Watt’s all this about cyberspy threat leaks… Analysts weigh in.
Analysis The energy sector across multiple Western countries is under intensified assault by hackers. Security experts warn that industrial systems are wide open to potential exploit once hackers secure a foothold, the most difficult part of the hacking process, using targeted phishing or similar tactics.
The UK’s government lead cyber defense agency recently warned that hackers are targeting the country’s energy sector to some effect. Just over a week ago, a memo was leaked from the NCSC (National Cyber Security Centre) warning that it had spotted connections “from multiple UK IP addresses to infrastructure associated with advanced state-sponsored hostile threat actors, who are known to target the energy and manufacturing sectors,” Motherboard reported.
That warning implied that state-sponsored hackers may have already secured a foothold in the UK’s energy sector network. Whether or not this compromised access is enough to do any harm is unclear.
Such attacks are far from limited to the UK. Ireland’s Electricity Supply Board (ESB) is under attack from suspected Russian hackers out to infiltrate control systems, The Times reports. Security sources in the Emerald Isle tell El Reg the attack involved a phishing email sent to an engineer who twigged it was bad and reported it. ESB said the attack failed.
Meanwhile, multiple US energy companies were sent phishing emails as part of a campaign aimed at stealing stealing credentials, Cyberscoop adds.
Reconnaissance
Added together, the reports suggest a concerted effort to gather steal credentials, map networks and probe for weaknesses in Western energy sector firms in preparation for a possible future attack. While nothing damaging has happened to date, the whole threat of attacks on the energy sector has ratcheted up since December 2015’s game changing BlackEnergy malware-based attacks in the Ukraine, which resulted in power outages for hours in districts around Kiev.
The recent “reconnaissance” campaign on Western energy sector targets likely takes the form of directed phishing attacks rather than internet-wide scanning and worm activity, according to experts at Rapid7, the firm behind the popular Metasploit pen-testing tool.
Hackers phish people targeted as working in energy sector in assault probably aimed at getting shells on victims’ computers. Shelled accounts then connect back “to infrastructure associated with advanced state-sponsored hostile threat actors”.
“None of these steps are particularly visible to Rapid7 Sonar, nor Heisenberg. Heisenberg is good at catching undirected attacks (internet-wide scanning and worm activity), not so much directed attacks like this,” explained Tod Beardsley at Rapid7.
Mind the air-gap. What air-gap?
Andrea Carcano, founder and chief product officer of Nozomi Networks, said that the impracticality of air gap sensitive operation networks and systems from corporate IT networks is partly responsible for the problem.
“Targeting engineers with access to control systems with phishing messages is pretty straight-forward and, if successful, could be extremely damaging,” Carcano explained. “In tandem, while air-gapping offered a degree of protection, the way our nuclear plants, and any infrastructure for that matter, is maintained today means this practice is defunct.”
“We often see engineers ‘plugging’ in their own devices to perform diagnostic checks. Should that person’s device have been compromised, this action could unleash malware directly into the heart of each component being checked, which then crawls and burrows deeper into the infrastructure,” he warned.
Air-gapping SCADA systems might seem as sensible tactic but as Faizel Lakhani, a pioneer of SCADA technology, previously told El Regin practice operational networks are seldom isolated because of a test link someone has forgotten to take out or a bridge to Wi-Fi networks someone has set up, among other reasons.
Almost everything is connected to the internet one way or another and the sectors tightening embrace of industrial IoT technology for remote monitoring and other functions is only pushing this along. All this added connectivity has implications for those attempting to defend industrial control and energy distribution systems from attack.
Carcano added: “You have to assume that all parts of critical infrastructure are being probed for vulnerabilities 24/7 from a risk management point of view. While Information Technology (IT) and Operation technology (OT) that control the electric grid systems and other critical infrastructure are separated, there have been increasing connections.
“Risk management is an ongoing process. Up to date patching and the use of artificial intelligence and machine learning to immediately identify suspicious network communications and incidents helps to harden the security that guards industrial control systems,” he added.
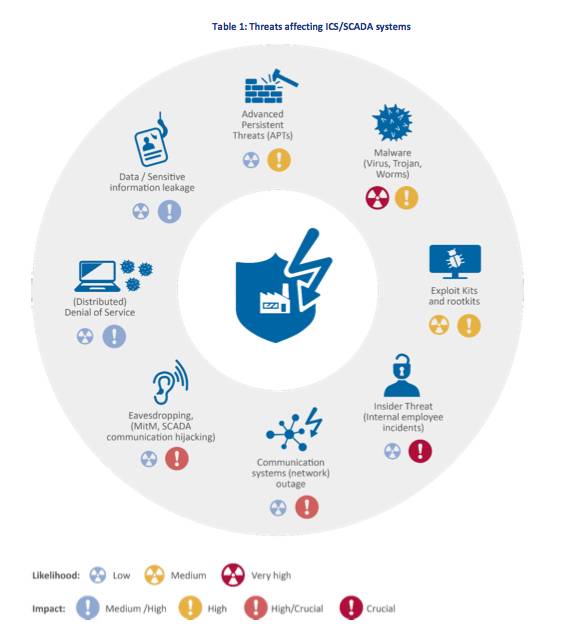
Industrial control; system threats [source: ENISA whitepaper: Communication network dependencies for ICS/SCADA Systems]
Internet exposure
A report on the Industrial Control Systems (ICS) threat landscape last year by Kaspersky Lab revealed that large organizations likely have ICS components connected to the internet that could allow cybercriminals to attack critical infrastructure systems. US organizations were especially exposed.
