Bank of England and Fed officials say cryptocurrency is too small to threaten world economy amid warnings of bubble.
Bitcoin topped $11,000 on Wednesday, less than 24 hours after hitting $10,000 for the first time, as central bankers on both sides of the Atlantic sought to ease fears that a potential bubble in the cryptocurrency was a threat to the global economy.
The digital currency continued on its record-breaking streak, rising to $11,150 just as analysts were digesting the news that it had made it through $10,000. However, it then fell back below $10,500, again highlighting its volatility.
Bitcoin has risen tenfold in value so far this year, the largest gain of all asset classes, prompting sceptics to declare it a classic speculative bubble that could burst, like the dotcom boom and the US sub-prime housing crash that triggered the global financial crisis.
“The madness of crowds is well documented, but it is quite something to behold in the flesh. It’s hard to keep up with this – bitcoin just flew past the $11,000 mark, leaping $200 in barely five minutes before taking another big leg higher,” said Neil Wilson, senior market analyst at ETX Capital.
“It’s up more than 14% today alone and the year-to-date chart is simply staggering. There are no fundamentals or technical that explain this other than it being a massive speculative bubble.”
The rapid growth in the value and popularity of the virtual currency, which emerged in the aftermath of the financial crisis and allows people to bypass banks and traditional payment methods to pay for goods and services, has forced central banks, financial regulators and institutions to consider how to respond.
Sir Jon Cunliffe, a deputy governor at the Bank of England with financial stability, said bitcoin was too small to pose a risk to the global economy.
He told BBC Radio 5 Live: “This is not a currency in the accepted sense. There’s no central bank that stands behind it. For me it’s much more like a commodity.
“This is not at a size where it’s a macroeconomic risk to the global economy, but when prices are moving like that, my view would be investors need to do their homework.”
Over in the US, William Dudley, the president and chief executive of the Federal Reserve Bank of New York, said bitcoin is “more of a speculative activity” than a currency.
“I would be pretty cautionary about it. I think that it’s not a stable store of value,” he said at an event in New Jersey. “I would be, at this point, pretty skeptical of bitcoin,” he added.
Dudley echoed Cunliffe’s point that the bitcoin is still relatively small. “Bitcoin is tiny relative to the amount of payment transactions that are executed in the United States.”
Commenting on the idea that the Fed could potentially offer it own digital currencies, he said: “I think at this point it’s really very premature to be talking about the Federal Reserve offering digital currencies, but it is something we are starting to think about.”
Banks and other financial institutions have been concerned about bitcoin’s early associations with money laundering and online crime, and it has not been adopted by any government.
The JP Morgan chief executive, Jamie Dimon, has described bitcoin as “worse than tulips”, in reference to a famous market bubble from the 1600s. Speaking in September, Dimon said the digital currency was a fraud that would ultimately blow up, adding it was only fit for use by drug dealers, murderers and people living in places such as North Korea.
However, according to reports last week, JP Morgan is considering whether to help its own clients bet on the price of bitcoin through proposed futures contracts to be offered by CME Group. The bank would collect fees for providing such a service.
Dennis de Jong, the managing director at the online currency broker UFX, said the value of the cryptocurrency was likely to rise further.
“Until bitcoin becomes a commonly used payment source, it’s very possible that it could hit $15,000 and beyond based on its current desirability,” he said. “If bitcoin falls into wider circulation, and becomes accepted into more conventional funds and exchanges, we are likely to see a normalization of its value.”
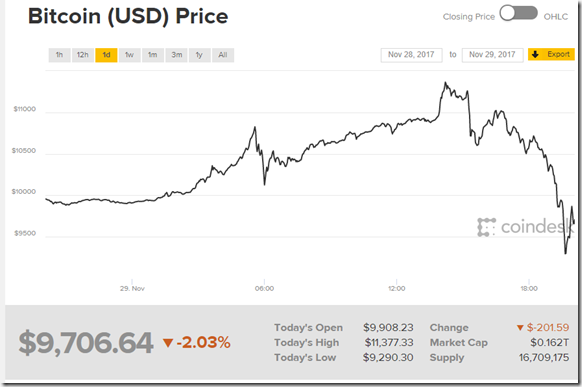
FYI—the price does fall and at the moment :
via: theguardian