‘SlowLoris’ flaw could see a mouse of a machine take down an elephant of a server.
An SMBv1 bug described late last week at DEF CON won’t be patched, because Redmond says it only needs a suitable block on connections coming from the Internet.
The 20-year-old bug was discovered by two RiskSense researchers combing code for vulnerabilities exposed by the NSA’s EternalBlue exploit.
After it landed, Twitter user @JennaMagius detailed what happens in a longish Twitter-thread, saying that the bug offers an easy vector to hose big web servers with small computers (all the way down to a Raspberry Pi).
However, it only works if the target machine has SMBv1 exposed to the Internet, and for that reason, Microsoft doesn’t see it as demanding an immediate patch.
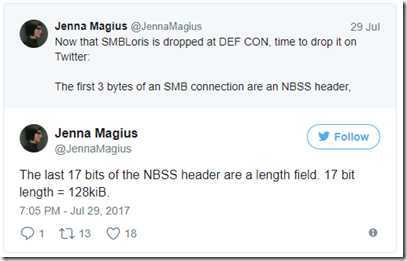
SMBLoris is a memory handling bug, @JennaMagius explained on Twitter, associated with two non-paged allocations that use physical memory and can’t be swapped out – so it’s trivial to fill a target Web server’s memory.
NBSS is the NetBIOS Session Service protocol, and a connection to it allocates 128kB of memory that’s only freed when the connection is closed (after 30 seconds if the attacker opens it but then does nothing). At one connection per TCP port (there are 65,535, @JennaMagius explains), the attacker can fill up more than 8 GB.
If they launch the attack on IPv4 and IPv6, that rises to 16 GB, and if an attack comes from just two IPs, they can fill 32 GB, and so on. Eventually, the target can’t allocate memory for NBSS and needs a manual reboot.
RiskSense researchers Sean Dillon and Zach Harding chatted to Kaspersky’s Threatpost about the bug before their DEF CON talk.
Noting a similarity to the old 2009 Slowloris bug, Dillon said:
“Similar to Slowloris, it requires opening many connections to the server, but these are low-cost connections for the attacker, so a single machine is able to perform the attack.”
In response to Microsoft saying it didn’t intend patching, Dillon said “The reason they say it’s a moderate issue is because it does require opening many connections to the server, but you could do it all from a single machine, and a Raspberry Pi could take down the beefiest server”.
via: theregister




Leave a Reply