The investigation found that 17,042 ICS components on 13,698 different hosts exposed to the internet likely belong to large organizations. These include energy, transportation, aerospace, oil and gas, chemicals, automotive and manufacturing, food and service, governmental, financial and medical institutions. The figures are the latest available from Kaspersky Lab. Other more recent studies present a similar picture albeit it in less detail.
“The world isn’t ready for cyber threats against critical infrastructure, but criminals are clearly ready and able to launch attacks on these facilities – as the widely-speculated compromise of the UK’s energy sector shows,” said David Emm, principal security researcher at Kaspersky Lab.
“We’ve seen attempts on power grids, oil refineries, steel plants, financial infrastructure, seaports and hospitals – cases where organizations have spotted attacks and acknowledged them. However, many more companies do neither, and the lack of reporting these incidents hampers risk assessment and response to the threat.”
“Security must be tailored to the specific needs of each organization and be seen as an ongoing process. This is true also of the human dimension – tricking people into taking action that launches the initial exploit is as common in attacks on such facilities as it is in any other context.” he added.
Phish fry
Groundbreaking research by ERPScan unveiled two years ago showed how hackers might be able to bridge the gap between ostensibly air-gapped systems in oil and gas production by pivoting from enterprise planning onto production systems. Vulnerabilities and insecure installations in SAP business software and other enterprise systems might be used to interfere with loosely-couple but nonetheless connected industrial control systems.
That might be one way in but, in practice, there might be more straightforward ways to secure the first crucial foothold into targeted networks.
Michael Shalyt, chief exec of APERIO Systems, and a former team leader in an elite Israel Defense Forces (IDF) intelligence unit, explained that the initial point of entry is key in any operation ultimately geared towards planting malware at strategic locations on a targeted SCADA (industrial control) network.
“Unfortunately, a typical SCADA environment today is very easy to branch out across and/or affect any specific piece of equipment remotely – whether due to lack of patching of known PLC vulnerabilities or the wealth of 0-day vulnerabilities that we don’t yet know about but are obviously there. So, once an attacker has a foothold – spreading and “borrowing” is easy,” Shalyt told El Reg.
“The hardest part is getting the initial ‘foot in the door’ – as the SCADA network is usually isolated from the outside networks (in theory…),” he added.
One of the easiest ways is still the fairly simple phishing attack, but state-sponsored hackers have a much more compressive playbook at their disposal that feature “willing or unwilling” insiders and equipment counterfeiting and/or interference.
“Even isolated systems still must allow access – sometimes remotely – for maintenance and installation purposes,” Shalyt explained. “A state actor can uncover these types of business relationships and infect the relevant personnel in advance.”
Strategic infection of equipment before it is even installed at the plant/facility is an option open to hackers playing the long game.
Sleeper cells
There are additional possibilities that involve chaining 0-days to progressively gain access to incremental parts of the outside administrative network, and then breaking into networking hardware like routers and equipment that are designed to keep SCADA network separated from the rest of the world.
What might the capable hackers seemingly probing Western electricity distribution systems be seeking to do? Having “digital sleeper agents” – very well hidden malware that is completely passive at the moment but can shut down operations with the push of a (remote) button – is one possible objective. The goal on potential activation could be a show of strength – creating a psychological intimidation effect – rather than a tool to cause real economic damage. But once achieved, compromised access also offers a capability that might be deployed in times of war or conflict, as best evidenced by the attacks in Ukraine, Saudi Arabia and Qatar over recent years.
Best practice
Earlier this month, the SANS Institute released the results of their 2017 survey of energy companies, chemical producers, critical infrastructure providers and other industrial operators. The survey revealed that industrial control system (ICS) security risks had reached an all-time high-water mark.
Four out of 10 ICS security practitioners quizzed as part of the study said they lacked visibility into their ICS networks. Despite high profile news coverage of recent attacks on unpatched systems, SANS found that only 46 per cent of respondents regularly apply vendor-validated patches, and 12 per cent neither patch nor layer controls around critical control system assets.
While reliability and availability remain the highest priority for OT systems, 69 per cent of ICS security practitioners believe threats to the ICS systems are high or severe and critical.
ICS-SCADA security [source: ENISA]
The latest annual study by EU security agency ENISA provides recommendations on how to protect critical infrastructure systems such as industrial control systems against cyber threats. ENISA’s paper on communication network dependencies for ICS/SCADA systems can be downloaded here.
via: theregister