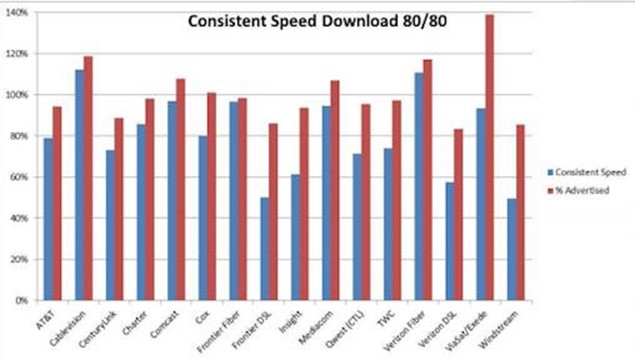
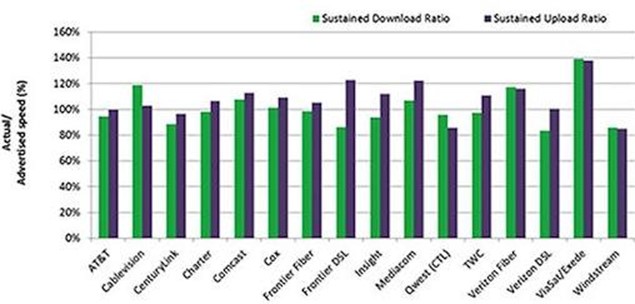
The German government is to end a contract for internet services with US-based telecoms firm Verizon over concerns of snooping by the US National Security Agency (NSA).
The decision highlights the impact controversial US government surveillance programmes are making on US technology firms.
Verizon has provided internet services to a number of German government departments and the current contract was due to run until 2015, reported the BBC.
Earlier this month, Germany announced an investigation into allegations by whistleblower Edward Snowden, that US spy agencies bugged chancellor Angela Merkel’s phone.
Verizon had not been implicated, but the allegations have put pressure on US technology firms doing business in Europe.
“There are indications that Verizon is legally required to provide certain things to the NSA, and that’s one of the reasons the co-operation with Verizon won’t continue,” said German interior ministry spokesman Tobias Plate.
“Furthermore, the ties revealed between foreign intelligence agencies and firms in the wake of the US National Security Agency affair, show that the German government needs a very high level of security for its critical networks,” he said.
In response to the German government’s decision, Verizon Germany’s managing director Detlef Eppig said in a statement: “Verizon Germany is a German company and we comply with German law.”
Transparency efforts
In an attempt to head off the impact of the Snowden revelations, Verizon published a transparency report in January 2014 outlining the number of law enforcement requests for customer information.
According to the report, Verizon received no demands from the US government for data stored in other countries during 2013.
Through the company’s policy blog, Verizon also attempted to dispel “persistent myths and questions” about the US government’s ability to access customer data stored in cloud servers outside the US.
“Our view on the matter is simple: the US government cannot compel us to produce our customers’ data stored in data centers outside the US and, if it attempts to do so, we would challenge that attempt in court,” the company said.
The blog post concludes by saying: “Whatever interpretations others may apply to US law, we want our position on the matter to be clear: there should be no concern about the US government compelling Verizon to disclose data our customers store in Verizon datacentres outside the US.”
Facebook’s legal fight
Facebook, in a similar attempt to distance itself from US government snooping, this week published a blog detailing the social networking firm’s efforts to fight bulk search warrants in court.
“Since last summer, we’ve been fighting hard against a set of sweeping search warrants issued by a court in New York that demanded we turn over nearly all data from the accounts of 381 people who use our service, including photos, private messages and other information,” said Chris Sonderby, Facebook deputy general counsel.
“This unprecedented request is by far the largest we’ve ever received—by a magnitude of more than ten—and we have argued that it was unconstitutional from the start.”
Sonderby said US government gag orders had prevented Facebook from discussing this case and notifying any of the affected people until now.
He said Facebook had complied with the order only after losing a “forceful” legal challenge.
Sonderby said Facebook is continuing its efforts to invalidate these “sweeping warrants” and to force the government to return the data it has seized and retained.
“We recognise that law enforcement needs to investigate potential crimes, but we believe all government data requests must be narrowly tailored, proportionate to the case and subject to strict judicial oversight,” he said.
Germany has led European opposition to privacy infringement by US technology firms, with its strict privacy laws presenting challenges to US firms such as Google and Facebook.
Germany has also proposed building European networks to enable citizens to avoid relying on US firms.
Via: computerweekly