Exorbitant custom support deal fees may not be the highest costs organisations running Windows XP will face after support ends in April.
Microsoft support for its Windows XP operating system (OS) ends on 8 April 2014. After this date, the software publisher will provide security updates until 14 July 2015.
Organisations still running Windows XP after April 2014 will have to pay substantial fees to Microsoft if they want a custom support contract, so what are the options for the company still running its business on the OS?
The fees for a custom support contract are anticipated to be significant. Although terms will depend on the particular deal struck with Microsoft, analyst organisation IDC predicts users can expect to pay $200 per PC per year for custom XP support in the first year, rising to $400 per PC in 2015 and $1,000 per PC in 2016.
Any business or public sector department running a large XP installed base will quickly see its IT budget eaten up by these significant support costs.
Analyst company Gartner estimates that more than 15% of mid-size and large enterprises will still have Windows XP running on at least 10% of their PCs after Microsoft support ends.
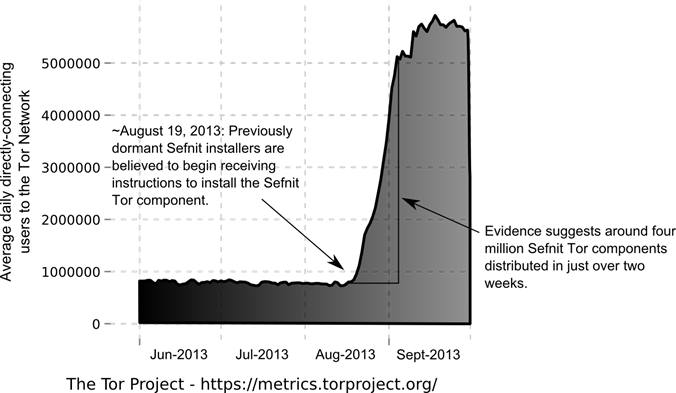
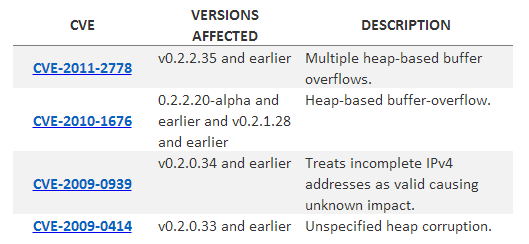
Security is the most pressing issue the IT department will face when XP support ends. Even after the SP2 release in 2004 – which hardened Windows XP – its security model was regarded as vastly inferior to Windows 7 and Windows 8.
In an organisation with 1,000 PCs, Citrix estimates that 9.1% will be compromised by XP security failings. When XP support ends, some experts believe the unsupported OS will become the target of increased attacks. The alerts published in Microsoft’s Patch Tuesday updates may act as a catalyst, spurring hackers to target vulnerabilities in XP.
Organisations’ reliance on XP
But why have IT departments left it so late to address the issue? Windows XP dates back to 2001. Microsoft stopped selling it in 2008, at which point the support clock began ticking. 7 April 2014 will be the last day Microsoft fully supports the OS. But at their launch, Windows XP and XP Professional OSs represented a concerted effort to deliver a consistent desktop OS for home and business users. Software providers were encouraged to create XP applications for the internet-ready OS. The Internet Explorer 6 (IE6) browser was built-in, enabling browser-based applications.
Gary Schare, president of Browsium – a company that makes browser emulation technology – says that, when XP came out in 2001, everyone had just completed Y2K and there was a big push to move to web technology, because people wanted to move from client server to web applications. They wanted to avoid lock-in but, according to Schare: “IE6 was super proprietary, and was tied to Windows.”
Commenting on a previous XP OS support article, one Computer Weekly reader noted: “It’s going to be XP for the next few years at least. The reason is simple. At least 60% of my apps don’t work on the newer flavours of Windows, and I really don’t feel like shelling out another couple of thousand to get the newer versions. What I have works, and I see no reason to line Microsoft’s pockets any more than I already have. Like a lot of others, I will migrate when, and only when, I have absolutely no other viable alternative.”
