When it comes to safeguarding your Internet security, installing an antivirus software or running a Secure Linux OS on your system does not mean you are safe enough from all kinds of cyber-threats.
Today majority of Internet users are vulnerable to cyber attacks, not because they aren’t using any best antivirus software or other security measures, but because they are using weak passwords to secure their online accounts.
Passwords are your last lines of defense against online threats. Just look back to some recent data breaches and cyber attacks, including high-profile data breach at OPM (United States Office of Personnel Management) and the extra-marital affair site Ashley Madison, that led to the exposure of hundreds of millions of records online.
Although you can not control data breaches, it is still important to create strong passwords that can withstand dictionary and brute-force attacks.
You see, the longer and more complex your password is, the much harder it is crack.
How to Stay Secure Online?
Security researchers have always advised online users to create long, complex and different passwords for their various online accounts. So, if one site is breached, your other accounts on other websites are secure enough from being hacked.
Ideally, your strong password should be at least 16 characters long, should contain a combination of digits, symbols, uppercase letters and lowercase letters and most importantly the most secure password is one you don’t even know.
The password should be free of repetition and not contain any dictionary word, pronoun, your username or ID, and any other predefined letter or number sequences.
I know this is a real pain to memorize such complex password strings and unless we are human supercomputers, remembering different passwords for several online accounts is not an easy task.
The issue is that today people subscribe to a lot of online sites and services, and it’s usually hard to create and remember different passwords for every single account.
But, Luckily to make this whole process easy, there’s a growing market for password managers for PCs and phones that can significantly reduce your password memorizing problem, along with the cure for your bad habit of setting weak passwords.
What is Password Manager?
Password Manager software has come a very long way in the past few years and is an excellent system that both allows you to create complex passwords for different sites and remember them.
A password manager is just software that creates, stores and organizes all your passwords for your computers, websites, applications and networks.
Password managers that generate passwords and double as a form filler are also available in the market, which has the ability to enter your username and password automatically into login forms on websites.
So, if you want super secure passwords for your multiple online accounts, but you do not want to memorize them all, Password Manager is the way to go.
How does a Password Manager work?
Typically, Password Manager software works by generating long, complex, and, most importantly, unique password strings for you, and then stores them in encrypted form to protect the confidential data from hackers with physical access to your PC or mobile device.
The encrypted file is accessible only through a master password. So, all you need to do is remember just one master password to open your password manager or vault and unlock all your other passwords.
However, you need to make sure your master password is extra-secure of at least 16 characters long.
Which is the Best Password Manager? How to Choose?
I’ve long recommended password managers, but most of our readers always ask:
- Which password manager is best?
- Which password manager is the most secure? Help!
So, today I’m introducing you some of the best Password Manager currently available in the market for Windows, Linux, Mac, Android, iOS and Enterprise.
Before choosing a good password manager for your devices, you should check these following features:
- Cross-Platform Application
- Works with zero-knowledge model
- Offers two-factor authentication (multi-factor authentication)
Note: Once adopted, start relying on your password manager because if you are still using weak passwords for your important online accounts, nobody can save you from malicious hackers.
Best Password Managers for Windows
Windows users are most vulnerable to cyber attacks because Windows operating system has always been the favorite target of hackers. So, it is important for Windows users to make use of a good password manager.
Some other best password manager for windows: Keeper, Password Safe, LockCrypt, 1Password, and Dashlane.
1. Keeper Password Manager (Cross-Platform)
Keeper is a secure, easy-to-use and robust password manager for your Windows, Mac, iPhone, iPad, and iPod devices.
Using military-grade 256-bit AES encryption, Keeper password manager keeps your data safe from prying eyes.
It has a secure digital vault for protecting and managing your passwords, as well as other secret information. Keeper password manager application supports Two-factor authentication and available for every major operating system.
There is also an important security feature, called Self-destruct, which if enabled, will delete all records from your device if the incorrect master password is entered more than five times incorrectly.
But you don’t need worry, as this action will not delete the backup records stored on Keeper’s Cloud Security Vault.
Download Keeper Password Manager: Windows, Linux and Mac | iOS | Android | Kindle
2. Dashlane Password Manager (Cross-Platform)
DashLane Password Manager software is a little newer, but it offers great features for almost every platform.
DashLane password manager works by encrypting your personal info and accounts’ passwords with AES-256 encryption on a local machine, and then syncs your details with its online server, so that you can access your accounts database from anywhere.
The best part of DashLane is that it has an automatic password changer that can change your accounts’ passwords for you without having to deal with it yourself.
DashLane Password Manager app for Android gives you the secure password management tools right to your Android phone: your password vault and form auto-filler for online stores and other sites.
