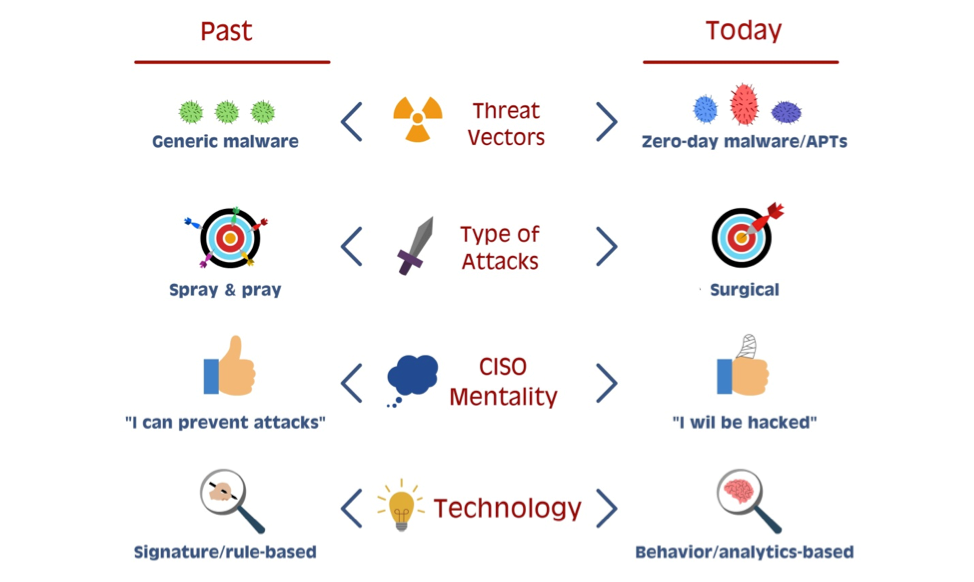
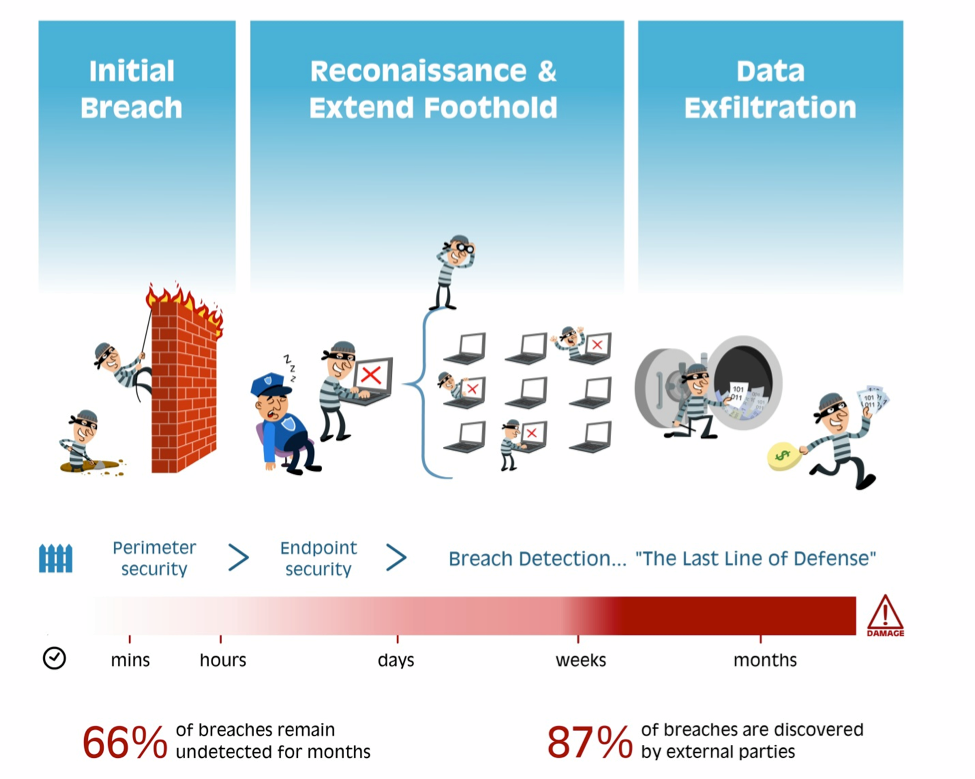
There’s fitness tracking and shopping tools, but no built-in GPS or Wi-Fi.
Apple’s latest “one more thing” was a doozy: A high-tech watch that CEO Tim Cook hopes will “redefine what people expect” from a wearable device. The watch does much more than tell the time — but what exactly does it do? And what can’t it?
