Apple really is listening, and doubly so!
The company backed down over the “foistware” U2 album that you recently received via iTunes, like it or not.
And later the same day, it announced that its two-step verification system would be applied to iCloud, effective immediately.
We’re delighted to hear it!
Bogus blame of iCloud in nude photo scandal
At the start of September 2014, a scandal broke when illegally-collected nude photos of 100 celebrities were published online.
Early rumours suggested that this might be down to some sort of iCloud “hack,” because at least some of the photos had been stolen from iCloud accounts, and because the photos all appeared at once, as though they had been grabbed as a job lot.
That turned out to be bogus reasoning.
The photos were apparently stolen from multiple sources in various ways, but released as a job lot by a collector.
He seems to have accumulated them in a series of underground trades and purchases.
So stolen, phished, keylogged and otherwise illegally acquired Apple ID passwords are a better explanation for the iCloud-related celebrity selfie breaches than a problem in iCloud itself.
→ Remember, re-used passwords make the problem worse: if you have one password for all your accounts, the crooks can breach any one of them and that’s that. So phishing your Gmail password would get them into iCloud, or vice versa.
Two-step verification
Apple’s response, as we reported at the time, was to urge iCloud users to turn on its two-factor authentication system, known as two-step verification (2SV).
2SV augments your password with a one-time login code sent via SMS:

Even a crook who knew your Apple ID password wouldn’t have enough to get into your account and restore your iCloud data onto his computer.
Also, if you were to see SMS verification codes popping up when you didn’t expect them, you’d have an early warning that someone was trying (and failing!) to breach your account
Huzzah for Apple, we thought.
2SV not enough
Except that 2SV didn’t apply to iCloud at all, as Naked Security writer Chester Wisniewski went out of his way to check.
Turning on 2SV only protected certain operations on your Apple account, such as editing your account details or buying products from iTunes or the App Store from a new computer or device.
So they ran a poll, asking whether Apple should change its mind and extend 2SV to iCloud.
The results were overwhelming:
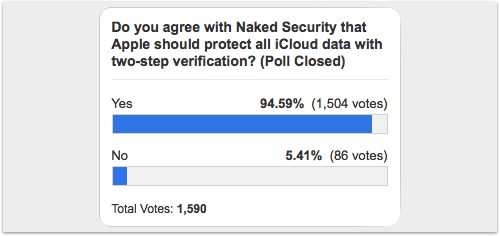
Nearly 95% of you said, “Yes.”
Apple pays attention
And Apple, it seems, was listening, sending out an email late yesterday Cupertino time (2014-09-16T018:00-7) to its 2SV users:
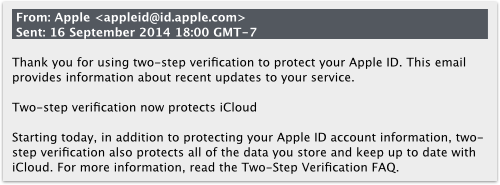
Thank you for using two-step verification to protect your Apple ID. This email provides information about recent updates to your service.
Two-step verification now protects iCloud
Starting today, in addition to protecting your Apple ID account information, two-step verification also protects all of the data you store and keep up to date with iCloud. For more information, read the Two-Step Verification FAQ.
The FAQ (which is article HT5570 in Apple’s knowledgebase) has been updated accordingly:
It now lists 2SV as applying when you:
- Sign in to My Apple ID to manage your account
- Sign in to iCloud on a new device or at iCloud.com
- Make an iTunes, App Store, or iBooks Store purchase from a new device
- Get Apple ID related support from Apple
2SV still not right
This is a good move, and we want to express public thanks to Apple for responding so quickly.
But we’ll also offer the opinion that the company still hasn’t got 2SV right.
Indeed, it’s a bit of a stretch for Apple to say that 2SV now “protects all of the data you store and keep up to date with iCloud” when, in fact, it only protects your very first login with a new device.
In other words, after you’ve signed in for the first time from your new iPhone, 2SV provides no further protection as you go about actually storing and keeping your data up to date.
In the same way that Apple’s 2SV can’t be turned on for every online purchase you make (why not?), it can’t be turned on for your actual data interactions with iCloud, such as kicking off a restore (why not?).
Allowing a stolen password alone to be used to pull down all your iCloud data, even if it’s being restored to your usual device, seems a huge waste of 2SV.
Trusted apps
Apple’s email also tells you that:
If you use iCloud with any third party apps such as Microsoft Outlook, Mozilla Thunderbird, or BusyCal, you can now generate app-specific passwords that allow you to sign in securely even if the app you are using does not support two-step verification.
. . .
App-Specific passwords will be required starting on October 1, 2014.
App-specific passwords (which effectively act as a pre-approved security bypass) are far from ideal.
But they do prevent crooks from bypassing your 2SV simply by choosing a login method that doesn’t support it.
Again, this is a good move, and hats off to Apple for setting a short deadline (October 2014) to enforce it.
The bottom line
Thanks to Apple for kicking off the process of adding 2SV to iCloud.
Your quick reaction is appreciated.
We urge iCloud users who live in one of the 59 supported countries to turn on 2SV sooner, rather than later, for the extra security it provides.
But please keep in mind: Apple has more work to do before 2SV truly “protects all of the data you store and keep up to date with iCloud”.
Via: sophos