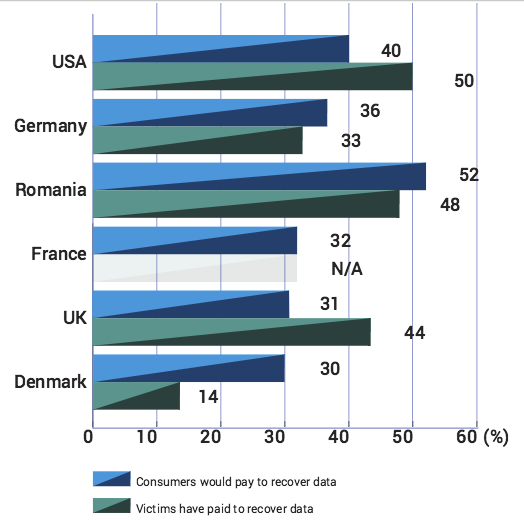
Exactly half of all Americans who have fallen victim to ransomware have fulfilled the attackers’ demands and paid the ransom.
This is just one of the findings of Ransomware. A Victim’s Perspective: A study on US and European Internet Users (PDF), a report conducted by Bitdefender in November of last year.
For its study, the security firm spoke with just over 3,000 web users located in the United States, France, Germany, Denmark, the United Kingdom, and Romania in an attempt to understand how a victim of crypto-ransomware responds to an infection session.
Bitdefender found that more than a fifth (21.21 percent) of all phishing emails laced with crypto-ransomware target the United States, making Americans the most sought-after targets for malware sample like Cryptolocker2 and CryptoWall 4.0.
This might explain why half of U.S. respondents answered that they have paid the ransom, whereas 40 percent said they would meet the attackers’ demands were their files to be encrypted.
 Source: Bitdefender
Source: Bitdefender
Overall, 50 percent of respondents everywhere said that they would pay for the return of their files. The British were willing to pay the most at $568 per each infection session, the study found.
When they were willing to pay, respondents said they were interested in recovering their personal documents first and foremost, Bitdefender determined, followed by personal photos and job-related documents.
Last year, the FBI stated that paying the ransom was sometimes the easiest way for a victim to regain access to their files.
This sentiment notwithstanding, payment in no way guarantees that the attackers will cooperate and provide victims with a decryption key. (This assumes that the encryption process works properly and that coding errors have not already rendered a victim’s files irretrievable.)
“The ransomware phenomenon has been hitting internet users and generating huge profit for cyber-criminals for years,” Catalin Cosoi, chief security strategist at Bitdefender, told SCMagazine. “While victims are usually inclined to pay the ransom, we encourage them not to engage in such actions as it only serves to financially support the malware’s developers.”
With that in mind, it is important that users regularly back up their data. These backups could help a victim recover from a ransomware attack without requiring them to pay the ransom fee.
For more information on how you can respond to and even prevent a ransomware infection, please click here.
Via: tripwire