Remember BlueBorne?
A series of recently disclosed critical Bluetooth flaws that affect billions of Android, iOS, Windows and Linux devices have now been discovered in millions of AI-based voice-activated personal assistants, including Google Home and Amazon Echo.
As estimated during the discovery of this devastating threat, several IoT and smart devices whose operating systems are often updated less frequently than smartphones and desktops are also vulnerable to BlueBorne.
BlueBorne is the name given to the sophisticated attack exploiting a total of eight Bluetooth implementation vulnerabilities that allow attackers within the range of the targeted devices to run malicious code, steal sensitive information, take complete control, and launch man-in-the-middle attacks.
What’s worse? Triggering the BlueBorne exploit doesn’t require victims to click any link or open any file—all without requiring user interaction. Also, most security products would likely not be able to detect the attack.
What’s even scarier is that once an attacker gains control of one Bluetooth-enabled device, he/she can infect any or all devices on the same network.
These Bluetooth vulnerabilities were patched by Google for Android in September, Microsoft for Windows in July, Apple for iOS one year before disclosure, and Linux distributions also shortly after disclosure.
However, many of these 5 billion devices are still unpatched and open to attacks via these flaws.
IoT security firm Armis, who initially discovered this issue, has now disclosed that an estimated 20 million Amazon Echo and Google Home devices are also vulnerable to attacks leveraging the BlueBorne vulnerabilities.
If I split, around 15 million Amazon Echo and 5 million Google Home devices sold across the world are potentially at risk from BlueBorne.
Amazon Echo is affected by the following two vulnerabilities:
- A remote code execution vulnerability in the Linux kernel (CVE-2017-1000251)
- An information disclosure flaw in the SDP server (CVE-2017-1000250)
Since different Echo’s variants use different operating systems, other Echo devices are affected by either the vulnerabilities found in Linux or Android.
Whereas, Google Home devices are affected by one vulnerability:
- Information disclosure vulnerability in Android’s Bluetooth stack (CVE-2017-0785)
This Android flaw can also be exploited to cause a denial-of-service (DoS) condition.
Since Bluetooth cannot be disabled on either of the voice-activated personal assistants, attackers within the range of the affected device can easily launch an attack.
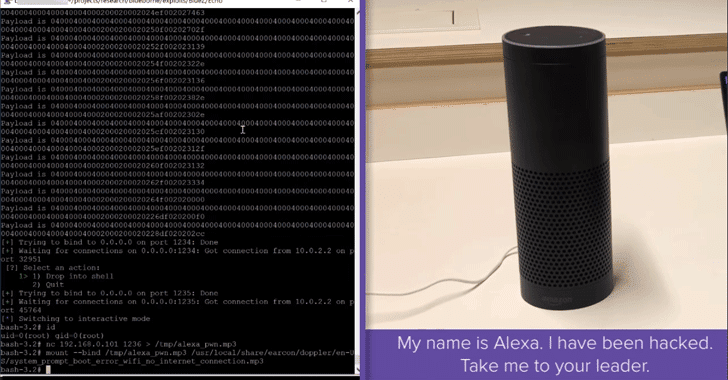
Armis has also published a proof-of-concept (PoC) video showing how they were able to hack and manipulate an Amazon Echo device.
The security firm notified both Amazon and Google about its findings, and both companies have released patches and issued automatic updates for the Amazon Echo and Google Home that fixes the BlueBorne attacks.
Amazon Echo customers should confirm that their device is running v591448720 or later, while Google has not made any information regarding its version yet.
via: thehackernews