Fancy earning $100,000? Of course, you do.
Well, now there’s an opportunity to earn a huge reward if you can demonstrate how Adobe Flash can be exploited.
Sounds good right? Well, here’s the bad news for the rest of us: it’s not Adobe offering the money in the form of a bug bounty.
Less than a month ago, Adobe proudly announced a series of security enhancements it had made to bolster the defences of Flash, following a year’s worth of collaboration with security researchers at Microsoft and Google’s Project Zero team:
One example of a larger scale collaboration is our heap isolation work. This project initially started with a Project Zero code contribution to help isolate vectors. Based on the results of that release and discussions with the Microsoft research team, Adobe then expanded that code to cover ByteArrays. In last week’s release, Adobe deployed a rewrite of our memory manager to create the foundation for widespread heap isolation which we will build on, going forward. This change will limit the ability for attackers to effectively leverage use-after-free vulnerabilities for exploitation.
Considering how many computers continue to run Flash Player, and the regularity with which criminals attempt to exploit vulnerabilities in its code, Adobe’s announcement sounded like positive news.
But there are, inevitably, people keen to bypass the heap isolation defence now built into the latest versions of Adobe Flash.
And thus it was perhaps not surprising to see controversial vulnerability broker Zerodium make an announcement offering a significant financial reward via its Twitter account:
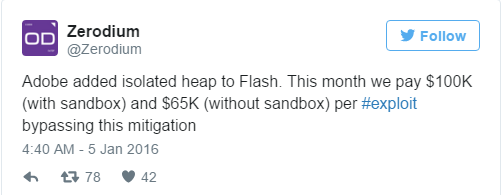
There’s a big problem with all of this, of course. And that’s that unless you have piles of cash in the bank, Zerodium hsa no intention of sharing details of any exploit (and how to protect against it) with you. In fact, there’s every likelihood that Zerodium will not be sharing it with Adobe either.
And if Adobe don’t get told about the vulnerabilities in Flash, they’re not going to get patched.
Instead, Zerodium believes that it will be able to make a healthy profit selling details of the $100,000 vulnerabilities to whoever is prepared to stump up a considerable amount of cash. Likely buyers include intelligence agencies who might use the code to spy upon foreign governments, military contractors and overseas companies.
And it’s obviously not in the interest of such purchasers to make details of any zero-day flaw public, as it would warn their intended targets of the potential threat.
We all know that Adobe Flash has been plagued with security problems over the years. Whatever advances Adobe makes, Flash will continue to be probed and dissected by those keen to find vulnerabilities and ways of exploiting them.
The sad news is that Adobe may not be told about flaws which are found – which can only be bad news for the rest of us, left without protection.
Via: tripwire




Leave a Reply