The attack that spreads malware through a simple website visit.
What if I told you that there’s a type of cyber attack that can infect your computer with malware without you doing anything?
I don’t mean to make you paranoid, I really don’t. It’s just whenever I told my friends about drive-by download attacks, they stared at me in disbelief.
You mean I can get a malware infection on a legitimate website? And without clicking on anything at all? But… how?
The how part is what I want to explain in this guide. Especially because, with this attack, the standard “I don’t visit nasty websites so there’s no way I can get infected” argument doesn’t work. And this, unfortunately, is still an attitude shared by many.
1. What is a drive-by attack and how it happens
Imagine this: you get up in the morning, pull up your laptop and check your favorite news website. Once you’re on the page, the malicious code embedded into the website (usually an exploit kit) starts scanning your computer for security vulnerabilities. Just so you know, the security holes on your PC are usually created by outdated apps of all kinds, from plugins to browsers, chat apps and beyond.
Once the appropriate weakness has been spotted, malware goes on to infiltrate the system and take control of it. Just like in the graphic below:

If you ever become a victim of drive-by download attacks (which I really hope you don’t), you may experience the following stages.
At first, you’ll probably get mad at the website owner. If you can trace the infection back to the source, that is. However, the problem is that the owner most likely had nothing to do with it and didn’t even know that his website was distributing malware.
Second, you’ll question how such a big and reputable website could become a malware-spreading agent. You might be surprised, but this happens all the time. Not because website owners want to imperil their visitors, but because software is not flawless and websites get hijacked. (More examples at the end of the article.) Another cause is the exploit-kits-as-a-service model, which makes hacking websites easy, fast and cost-effective.
Third, you’ll wonder how you can get a malware infection without clicking or downloading anything. This was the norm until a few years ago. As cybercriminals refined their tactics, they found ways to spread their malicious software without requiring user/victim interaction.
In drive-by download attacks, attackers compromise websites and embed malicious elements inside. These elements can range from malicious JavaScript code injects, to malvertisements, malicious redirects, cross-site scripting attacks (also known as XSS), malicious iFrames that execute invisibly or other subtle attack techniques that potential victims can’t spot on their own.
No matter the tactic, the objectives are clear: cyber criminals either want to install and run malicious software on your device or steal your sensitive information (financial, identity-related, etc.).
Consequences range from adware infections to financial loss or even data encryption (in the case of a ransomware infection).
2. How you’re exposing yourself to drive-by attacks
Of course no one wants to become a cyber attack victim, but you may be doing it unintentionally. Here are some of the ways you’re putting up the “Come and get it!” sign right where cyber criminals can sniff the opportunity:
You don’t update your software (operating system, browsers, plugins, desktop apps, mobile apps, etc.).
If you don’t think this is a big deal, let’s look at a single number.
This is how many vulnerabilities the top 3 most used browsers in the world have had last year and this year, until the date this post was first published (November 8, 2016).
1004
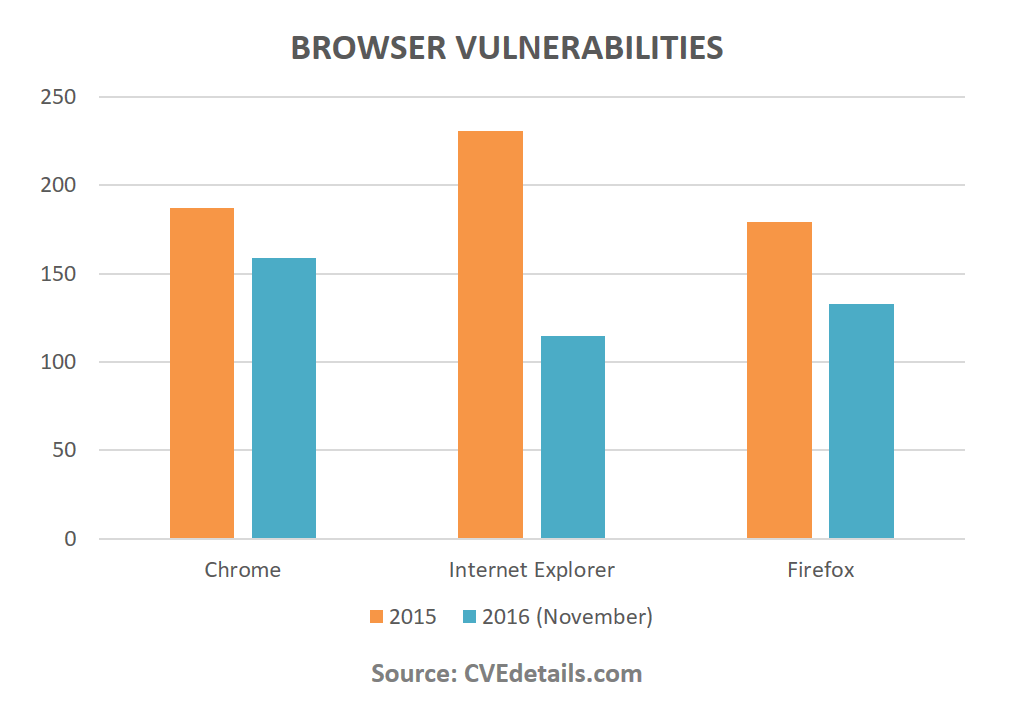
Many of these security issues allow the attacker to take full control over the compromised system. From there on, the malicious hacker can do whatever he/she wants.
