In a key vote the European Parliament’s legal affairs committee has backed the two most controversial elements of a digital copyright reform package — which critics warn could have a chilling effect on Internet norms like memes and also damage freedom of expression online.
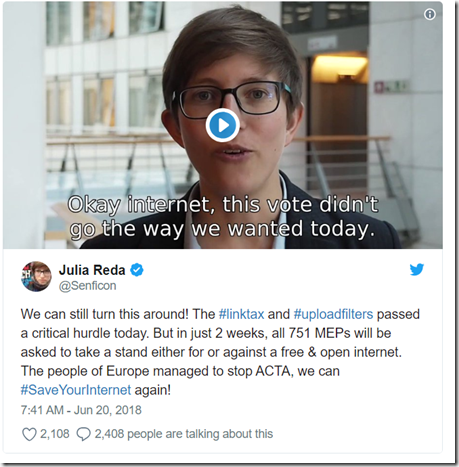
In the draft copyright directive, Article 11; “Protection of press publications concerning online uses” — which targets news aggregator business models by setting out a neighboring right for snippets of journalistic content that requires a license from the publisher to use this type of content (aka ‘the link tax’, as critics dub it) — was adopted by a 13:12 majority of the legal committee.
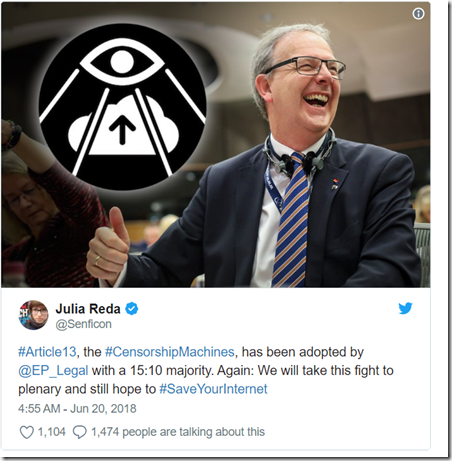
While, Article 13; “Use of protected content by online content sharing service providers”, which makes platforms directly liable for copyright infringements by their users — thereby pushing them towards creating filters that monitor all content uploads with all the associated potential chilling effects (aka ‘censorship machines’) — was adopted by a 15:10 majority.
MEPs critical of the proposals have vowed to continue to oppose the measures, and the EU parliament will eventually need to vote as a whole.
EU Member State representatives in the EU Council will also need to vote on the reforms before the directive can become law. Though, as it stands, a majority of European governments appear to back the proposals.
European digital rights group EDRi, a long-standing critic of Article 13, has a breakdown of the next steps for the copyright directive here. It’s possible there could be another key vote in the parliament next month — ahead of negotiations with the European Council, which could be finished by fall. A final vote on a legally checked text will take place in the parliament — perhaps before the end of the year.
Derailing the proposals now essentially rests on whether enough MEPs can be convinced it’s politically expedient to do so — factoring in a timeline that includes the next EU parliament elections, in May 2019.
A coalition of original Internet architects, computer scientists, academics and supporters — including Sir Tim Berners-Lee, Vint Cerf, Bruce Schneier, Jimmy Wales and Mitch Kapor — penned an open letter to the European Parliament’s president to oppose Article 13, warning that while “well-intended” the requirement that Internet platforms perform automatic filtering of all content uploaded by users “takes an unprecedented step towards the transformation of the Internet from an open platform for sharing and innovation, into a tool for the automated surveillance and control of its users”.
“As creators ourselves, we share the concern that there should be a fair distribution of revenues from the online use of copyright works, that benefits creators, publishers, and platforms alike. But Article 13 is not the right way to achieve this,” they write in the letter.
“By inverting this liability model and essentially making platforms directly responsible for ensuring the legality of content in the first instance, the business models and investments of platforms large and small will be impacted. The damage that this may do to the free and open Internet as we know it is hard to predict, but in our opinions could be substantial.”
The Wikimedia Foundational also blogged separately, setting out some specific concerns about the impact that mandatory upload filters could have on Wikipedia.
“Any sort of law which mandates the deployment of automatic filters to screen all uploaded content using AI or related technologies does not leave room for the types of community processes which have been so effective on the Wikimedia projects,” it warned last week. “As previously mentioned, upload filters as they exist today view content through a broad lens, that can miss a lot of the nuances which are crucial for the review of content and assessments of legality or veracity.”