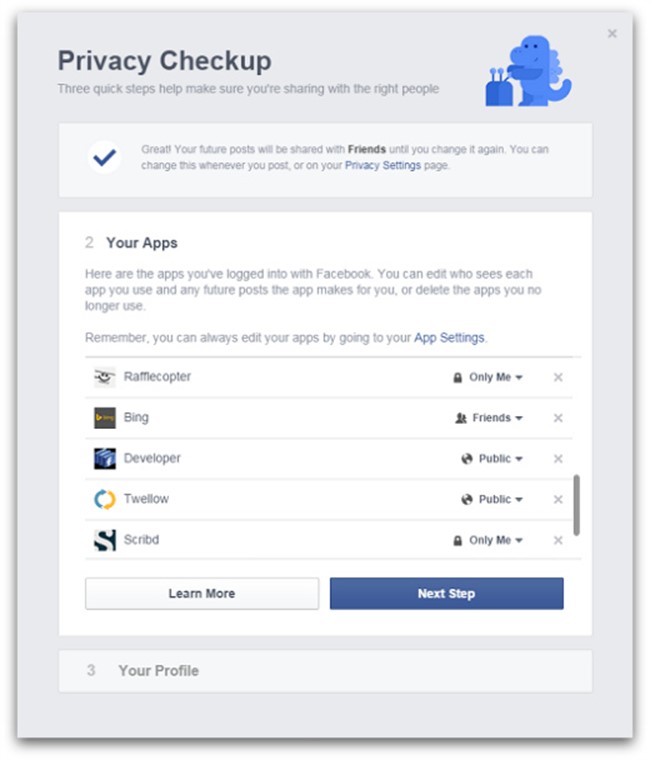
The US$350 Apple Watch is meant to be worn throughout the day and relies on its connection to an iPhone for much of its functionality. It can track health activity, communicate with friends and run a wide range of apps. It can even make retail payments.
Here are five things the Apple Watch can do, followed by five things it can’t.
1. Messaging and calling. There’s a variety of ways to communicate with the device: Users can send and receive messages by dictating them or selecting from preset options. There’s a built-in speaker and microphone for phone calls — though it seems those calls have to go through an accompanying smartphone and not directly from the watch to a network. Users can silence incoming calls by covering the watch with their hand. There’s also a new way to communicate called “digital touch,” which lets people draw on the watch’s screen and send the image to friends, almost like a Snapchat doodle.
2. Siri. Apple’s personal assistant can be accessed on the watch by saying, “Hey, Siri,” or holding down the crown (the winder on a regular watch) on the side of the device. With Siri, users can dictate messages to friends, get turn-by-turn directions or perform local searches, like for movie times.
3. Fitness tracking. Apple says the watch can help people lead healthier lives, by letting them set goals within apps or tracking their physical activity using built-in sensors. There’s an accelerometer like in a smartphone, and a heart-rate sensor that uses infrared and visible-light LEDs and photodiodes. The Watch’s Activity app will graph data like calories burned or how long you’ve been standing up. Its Workout app provides more granular information for specific activities like running and cycling. Meanwhile, the companion Health app on the iPhone will let people share the data with third-party health and fitness apps.
4. Shopping. One of the more intriguing features is that the watch supports Apple Pay, a new system intended to replace debit and credit cards for making purchases. It’s based on NFC, or near field communication technology, which is already in some Android smartphones but not Apple’s. Visa, Master Card and Amex card holders will be able to keep their card information on file with Apple, and Apple will create a device account number for each card that’s stored in a Secure Element chip. Watch wearers will then be able to buy items by double clicking the button under the crown and waving their wrist in front of special in-store readers. Apple says its working with Macy’s, McDonald’s and lots of other stores to have the readers installed.
5. Apps. The Apple Watch has a brand new interface that displays apps as small, circular icons. The watch uses what Apple calls a “taptic engine” for alerts and app notifications, so it will vibrate or “tap you on the wrist” when they come in. There’s a range of on-board apps like calendar, Maps, photos, and music. Users can control music on their iPhone from the watch, and music can also be played directly from the watch, though it’s unclear how much storage the watch has. The WatchKit tools will let developers build more apps for the device.
The Apple Watch, clearly, packs a lot of features into a small package. But here are five things it doesn’t have:
1. Universal compatibility. Many of the watch’s functions, like receiving calls and emails, require it to be paired with an iPhone. As of now the watch will only work with the new iPhone 6 and 6 Plus, as well as the 5, 5C and 5S. There’s also no reason to think it will work with Android and Windows phones.
2. A keyboard. To send messages, they must be dictated into the microphone or selected from pre-set responses. This is similar to how smartwatches powered by Google’s Android Wear system currently work. Apple says the watch is smart enough to analyze incoming messages and display the appropriate responses that can be sent back.
3. It’s own camera. The Watch can display favorite photos from a Mac or iPhone, but it doesn’t have its own built in camera. It can be used as a remote viewfinder, however, for the camera on your phone. And you can use the watch to snap the photo or set the timer on the camera’s phone.
4. Built-in GPS and Wi-Fi. For that, you need to be connected to your iPhone. If you go out for a bike ride, or do some other activity that can’t be measured in steps with the accelerometer, the Watch can’t track your distance without your phone.
5. One important thing the Apple Watch doesn’t have yet is a firm launch date. Apple said the watch would be available in “early 2015,” but it did not clarify beyond that.
Via: itworld