Mozilla is the latest vendor, if you will excuse me not referring to it as a foundation or a community, to announce a walled garden for its software ecosystem.
In the second half of 2015, it says, Firefox will require all browser extensions to be digitally signed.
The purpose should be obvious: to make it harder for surreptitious, devious or plain malevolent add-ons to make their way into your browser unnoticed.
Extensions can adapt the behavior of Firefox significantly, from rewriting links and content, through keeping tabs on where you browse, to reading and using your data.
As a result, malicious extensions can be as bad for your digital health as a full-blown malware infection at the operating system level.
How it will work
Mozilla will be the signer-in-chief, and that, apparently, will be that.
If you publish your extension via Mozilla’s equivalent of the App Store, known as AMO, or addons.mozilla.org, the company will automatically vet it, sign it, and make it available for download.
That’ll be a bit like Google’s Bouncer, the automatic process that decides if your Android app is safe for inclusion on Google Play.
The good side of an automatically-scan-approve-and-sign process is that it’s simple and fast.
That makes it vaguely more egalitarian than a complex and bureaucratic mechanism that tends to favor bigger, more established software makers, who themselves have the staff and bureaucracy to match.
The bad side is that automatic systems for software approval are designed as much to help online software markets grow really quickly as they are to keep the crooks out.
So they don’t always do a very good job of security, and if completely automatic approval systems do let malware or dodgy programs through, they give a powerful but completely false sense of safety that plays straight into the hands of the crooks.
Going off market
Like Google on Android, but unlike Apple on iOS, Mozilla will continue to allow its users to shop “off market,” so you won’t be forced to publish your extensions via AMO.
Unlike on Android, however, this won’t require users to invoke an “allow unsigned extensions” option.
In fact, Mozilla says that there will be no way, neither via command line nor through configuration options, to suppress signature checking.
Instead, all extensions will have to be signed, even “off-market” ones, so instead of devolving the responsibility for off-market content onto the user, Mozilla is going to require developers to make the effort.
→ Apparently, there will be a special sort of exception for in-house extensions, to appease Mozilla’s corporate users. How this will work, and how it will be locked down to prevent malware abusing it as a backdoor, is not yet clear. Presumably you’ll be able to instruct your company browsers to accept extensions signed with a company certificate.
What isn’t clear is how developers will test their extensions under the current Release version before submitting them for approval.
Mozilla says:
Installation of unsigned extensions will still be possible on Nightly and Developer Edition, as well as special, unbranded builds of Release and Beta that will be available mainly for developers testing their extensions.
This, of course, raises the question, “Will the unbranded or the Developer builds be sufficiently similar to the Release versions out in the real world that developers can stand by their testing results?”
It also makes you wonder, “How many users, including businesses, will simply switch to the unbranded versions themselves and be done with this code signing hassle?”
The community strikes back
Security and reliability concerns, however, don’t seem to be what’s worrying some of the more vocal members of the Mozilla community, who have already hit back with comments like this emotive piece:
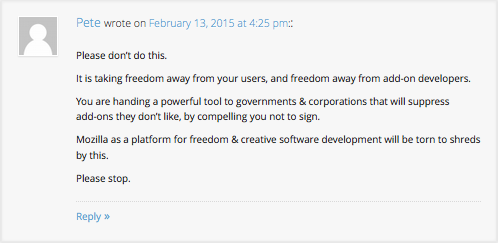
Please don’t do this.
It is taking freedom away from your users, and freedom away from add-on developers.
You are handing a powerful tool to governments & corporations that will suppress add-ons they don’t like, by compelling you not to sign.
Mozilla as a platform for freedom & creative software development will be torn to shreds by this.
Please stop.
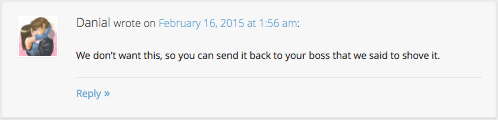
We don’t want this, so you can send it back to your boss that we said to shove it.
Mozilla has certainly set the cat amongst its own community’s pigeons.
At this stage, it’s not even clear if the organization is going to be able to please some of the people some of the time.
Via: sophos