Encrypted storage, malware scanners, missing-phone-finders and more: Here are 20 apps to help protect your smartphone, your privacy and your data.
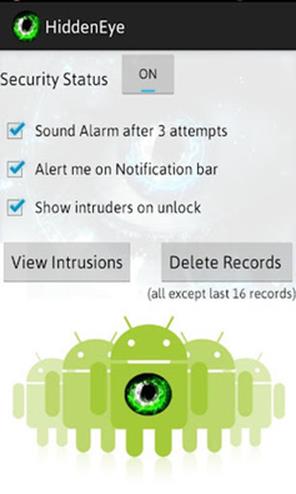
HiddenEye
HiddenEye Plus uses your smartphone’s camera in self-defense: This app photographs any person who tries to unlock your phone.
Available for: Android
Cost: Free

Kryptos
Kryptos uses 256-bit AES encryption to encrypt voice communications before transmission (using 2048 bit RSA for key exchange). Provides VoIP connectivity for secure calls over 3G, 4G and WiFi.
Available for: Android and iPhone
Cost: Free to download, monthly service fee of $10
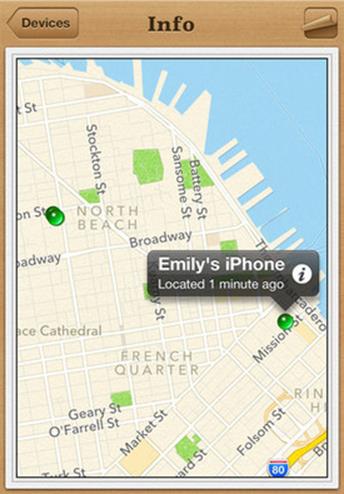
Find my iPhone
If you misplace your iPhone, the Find My iPhone app will let you use another iOS device to find it and protect your data. Locates the missing device on a map, plays a sound, displays a message, remotely locks the device and/or erases all the data on it.
Available for: iPhone
Cost: Free

SeekDroid
SeekDroid (similar to Find My iPhone) allows the user to locate a lost or stolen Android device. Features device location on a map, remote audible alarm, remote wiping of the device, remote tracking and GPS.
Available for: Android
Cost: $2.99
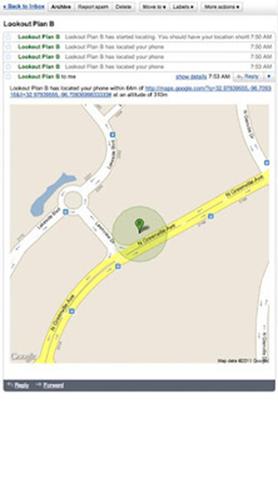
Plan B
Plan B is a find-my-phone app that you download AFTER you lose your phone. Described as a “last resort” to find a missing phone, allows the user to locate their lost device using cell towers and GPS. On some phones, Plan B can switch GPS on automatically.
Available for: Android
Cost: Free
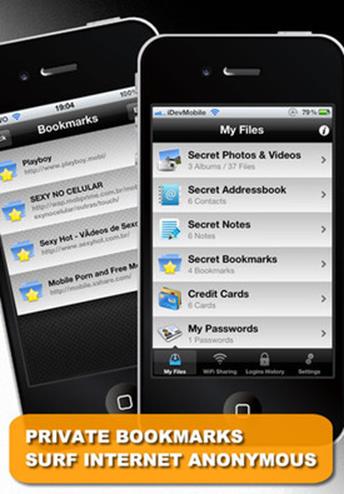
Secure Folder PRO
A private storage solution for photos, videos, contacts, notes, credit cards and passwords. Features secret website bookmarks and private navigation system without history tracking, a “decoy” storage area to trick nosy intruders, and encrypted storage for credit card and other data.
Available for: iPhone
Cost: $1.99
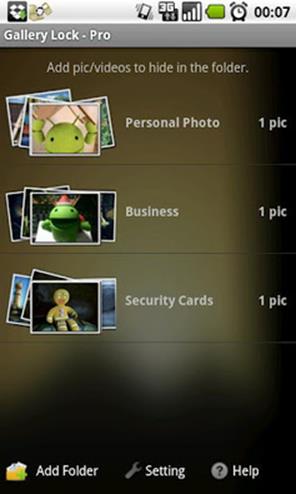
Gallery Lock
Gallery Lock provides privacy for picture and video files by hiding them in individual, password-protected folders.
Available for: Android
Cost: Free

