The UK is rushing through Parliament what it calls an emergency law that will ensure it retains access to people’s phone and internet records.
The BBC calls the rush job a “highly unusual move”, with the legislation set to take up a mere seven days, instead of the typical months-long consideration to which a bill would normally be subjected.
The Liberal Democrats (the smaller of the two political parties in the UK’s coalition government) had already successfully blocked plans for the earlier, similar, much-reviled Communications Data Bill – commonly known as the Snooper’s Charter.
The rush job for this new bill comes in response to the European Court of Justice’s (ECJ) having in April struck down an EU directive – the Data Retention Directive – that required telecoms to store the communications data of EU citizens for a minimum of six months and a maximum of two years.
That directive was introduced in 2006, after the London and Madrid bombings, to help fight organised crime and terrorism, but the ECJ ruled that it violated human rights.
The idea of the directive going away has been grating on the UK powers – particularly given that privacy advocates such as the Open Rights Group have recently been pushing service providers to start destroying data.
Prime Minster David Cameron, who’s reportedly secured the backings of all three major parties for the “emergency” Data Retention and Investigatory Powers Bill, says that if the collected data is deleted or no longer collected, “criminals and terrorists” are going to be tougher to go after.
Cameron says the emergency law will also “clarify” police and security services’ powers to bug suspects’ phones when they’ve got a warrant issued by the home secretary.
Some companies are already turning down requests to hand over data, he told the BBC:
Some companies are already saying they can no longer work with us unless UK law is clarified immediately.
Maybe Cameron has all three parties backing him on this new iteration of the snooper’s charter, but he’s still outraged some MPs, who said on Thursday morning that they hadn’t even seen the bill yet.
Labour MP Tom Watson, for one, said on Twitter that the new law will be “railroaded” through parliament next week:
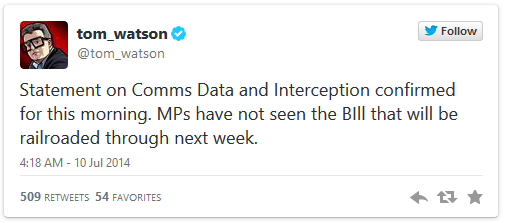
@tom_watson
Statement on Comms Data and Interception confirmed for this morning. MPs have not seen the BIll that will be railroaded through next week.
Meanwhile, privacy advocates are calling this so-called emergency a theatrical stunt.
Jim Killock, from the Open Rights Group, told the BBC that it’s neither terrorists nor paedophiles that have lit a fire under the government; rather, it’s the fact that groups like his are actually expecting telecoms to make good on the EJC’s ruling:
The government knows that since the ECJ ruling, there is no legal basis for making internet service providers retain our data, so it is using the threat of terrorism as an excuse for getting this law passed.
The government has had since April to address the ECJ ruling but it is only now that organizations such as ORG are threatening legal action that this has become an ’emergency’.
The emergency bill addresses collection of metadata, which can potentially include the time, duration, location, originator and recipient of phone or internet messages.
It does not, Cameron stressed, include legal obligations for telecoms to preserve content.
The bill does, however, also cover “legal intercept” rules, for when authorities are empowered to listen in on conversations.
In those circumstances, snooping authorities need a warrant, signed by either the foreign secretary, the home secretary, the secretary of state for Northern Ireland, the defence secretary or the cabinet secretary for justice for Scotland.
The emergency law includes a sunset provision: it will be ended in 2016, at which time government will have to look at it again.
Cameron stressed that the emergency bill isn’t granting powers that weren’t already there:
I want to be very clear that we are not introducing new powers or capabilities – that is not for this parliament. This is about restoring two vital measures ensuring that our law enforcement and intelligence agencies maintain the right tools to keep us all safe.
Nick Clegg, leader of the junior coalition Liberal Democrats party, said that the emergency bill is not just another snooper’s charter.
The differences between old and new legislation: the number of bodies able to obtain data from telecoms will be restricted, with some losing their access rights altogether and councils having to go through a single central authority, according to the Huffington Post.
The law doesn’t deal with communications interception and monitoring done by the UK’s intelligence agency, GCHQ.
The bill also includes measures meant to increase transparency and oversight. Beyond the sunset clause and the increased government scrutiny it entails, these measures also include:
- The creation of a new Privacy and Civil Liberties Oversight Board to scrutinise the impact of the law on privacy and civil liberties.
- Annual government transparency reports on how these powers are used, similar to those put out by Facebook, Google, Yahoo and other companies.
- The appointment of a senior former diplomat to lead discussions with the US government and internet firms to establish a new international agreement for sharing data between legal jurisdictions.
- A restriction on the number of public bodies, including Royal Mail, able to ask for communications data under the Regulation of Investigatory Powers Act (RIPA).
In spite of the government’s reassurances about most people being safe from having the actual content of their communications spied on, metadata of course provides ample details about even innocent people.
The Washington Post’s recent analysis of the US National Security Agency (NSA)’s surveillance shows that clearly: the paper found that 9 of 10 spied-on account holders weren’t intended targets of surveillance but were still swept up in the net cast to catch somebody else.
As critics pointed out about the earlier snooper’s charter, the system could be abused by law enforcement agencies that could conduct fishing expeditions rather than targeted surveillance against specific individuals.
In fact, Sir Paul Kennedy, the Interception of Communications Commissioner, told MPs at the time the bill was drafted that the law would justify investigating criminal infractions as mild as fly tipping – i.e., illegal dumping – and that setting a “crime threshold” would be difficult.
Top political figures in the UK tried to revive the snooper’s charter about a year ago, with spectacularly bad timing: smack in the middle of the earliest Snowden revelations about US surveillance.
Now, they’ve scaled back in an attempt, apparently, just to hang on to the snooping powers that the EJC decided were a violation of human rights.
Will the new bill present a more palatable approach to privacy? Will the wealth of data that the bill retains the right to amass still present an opportunity for the government to build profiles about individuals’ browsing or calling habits?
Will the amassed data still wind up in databases as a powerful lure for cybercrooks who might want to steal it so as to abuse private information or even to blackmail individuals – as in, we know when and how often you called so-and-so. What will you pay for that info not to get out?
Those were the objections to the snooper’s charter and the emergency bill is being given precious little time for those same concerns to be discussed.
Via: sophos