Hope here to present a simple, dumbed-down, step-by-step article on how to get these updates and navigate Microsoft’s overly complicated announcement.
There are four Microsoft help pages that we used to compile this information, which you may also want to read, just in case:
1) Guidance for Windows desktop users
2) Guidance for Windows Server users
3) Security advisory ADV180002 (contains KB numbers for update packages)
4) Update compatibility warning for users with third-party anti-virus software
The key and most important sentence on all these pages is:
To help prevent stop errors caused by incompatible anti-virus applications, Microsoft is only offering the Windows security updates released on January 3, 2018 to devices running anti-virus software from partners who have confirmed their software is compatible with the January 2018 Windows operating system security update.
What does this mean?
It means that if you go to the Windows Update section of your Windows operating system and you press “Check for updates,” if something comes up, you’re safe to install it.
Windows update packages (KB numbers) are available here. A different KB number will appear, depending on your operating system and hardware platform.
If nothing comes up, that means Windows has detected the presence of an incompatible anti-virus (AV) application on your system.
The whole mess with anti-virus programs
Microsoft says that during tests, it detected some anti-virus programs causing BSOD crashes that prevented computers from booting after the installation of the Meltdown and Spectre patches.
The company says it instructed anti-virus vendors to modify their products and create a registry key on customers’ computers when they’ve confirmed or updated their products so not to crash Windows PCs post-Meltdown/Spectre updates.
Microsoft says that currently, whenever users want to update Windows, its update system will check for that registry key on users’ PCs.
If the key exists, the Windows update process will believe the anti-virus software received an update to support the Meltdown and Spectre patches, and install the proper OS updates as well.
This is where things get messy. Some AV companies have said they don’t plan to create that registry key, some said they cannot “technically” create that key, while others will ship updates in the following days.
This Google Docs file contains a list of the responses from some AV companies.
In simple terms, most AV users will have to wait, as most AV companies have promised to update their products and automatically add the registry key.
The simplest way to go about this is if you can go to the Windows Update section every day and press the “Check for updates” button and you’ll receive the update after your AV product creates that registry key.
If you’re one of the unlucky souls whose AV company doesn’t plan to add that registry key, this is a .reg file Bleeping Computer put together to automatically create the following registry key for you.
Key="HKEY_LOCAL_MACHINE" Subkey="SOFTWARE\Microsoft\Windows\CurrentVersion\
QualityCompat" Value="cadca5fe-87d3-4b96-b7fb-a231484277cc" Type="REG_DWORD”
We’ll display this in red so it sticks out. Do not run the .reg file unless you’ve confirmed with your AV vendor that they’re compatible with the Meltdown andSpectre patches.
Once you’ve run the file or added the registry key manually, your PC will receive the patches for the Meltdown and Spectre vulnerabilities.
How can you check the status of the patches?
Microsoft has also released a set of Powershell one-liners that you can use to check if your PC installed the updates properly, or if you need additional firmware updates.
When starting PowerShell, make sure you start it with Admin privileges so that you can install the required modules.
The Powershell command below will download and install a Powershell module for testing for the Meltdown and Spectre flaws.
Install-Module SpeculationControl
If you run the command and get execution errors, you might need to adjust your Powershell execution policy. Run the following command:
Set-ExecutionPolicy Bypass
Now, you know can run a second Powershell command that actually checks your system:
Get-SpeculationControlSettings
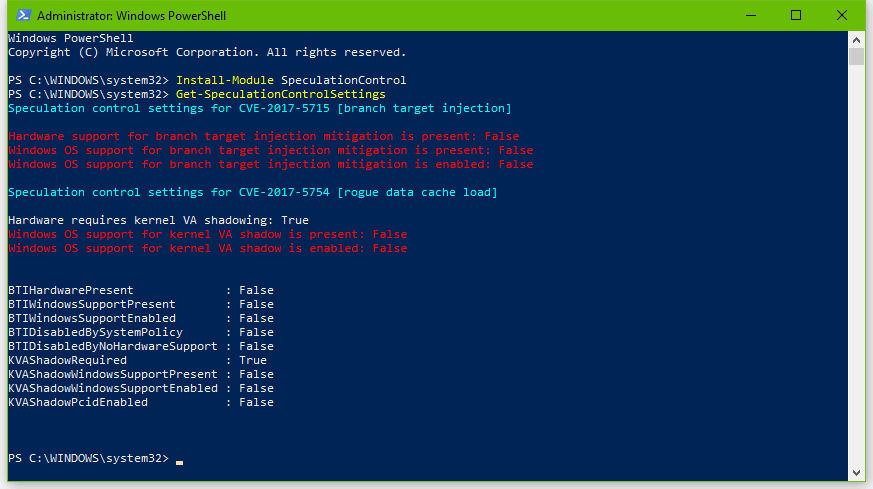
Google says that not all CPUs are vulnerable to the Meltdown and Spectre flaws, but if the result will look like this, with lots of red-colored text, then you’re CPU and OS are vulnerable to these attacks. Most likely, it looks like this.