Privacy Filter
Privacy Filter blocks the screen from prying eyes glancing at the device from the side.
Available for: Android
Cost: $1.99
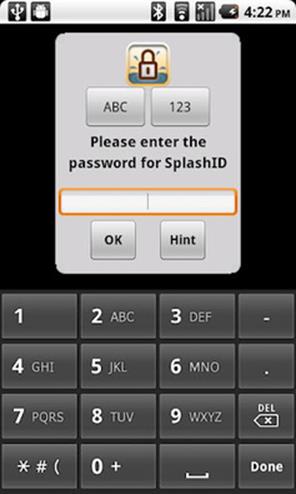
Splash ID Safe
A sensitive-data vault that stores personal information (such as web logins, credit cards, PINs, and email settings) using 256-bit encryption.
Available for: Android
Cost: $9.99
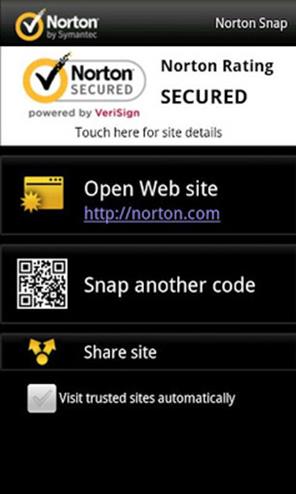
Norton Snap
Norton Snap is a QR code scanner that warns the device user about dangerous QR codes, and blocks unsafe Web sites before they load on the device.
Available for: Android and iPhone
Cost: Free
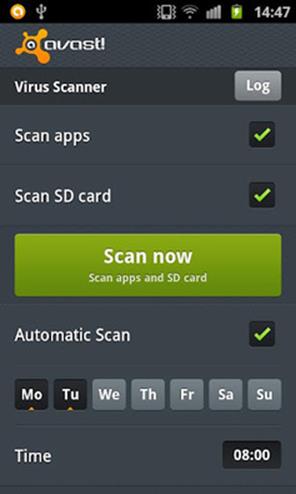
Avast Free Mobile Security
Famous from the PC space, Avast also offers this antivirus and anti-theft Android security application. Includes scanning of installed apps and memory card content on demand. Also features a privacy report, which scans and displays access rights and intents of installed apps, as well as anti-theft components that give the user remote control via SMS or Web to lock, locate, siren, memory or wipe the device.
Available for: Android
Cost: Free
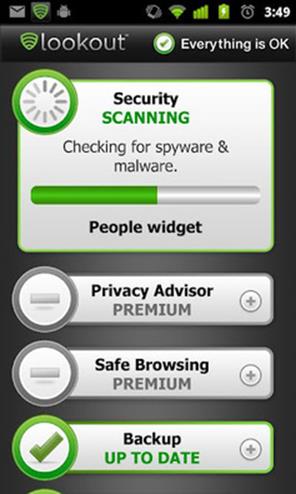
Lookout Mobile Security
The Android version of this app includes antivirus and blocks malware, spyware, and trojans and scans each app downloaded. Both the Android and iPhone versions feature a find-my-phone component, which locates a lost or stolen phone on a Google map and activates a loud alarm, even if the device is on silent.
Available for: Android, limited version for iPhone
Cost: Free

AVG Mobilation Antivirus
AVG’s version of antivirus for smartphones detects harmful apps and text messages. Features include scanning of apps, settings, files, and media in real time, location of lost or stolen phone via Google Maps, lock and wipe device to protect privacy.
Available for: Android
Cost: Free
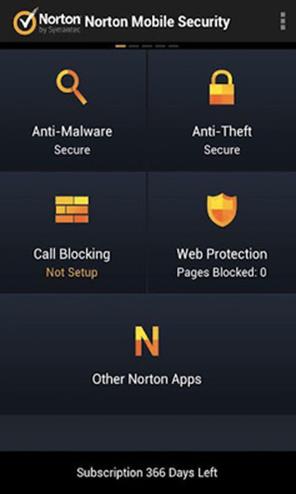
Norton Mobile Security
Security, antivirus, antitheft protection. Includes automatic antivirus scan for downloaded apps and app updates, keystroke logging protection, remote lock and wipe, find-my-phone phone locator, and a “scream” locator that lets the user send a text to the missing phone, which sets off a scream alarm.
Available for: Android
Cost: Free