More generally critics warn that expressive and creative remix formats like memes and GIFs — which have come to form an integral part of the rich communication currency of the Internet — will be at risk if the proposals become law…
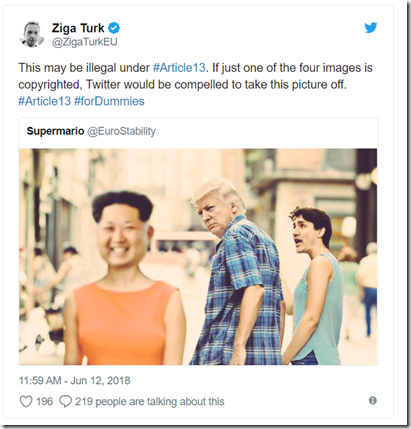
Regarding Article 11, Europe already has experience experimenting with a neighboring right for news, after an ancillary copyright law was enacted in Germany in 2013. But local publishers ended up offering Google free consent to display their snippets after they saw traffic fall substantially when Google stopped showing their content rather than pay for using them.
Spain also enacted a similar law for publishers in 2014, but its implementation required publishers to charge for using their snippets — leading Google to permanently close its news aggregation service in the country.
Critics of this component of the digital copyright reform package also warn it’s unclear what kinds of news content will constitute a snippet, and thus fall under the proposal — even suggesting a URL including the headline of an article could fall foul of the copyright extension; ergo that the hyperlink itself could be in danger.
They also argue that an amendment giving Member States the flexibility to decide whether or not a snippet should be considered “insubstantial” (and thus freely shared) or not, does not clear up problems — saying it just risks causing fresh fragmentation across the bloc, at a time when the Commission is keenly pushing a so-called ‘Digital Single Market’ strategy.
“Instead of one Europe-wide law, we’d have 28,” warns Reda on that. “With the most extreme becoming the de-facto standard: To avoid being sued, international internet platforms would be motivated to comply with the strictest version implemented by any member state.”
However several European news and magazine publisher groups have welcomed the committee’s backing for Article 11. In a joint statement on behalf of publishing groups EMMA, ENPA, EPC and NME a spokesperson said: “The Internet is only as useful as the content that populates it. This Publisher’s neighbouring Right will be key to encouraging further investment in professional, diverse, fact-checked content for the enrichment and enjoyment of everyone, everywhere.”
Returning to Article 13, the EU’s executive, the Commission — the body responsible for drafting the copyright reforms — has also been pushing online platforms towards pre-filtering content as a mechanism for combating terrorist content, setting out a “one hour rule” for takedowns of this type of content earlier this year, for example.
But again critics of the copyright reforms argue it’s outrageously disproportionate to seek to apply the same measures that are being applied to try to clamp down on terrorist propaganda and serious criminal offenses like child exploitation to police copyright.
“For copyrighted content these automated tools simply undermine copyright exceptions. And they are not proportionate,” Reda told us last year. “We are not talking about violent crimes here in the way that terrorism or child abuse are. We’re talking about something that is a really widespread phenomenon and that’s dealt with by providing attractive legal offers to people. And not by treating them as criminals.”
Responding to today’s committee vote, Jim Killock, executive director of digital rights group, the Open Rights Group, attacked what he dubbed a “dreadful law”, warning it would have a chilling effect on freedom of expression online.
“Article 13 must go,” he said in a statement. “The EU Parliament’s duty is to defend citizens from unfair and unjust laws. MEPs must reject this law, which would create a Robo-copyright regime intended to zap any image, text, meme or video that appears to include copyright material, even when it is entirely legal material.”
Also reacting to the vote today, Monique Goyens, director general of European consumer rights group BEUC, said: “The internet as we know it will change when platforms will need to systematically filter content that users want to upload. The internet will change from a place where consumers can enjoy sharing creations and ideas to an environment that is restricted and controlled. Fair remuneration for creators is important, but consumers should not be at the losing end.”
Goyens blamed the “pressure of the copyright industry” for scuppering “even modest attempts to modernize copyright law”.
“Today’s rules are outdated and patchy. It is high time that copyright laws take into account that consumers share and create videos, music and photos on a daily basis. The majority of MEPs failed to find a solution that would have benefitted consumers and creators,” she added in a statement.
via: techcrunch



 The reward scheme for the Microsoft Identity Bounty Program
The reward scheme for the Microsoft Identity Bounty Program