The next step is to press the “Check for updates” button until you receive a Meltdown/Spectre patch. As explained above, this might take a few days for some users with “problematic” anti-virus software.
After the updates, you’ll need to run the Get-SpeculationControlSettings again. There are two possible scenarios.
The most common scenario is the following result:
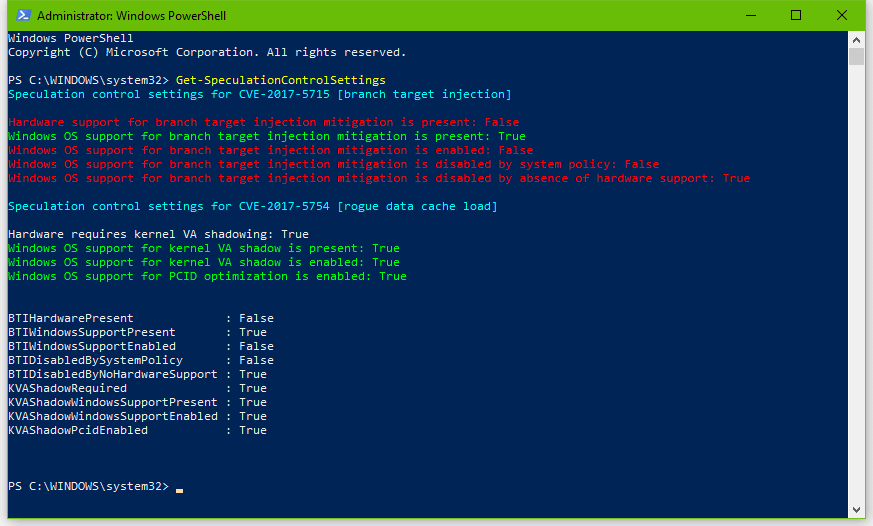
The image means that your system received patches for the Meltdown bug, but has received incomplete patches for the Spectre bug.
This was to be expected, as Google said yesterday that Spectre is harder to exploit, but also harder to patch.
What the red text means is that you need additional chipset firmware updates. Microsoft and Google say that OEMs will need to provide users with these additional firmware updates to complete the Windows OS-level Spectre patches. Depending on your computer’s age, some OEM might not make these firmware updates available, meaning you’ll be stuck with an incomplete Spectre patch.
If your laptop/desktop/server vendor has provided extra chipset firmware updates, you can get them from their official sites, install them, and complete the patch.
If everything is OK, all checks will appear in green-colored text, like so:
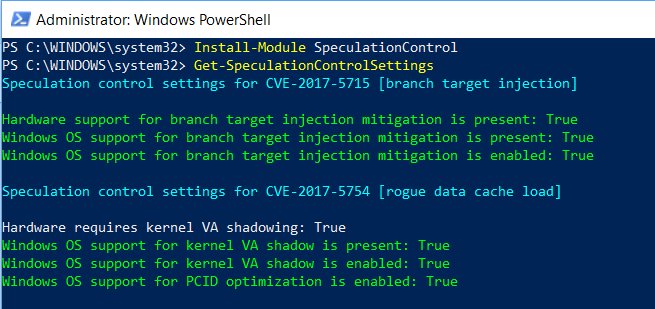
When the output is all green and each item is set to True, as shown above, then you are now protected from these attacks.
Once you’re done, remember to set the Powershell execution police back to a restricted mode, which may be useful in mitigating malware attacks that use Powershell to run malicious commands.
via: bleepingcomputer