NQ Mobile
Security and antivirus protection against from virus, malware, spyware, trojans and phone hacking. Features include: antivirus, anti-harassment, privacy protection, phone locator, data backup, safe browsing and traffic.
Available for: Android
Cost: Free
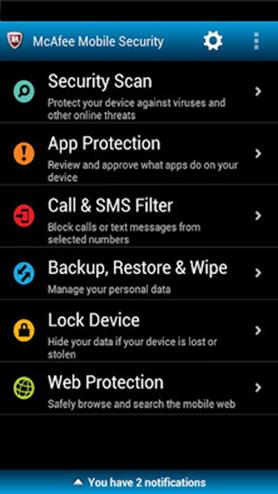
McAfee Mobile Security
McAfee’s version of protection for the Android; features antivirus, anti-theft, safe mobile surfing, app protection and call and SMS filter. Other features include remote device lock, locate and track.
Available for: Android
Cost: Free trial
Accellion Mobile
Allows business users to work on enterprise content by providing secure mobile access to files. Features: Securely browse, view, edit, save back, upload, send, and share files and folders on-the-go. Participate in real-time collaboration by opening, editing, and saving back Microsoft Office file types through Quickoffice.
Available for: Android and iPhone
Cost: Free
Junos Pulse
Junos Pulse secures connectivity to corporate web-based applications via Juniper Networks SSL VPN gateways. Also delivers mobile security against malware, viruses, and spyware, as well as from device loss or theft, preventing device damage, and loss and exploitation of sensitive user or corporate data.
Available for: Android and iPhone
Cost: Free
Accellion Mobile
Allows business users to work on enterprise content by providing secure mobile access to files. Features: Securely browse, view, edit, save back, upload, send, and share files and folders on-the-go. Participate in real-time collaboration by opening, editing, and saving back Microsoft Office file types through Quickoffice.
Available for: Android and iPhone
Cost: Free
Junos Pulse
Junos Pulse secures connectivity to corporate web-based applications via Juniper Networks SSL VPN gateways. Also delivers mobile security against malware, viruses, and spyware, as well as from device loss or theft, preventing device damage, and loss and exploitation of sensitive user or corporate data.
Available for: Android and iPhone
Cost: Free
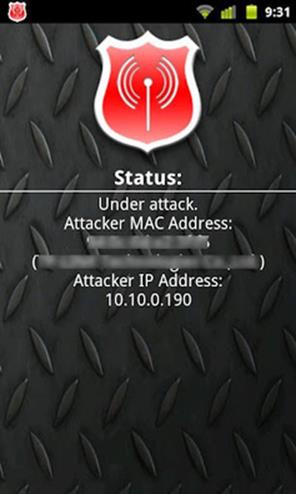
WiFi Protector
Guards against WiFi sniffing attacks by detecting Address Resolution Protocol (ARP)-related attacks, such a DDOS (Denial Of Service) or MITM (Man In The Middle). Protects the phone from tools like FaceNiff, Cain & Abel, ANTI, ettercap, DroidSheep, NetCut, and others that try to hijack sessions via “Man In The Middle” through ARP spoofing / ARP poisoning.
Available for: Android
Cost: $3.89
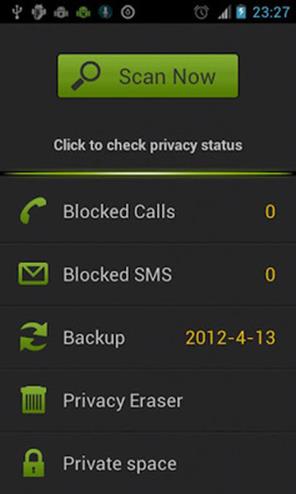
Privacy Safe
Automatically moves confidential SMS and call logs from private contacts into private space and hides the normal track on your phone. Notifies of private space status secretly. Private space is password protected. Also blocks unwanted SMS using keywords specified by the owner.
Available on: Android
Cost: Free
Via: csoonline