We’re nearing the end of Microsoft’s unprecedented free upgrade offer for Windows 10. The offer officially expires July 29, 2016, on the one-year anniversary of the operating system’s initial release. But what happens then?
Microsoft’s ambitious plan to get Windows 10 running on a billion devices within the next few years depends to a large extent on the success of its free upgrade offer.
When the company first announced the terms of that offer in May 2015, it literally included an asterisk and fine print. Those terms have changed slightly over the intervening months, but one element has remained constant: The offer is good for one year after the availability of Windows 10.
Here’s the actual wording of the offer, as it appears today:
Get the best Windows experience. Ever.
Ready for Windows 10? Qualified Windows 7 or Windows 8.1 devices can upgrade for free. Offer ends July 29, 2016.
The text that appears in the fine print at the bottom of that page has changed slightly over the past year. Here’s how it now reads (emphasis added):
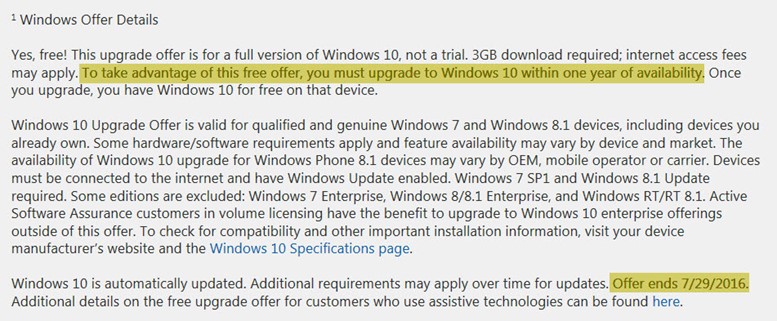
The fine print on the Windows 10 upgrade offer, as of June 2016.
Here’s the tl;dr (Too long; didn’t read) version if you don’t want to keep reading:
1. The free upgrade offer ends on July 29 and will not be extended.
2. Any upgrades completed before that date will be valid for as long as the device lasts.
3. There is a possibility that Microsoft will introduce some new upgrade offers after July 29, but don’t count on it.
In fact, Microsoft’s real goal with this upgrade offer isn’t just to get its installed Windows 10 base to a billion. The long-term goal is to help close the books on Windows 7 in an orderly fashion before its extended support commitment ends on January 14, 2020.
Some of those Windows 7 PCs will simply be retired, of course. But what about those that are only a few years old and have more than four years of usable life ahead of them? For Microsoft executives, the prospect that hundreds of millions of PCs will still be running Windows 7 on New Year’s Day 2020 has to bring back unpleasant flashbacks of Windows XP’s messy end.
After nearly a year, Microsoft says a total of 300 million devices are running Windows 10. Many of those, perhaps one-third or more, represent new PCs. Another big chunk represents newer devices originally sold with Windows 8 or 8.1, Windows 10 has succeeded in cutting the share of devices running those versions nearly in half over the past year, and the share of PCs running Windows 8.1 should be in the low single digits by the end of 2017.
But what about Windows 7? As measured by the U.S. Government’s Digital Analytics Program, the percentage of Windows PCs running that version has dropped significantly in the past year, going from 71.1 percent in the first quarter of 2015, before the release of Windows 10, to less than 60 percent at the end of May 2016.
That’s still a lot of Windows 7 PCs, and there’s not much evidence that even the carrot of a free upgrade will be enough to move more than another few percent as the deadline approaches.
Which explains why the offer won’t be extended. In early May 2016, the company made it official. If you want to upgrade a PC from Windows 7 or Windows 8.1 after July 29, you’ll have to pay for the privilege.
There’s plenty of precedent for this, based on past behavior. For Windows 7 and 8, Microsoft offered significant introductory discounts and then ended them on schedule after a few months, with no extensions.
Financially, this decision is unlikely to have much of an impact. Retail upgrades have historically represented a microscopic share of Microsoft’s revenue (see the chart in this article), and most customers who might have been willing to pay for an upgrade will have taken advantage of the free offer by the time the Anniversary Update rolls around.
Asking existing Windows 7 users to pay $99 or more after they’ve spent a year avoiding the free upgrade seems like a surefire way to guarantee that they never upgrade. That significantly increases the risk of an XP-style mess come 2020.
On the other hand, the free upgrade offer never really applied to large businesses that run Windows Enterprise editions. For those customers who also have purchased Software Assurance for those volume licenses, the Windows 10 upgrade offer is, if not free, at least already paid for. The decision of whether and when to upgrade is driven by business needs, not by the cost of an upgrade license.
In the new “Windows as a Service” model, Microsoft says it plans to deliver two or three new releases each year. The Anniversary Update is the first release in the Redstone update series, and it’s scheduled to arrive at more or less the same time that the original upgrade offer ends. Another Redstone feature update is scheduled to arrive in the first half of 2017.
In the last few weeks before July 29, Microsoft will no doubt brag a bit about the success of the upgrade offer so far and encourage holdouts to upgrade. (Remember, the point of the deadline is to add urgency.)
And, of course, the end of this upgrade offer doesn’t eliminate the possibility of a new offer. If not free, then perhaps a discounted in-place upgrade. But an extension of the current offer is not going to happen.
One important date to watch is October 31, 2016. That’s when OEM sales of new PCs with Windows 7 Professional officially end. That means more than three years in which the population of Windows 7 PCs will presumably shrink as old PCs die and are replaced by newer models running Windows 10 (or aren’t replaced at all).
Anyone who has taken Microsoft up on its free Windows 10 upgrade offer before the expiration date has a “digital entitlement” tied to that hardware. That upgrade doesn’t expire.
A few logistical questions remain unanswered. For example, you can currently use a product key for Windows 7, 8, or 8.1 to activate the corresponding edition of Windows 10. Come July 30, Microsoft’s activation servers should stop accepting those keys. But we won’t know until that day comes.
As of that anniversary, Microsoft also says it plans to begin uninstalling its controversial Get Windows 10 software. But there are no plans to remove the Windows 10 download page, which is useful for anyone who needs the Windows 10 bits to do a recovery or a clean install on a machine that already has a Windows 10 license. But will the Upgrade Now button still work without requiring payment upfront?
It would be nice if Microsoft would publish details about how this transition will work, but after watching the company’s communications over the past year, I’m not betting on that.
Via: zdnet