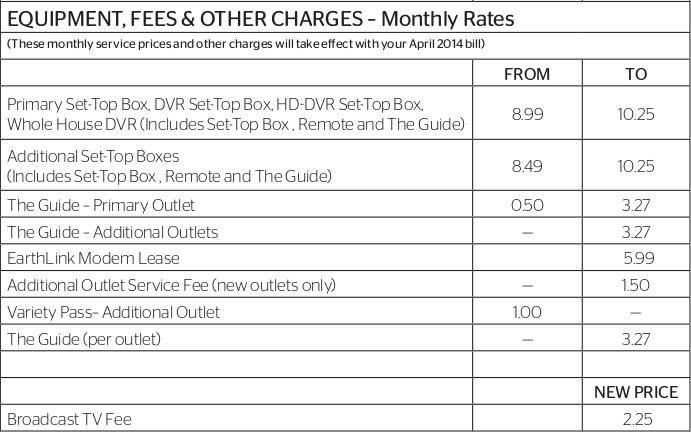
Justice Department Has Charged Nearly 900 for Claiming Bogus Refunds.
With tax season under way, federal authorities are stepping up efforts to stop what they call a growing problem of fraudulent filings seeking tax refunds based on stolen identities.
The scam, which involves repeatedly filing fake tax returns electronically and receiving refunds within days, is so enticing it is attracting suspects not typically associated with white-collar crime.
On Friday, two members of an alleged crack-dealing gang in Miami were indicted on charges they also ran a tax-refund scam on the side. Suspects typically steal lists of names and Social Security numbers. Then they file large numbers of electronic returns claiming refunds, and can start getting money before investigators spot the fraud.
Identity fraud tax refund crimes are partly an outgrowth of the more recent ability to file tax returns electronically—in many cases fraudsters take advantage of that and of separate Internal Revenue Service measures intended to ease the filing process for those without bank accounts.
A spike in the number of bogus returns in the last five years has prompted law enforcement agencies—including the Justice Department and the IRS—to dramatically increase their focus on finding the tax thieves.
On Monday, the Justice Department will release data showing it filed charges against more than 880 people suspected of stolen identity tax refund crimes in the last budget year.
The number of IRS investigations jumped 66% in the past year, with the agency initiating 1,492 probes of identity-theft related crimes in fiscal 2013, up from 898 in 2012 and 276 in 2011. The IRS said it is working closely with local law-enforcement officials in more than 35 identity theft task forces nationwide.
Often the first to spot the suspects are local authorities investigating other crimes—another indication, officials say, that such paperwork crimes are being adopted by a wider range of crooks.
The scams can be sophisticated, but even simpler versions are difficult to stop. Unlike more traditional versions of tax fraud, where individuals lie about their income or deductions, stolen-identity refund fraud involves creating an entirely fake tax document, in which the only true items are the name and Social Security number.
One problem is that the IRS generally can’t match up recent earnings records with individual returns until well after the false returns are filed.
“There’s been a perception out there by criminals used to earning their money through crimes of violence that if they shift to this, it is cleaner and simpler,” said Kathryn Keneally, head of the Justice Department’s tax division. “But if you look at our prosecutions and the lengths of the sentences we’re getting, we are moving toward our goal of making this a very unprofitable crime.”
More sophisticated groups have stolen millions of taxpayer dollars before getting caught. During the past year federal authorities have brought cases targeting large fraud networks in Montgomery, Ala. The Tampa Bay region of Florida also has been a hot spot for such fraud.
The crime creates two victims—the U.S. Treasury and individual taxpayers, who only learn of the fraud when they try to file their legitimate returns. Those taxpayers are stuck with the hassle of proving to the IRS that the previous document was a phony claim.
The IRS has adopted elaborate electronic filters to screen phony returns. An IRS watchdog agency recently reported that the IRS identified nearly 580,000 returns claiming $3.6 billion in fraudulent refunds during the 2013 filing season. The IRS said it prevented refunds in about 96% of the cases. But some doubt remains about exactly how many phony claims are being paid. The IRS watchdog recently said the agency has issued potentially fraudulent returns totaling several billion dollars in some past years.
“The question is, do the systems that are in place at DOJ and the IRS actually work? Certainly not yet, given recent data we’ve seen,” said Sen. Orrin Hatch (R., Utah), the top Republican on the Senate Finance Committee.
IRS Commissioner John Koskinen said in a statement the agency is “fighting identity theft head-on at the IRS and making substantial progress with the help of the Justice Department and local law enforcement.” He said the IRS is “stopping more identity theft before these fraudulent refunds go out the door.”
Via: wsj