A cybersecurity researcher at ESET today published an analysis of a new piece of malware, a sample of which they spotted on the Virustotal malware scanning engine and believe the hacker behind it is likely interested in some high-value computers protected behind air‑gapped networks.
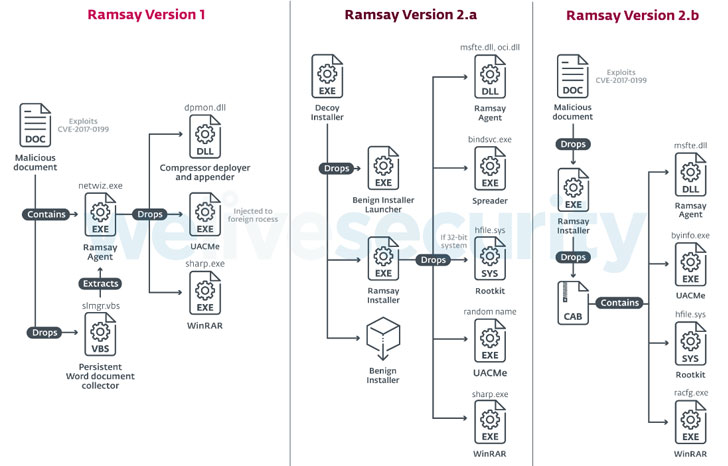
Dubbed ‘Ramsay,’ the malware is still under development with two more variants (v2.a and v2.b) spotted in the wild and doesn’t yet appear to be a complex attacking framework based upon the details researcher shared.
However, before reading anything further, it’s important to note that the malware itself doesn’t leverage any extraordinary or advanced technique that could let attackers jump air-gapped networks to infiltrate or exfiltrate data from the targeted computers.
According to ESET researcher Ignacio Sanmillan, Ramsay infiltrates targeted computers through malicious documents, potentially sent via a spear-phishing email or dropped using a USB drive, and then exploits an old code execution vulnerability in Microsoft Office to take hold on the system.
‘Several instances of these same malicious documents were found uploaded to public sandbox engines, labeled as testing artifacts such as access_test.docx or Test.docx denoting an ongoing effort for trial of this specific attack vector,’ the researcher said.
Ramsay malware primarily consists of two main functionalities:
- Collecting all existing Word documents, PDFs, and ZIP archives within the target’s filesystem and storing them to a pre-defined location on the same system or directly to a network or removable drives.
- Spreading itself to other computers being used within the same isolated facility by infecting all executable files available on a network shares and removable drives.
According to the researcher, the Ramsay samples they found do not have a network-based C&C communication protocol, nor does any attempt to connect to a remote host for communication purposes.
Now the question arises, how the attackers are supposed to exfiltrate data from a compromised system.
Honestly, there’s no clear answer to this at this moment, but researcher speculate that the malware might have been ‘tailored for air‑gapped networks’ with similar scenarios—considering that the only option left is to physically access the machine and steal the collected data with a weaponized USB.
‘It is important to notice that there is a correlation between the target drives Ramsay scans for propagation and control document retrieval,’ the ESET researcher said.
“This assesses the relationship between Ramsay’s spreading and control capabilities showing how Ramsay’s operators leverage the framework for lateral movement, denoting the likelihood that this framework has been designed to operate within air-gapped networks.’
‘The current visibility of targets is low; based on ESET’s telemetry, few victims have been discovered to date. We believe this scarcity of victims reinforces the hypothesis that this framework is under an ongoing development process, although the low visibility of victims could also be due to the nature of targeted systems being in air-gapped networks,’ he added.
However, a lack of technical and statistical evidence doesn’t support this theory yet and remains a broad guess.
Moreover, since the malware is still under development, it’s too early to decide if the malware has only been designed to target air-gapped networks.
It likely possible that the future versions of the malware could have an implication to connect with a remote attacker-controlled server for receiving commands and exfiltrating data.
We have reached out to ESET researcher for more clarity on the ‘air-gap’ claim and will update this story once he responds.
UPDATE: Researcher Explains ‘Air Gap’ Scenarios
Researcher Ignacio Sanmillan, who discovered and analyzed Ramsay malware, has provided the following explanation for our readers.
“We only have a copy of the Ramsay agent, which only has code to aggregate and compress the stolen data in a very decentralized and covert way on the local filesystem of the infected host. Based on this, we assume that another component is responsible for scanning the filesystem, locating the compressed files, and performing the actual exfiltration.”
On asking if the attacker needs to rely on the physical access for data exfiltration, Sanmillan said:
“There are several ways the attacker might do this. We have not seen this operation performed; however, we have a few hypotheses on how the attacker could do this. Those are only our best-educated guess and pure speculation at this point, so please treat those two hypothetical scenarios as such.”
“Scenario 1 — Imagine System A, connected to the Internet and under full control of the Ramsay operators, and System B, an air-gapped computer infected by the Ramsay agent. Then imagine a legitimate user of those systems occasionally transferring files between both systems using a removable drive.”
“When the drive is inserted into System A, the attacker could decide to place a special control file on the removable drive which, when connected to System B, would cause the Ramsay agent to execute the Ramsay exfiltrator which would be built to retrieve the staged stolen data and copy it to the removable drive for later retrieval once the removable drive gets connected to System A. This scenario is a variation of how Sednit / APT28 operated USBStealer.”
“USBStealer systematically copied the stolen data on the removable drive used between System A and System B, while Ramsay stages the stolen data locally for a future explicit exfiltration.”
“Scenario 2 — Imagine Ramsay agent running for days or weeks in an air-gapped network, staging on the local filesystem all the data it can find on network drives and all the removable drives that got connected to the system.”
“Then at some point, the attacker decides it is exfiltration time. He would need to gain physical access to the infected system and either obtain code execution to run the Ramsay exfiltrator, or in case the system does not have full-disk encryption, boot the system from a removable drive, mount the filesystem, parse it to retrieve the well-staged stolen data and leave.”
“This scenario is more elaborate and requires the physical presence of an operative/accomplice, but it could still be plausible as it would allow for a very quick on-site operation.”
To answer if the malware author can integrate remote C&C communication module in future versions, the researcher said:
“Ramsay has a series of common functionality implemented across their versions, which is the control-file based protocol and how artifacts involved in this protocol are retrieved from Removable media and Network Shares.”
“This denotes that evaluation for these techniques was taken into account while designing this malware, all of which point towards the implementation of capabilities for operation without the need for any network connection.”
“It seems that if attackers would leverage techniques relying on Network artifacts would not correlate to the philosophy of this malware. We indeed think that Ramsay can be under development, but we are highly inclined to believe that they won’t introduce a Network-based exfiltration component.”
via: thehackernews