And it’s likely that you won’t see the drive-by download coming either. Not when you’re on NBC, reading the latest news.
You hoard plugins and add-ons in your browsers and never clean them up.
Do you even remember the last time you took a peek at what’s going on in your browser, plugin-wise?
The more add-ons and plugins you install in your browsers, the more you increase your chances that one of them will be hacked. Yes, these things can make your life easier, but blindly giving permission to all sorts of developers to your browser is not a great idea.
Do you check where these plugins come from? Do you install them from safe sources?
Ask yourself this and then reconsider. And do it before you go about your business and end up with financial malware on your PC.
You don’t use a safe browser for your online shopping or online banking activities.
Your browser is the entry point for most drive-by download attacks. So, for example, using Chrome for all your Internet-related needs could spell trouble. Especially if you’re a digital hoarder, like I just mentioned. (The first step to solving this is admitting it. We’ve all done it.)
Your banking data and identity-related info is what cyber criminals pine for. Don’t be the “stealing candy from a baby” type.
You rely on your (free) antivirus for all your online protection needs.
No matter how often we share this, it doesn’t seem to be enough: there is no panacea in terms of Internet security. Your antivirus can’t provide miracles (like knowing and blocking all the threats out there). And neither can any other single security products.
Why?
Because things are just too complicated, both in terms of software and hardware. Because cybercrime comes in volumes that no single company could possible handle. It doesn’t mean that they’re weak, it’s just the pragmatic reality of things.
It would be easy to have to buy just one thing to keep us safe online, but we can’t. So instead of wasting our energy wishing for things to be different, let’s all work together to make it happen.
You don’t know what fileless malware can do.
Not many people know that malware can be bundled together to wreak havoc on victim’s devices. Such malicious software cocktails can also include fileless malware, which your antivirus can’t detect. As the name suggests, this type of infection runs in the RAM memory of your device and it doesn’t use any files.
Drive-by attacks are notoriously stealthy and using fileless malware adds to this strategy and increases the impact. Reading up on fileless malware will open up your perspective and help you move from reactive to proactive online security (which is what we all need going forward).
You think that your mobile devices (smartphone, tablet) are safe by default
Android is plagued by malware of all sorts and drive-by download attacks are included on “the menu” as well. What’s more, you may have more data on your phone than on your laptop/desktop PC.
Your phone knows where you’ve been, who you’ve talked to, what messages you’ve written, you use it for online banking, for listening to music, etc. So why would you leave it unprotected?
If you don’t update your operating system, the chances that you’ll be hacked multiply. Just take a peek at this real-life case of a drive-by attack that affected over 300.000 Android users.
You believe that Apple products are unhackable
This common misconception can endanger your data, so it may be time to let it go. While there’s no doubt that Apple products and their respective operating systems are a lot more secure than others, they’re also prone to malicious hacking.
And because some people just want to watch the world burn, here’s a case of a drive-by download attack involving a website connected to Dalai Lama, which targeted Mac users. It happened before and it can happen again. So my question to you is: why take unnecessary risks?
3. How to protect your devices and data from drive-by attacks
You can do more to shelter your sensitive information from the greedy hands of online criminals.
Update your software quickly and constantly.
When a software maker releases and update, cybercriminals will rush to reverse engineer it and target Internet users who have not applied the update. This is why updating your software (including your operating system) is key and this is why you need to do it fast!