Another reader said he still ships hundreds of industrial XP boxes a year. “We’re getting XP licences under the Windows Embedded programme until at least December 2016. Microsoft could easily support XP for years until they produce something consumers actually want.”
Browser challenge and virtualisation
Clearly, some applications have been modernised to suit more recent OSs, such as Windows 7, but it has been the browser that has created the most problems for IT departments. Quocirca analyst Clive Longbottom points out that figures from sites that attract large numbers of hits from a broad range of users show that 5% of desktops worldwide remain on IE6, or approximately one in four of all desktops running XP.
A product such as Browsium Ion controls settings in a native browser to enable legacy apps to work. It injects Javascript to get around incompatibility.
Another option which may work in the interim, is to virtualise the XP environment, using a product such as Citrix XenDesktop to run virtual XP on top of a Windows 7 environment, or to build a hosted virtual desktop environment. So long as the virtual XP environment is not given free reign to access everything on the internet, this may prove a secure way to maintain access to certain core XP and IE6 applications that cannot be migrated.
“We are seeing people continue to virtualise XP applications and use AppDNA [a Citrix product to identify OS compatibility issues] to identify application compatibility,” says Jason Tooley, UK manager at Citrix. “We are seeing companies approaching the deadline with challenges of migrations that have effectively run out of time for a true migration to Windows 7/8. They will have to run XP applications in a Citrix virtual environment.”
IT departments can also run XP using Remote Desktop Services (RDS) on Windows Server 2003, which Microsoft will support until 7 April 2015, giving another year of support.
Citrix’s Tooley says some of the company’s XP customers have been running RDS on Windows Server 2003 using XenApp 4.5. “Our extended support dates for XenApp 4.5 – the version that supports WS2k3/R2 – aligns with Microsoft’s extended support dates.”
Mitigate security risk
If virtualisation is not practical, Gartner recommends IT departments segregate their corporate local area network, so the XP-based PCs effectively live on a private network. This will limit the extent to which a hacker can use a compromised XP machine to gain access to the wider corporate network.
What is clear from all the advice on running the unsupported XP OS is that the environment should be locked down, with a whitelist of authorised applications and kept in a known state, which enables the XP machine to be rebuilt easily. As one reader points out: “Knowing how your computer works is by far the most effective defence against security problems. Hiding things under ever more complex layers of software is a sure-fire way to get yourself stuck in a security pothole.”
So the issue fundamentally boils down to simplicity. A known environment is more secure than one where the user is free to download software from the internet – or indeed install anything else.
According to Gartner research vice-president Stephen Kleynhans, the strategy to keep XP secure will depend on the machines in question. “The key thing to do is limit the opportunities for new malicious code to get on those devices, then harden them so that, if they are exposed, there is some line of protection,” he says.
Like Y2K, 8 April 2014 represents a line in the sand for which the entire industry needs to prepare. “Generally, people know what they have to do,” says Kleynhans.
To harden the machine, ensure antivirus (AV) software is supported and up to date. Most big AV companies say they will support the XP OS for some time, but Kleynhans counsels organisations not to expect security support beyond 14 July 2015. During this time, users will probably get signature updates for new threats.
It is a lot of work and it may be as much work as converting to Windows 7. But the organization that has not paid attention to the implications of the end of support for XP is probably not the type of organization that is concerned about security.
The Licensing implications of virtualisation
Analyst firm Gartner warns that, while virtualisation certainly offers options for IT departments looking to circumnavigate problems arising from Microsoft’s end of support for XP, the software company considers virtualising the browser a violation to its licensing terms and conditions, so the IT department will need to check what is covered under its licence agreement.
Hosting IE6 or 7 in virtual desktop infrastructure is permitted. According to Citrix, putting an XP image in the XenClient Type-1 hypervisor, for example, and using the browser would work, but support for this ends very soon. Microsoft does not permit using App Streaming/App-V to isolate the browser in a package. Citrix says many thousands of users today use XenApp to publish IE6/7 for exactly this purpose and it does not break licensing rules.
Via: computerweekly