Luckily, this is a part of your protection you can easily automate to save time and energy. I recommend you check out how Heimdal FREE can help you (download link at the end of this guide).
Once your updates are taken care of, it’s time to move on to the next phase.
Clean up your software.
The more plugins you have, the more exposed you are. Learn how to remove old software that’s making your computer vulnerable.
Get rid of the clutter! Keep only products you trust and use constantly. You’ll not only feel safer, but you’ll also be safer. Plus, you’ll probably speed up your PC too, which is a welcome benefit.
Use a separate browser for online shopping and financial transactions.
At the moment, Microsoft Edge is one of the safest options out there (if you eliminate Flash from your system altogether).
You can also choose to use an option such as Bitdefender Safepay or browse through these 8 alternatives.
Just make sure sure you pay extra attention when entering confidential data over the Internet.
Use a reliable antivirus with a built-in URL checker
Choosing the best antivirus for your PC is an important step and you still need this reactive protection layer on your system.
For example, Bitdefender has Search Advisor and Avira has Browser Safety, and they’re not the only ones that integrate this feature.
However, I feel like it’s my obligation to also present the potential pitfalls of browser extensions that rate websites before you click on links. Read and make your own decisions, but please don’t go without antivirus.
Go proactive
Now that your reactive protection is all set up, it’s time to handle the threats that your antivirus can’t catch. And this includes the fileless malware I mentioned earlier.
Traffic filtering is a key component of your online security, so I recommend you explore what it can do for you. Blocking threats based on where they come from can be a huge advantage for you, since changing infrastructure (servers especially) is a costly and difficult thing to do for cybercriminals.
Protect all your devices
My advice is to never take security for granted. Think of all your devices and what you can do to keep them safe. Don’t disregard your phone or tablet, or even your TV. Who knows how malware creators will improve drive-by attacks and which platforms they’ll target next?
Think of security as a core component of your digital life. It’s not a nice-to-have type of thing. It’s need-to-have!
Use an ad blocker
Drive-by download attacks often use online ads as infections vectors. Using an ad blocker will help you reduce your exposure to this type of attacks. It won’t eliminate the risk entirely, because, as you’ve seen in the beginning, drive-by attacks come in many shapes and sizes, but it will make your system safer.
I hope that this guide has helped you get a better idea of how drive-by download attacks work and what you can do to shelter your devices and data from them.
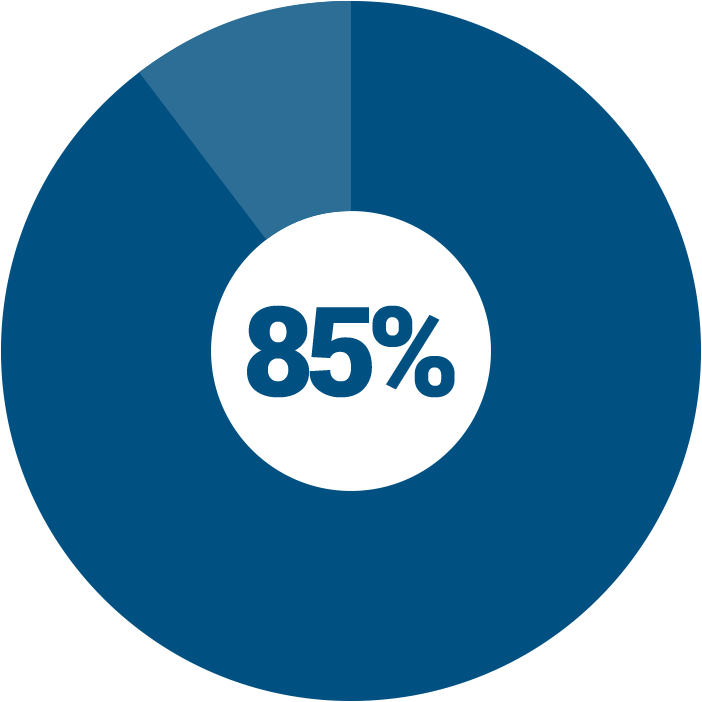
Automate your updates & keep malware out of your PC!
Heimdal FREE updates your apps automatically and silently and
blocks 85% of attacks that target vulnerabilities in your apps!
FAST | TIME-SAVING | EASY TO USE
DOWNLOAD HEIMDAL FREE
via: heimdalsecurity