DashLane Password Manager app for Android is completely free to use on a single device and for accessing multiple devices, you can buy a premium version of the app.
Download DashLane Password Manager: Windows and Mac | iOS | Android
3. LastPass Password Manager (Cross-Platform)
LastPass is one of the best Password Manager for Windows users, though it comes with the extension, mobile app, and even desktop app support for all the browsers and operating systems.
LastPass is an incredibly powerful cloud-based password manager software that encrypts your personal info and accounts’ passwords with AES-256 bit encryption and even offers a variety of two-factor authentication options in order to ensure no one else can log into your password vault.
LastPass Password Manager comes for free as well as a premium with a fingerprint reader support.
Download LastPass Password Manager: Windows, Mac, and Linux | iOS | Android
Best Password Manager for Mac OS X
People often say that Mac computers are more secure than Windows and that “Macs don’t get viruses,” but it is not entirely correct.
As proof, you can read our previous articles on cyber attacks against Mac and iOs users, and then decide yourself that you need a password manager or not.
Some other best password manager for Mac OS X: 1Password, Dashlane, LastPass, OneSafe, PwSafe.
1. LogMeOnce Password Manager (Cross-Platform)
LogMeOnce Password Management Suite is one of the best password manager for Mac OS X, as well as syncs your passwords across Windows, iOS, and Android devices.
LogMeOnce is one of the best Premium and Enterprise Password Management Software that offers a wide variety of features and options, including Mugshot feature.
If your phone is ever stolen, LogMeOnce Mugshot feature tracks the location of the thief and also secretly takes a photo of the intruder when trying to gain access to your account without permission.
LogmeOnce protects your passwords with military-grade AES-256 encryption technology and offers Two-factor authentication to ensure that even with the master password in hand, a thief hacks your account.
Download LogMeOnce Password Manager: Windows and Mac | iOS | Android
2. KeePass Password Manager (Cross-Platform)
Although LastPass is one of the best password manager, some people are not comfortable with a cloud-based password manager.
KeePass is a popular password manager application for Windows, but there are browser extensions and mobile apps for KeePass as well.
KeePass password manager for Windows stores your accounts’ passwords on your PC, so you remain in control of them, and also on Dropbox, so you can access it using multiple devices.
KeePass encrypts your passwords and login info using the most secure encryption algorithms currently known: AES 256-bit encryption by default, or optional, Twofish 256-bit encryption.
KeePass is not just free, but it is also open source, which means its code and integrity can be examined by anyone, adding a degree of confidence.
Download KeePass Password Manager: Windows and Linux | Mac | iOS | Android
3. Apple iCloud Keychain
Apple introduced the iCloud Keychain password management system as a convenient way to store and automatically sync all your login credentials, Wi-Fi passwords, and credit card numbers securely across your approved Apple devices, including Mac OS X, iPhone, and iPad.
Your Secret Data in Keychain is encrypted with 256-bit AES (Advanced Encryption Standard) and secured with elliptic curve asymmetric cryptography and key wrapping.
Also, iCloud Keychain generates new, unique and strong passwords for you to use to protect your computer and accounts.
Major limitation: Keychain doesn’t work with other browsers other than Apple Safari.
Also Read: How to Setup iCloud Keychain?
Best Password Manager for Linux
No doubt, some Linux distributions are the safest operating systems exist on the earth, but as I said above that adopting Linux doesn’t completely protect your online accounts from hackers.
There are a number of cross-platform password managers available that sync all your accounts’ passwords across all your devices, such as LastPass, KeePass, RoboForm password managers.
Here below I have listed two popular and secure open source password managers for Linux:
1. SpiderOak Encryptr Password Manager (Cross-Platform)
SpiderOak’s Encryptr Password Manager is a zero-knowledge cloud-based password manager that encrypts protect your passwords using Crypton JavaScript framework, developed by SpiderOak and recommended by Edward Snowden.
It is a cross-platform, open-Source and free password manager that uses end-to-end encryption and works perfectly for Ubuntu, Debian Linux Mint, and other Linux distributions.
Encryptr Password Manager application itself is very simple and comes with some basic features.
Encryptr software lets you encrypt three types of files: Passwords, Credit Card numbers and general any text/keys.
Download Encryptr Password Manager: Windows, Linux and Mac | iOS | Android
2. EnPass Password Manager (Cross-Platform)
Enpass is an excellent security oriented Linux password manager that works perfectly with other platforms too. Enpass offers you to backup and restores stored passwords with third-party cloud services, including Google Drive, Dropbox, OneDrive, or OwnCloud.
It makes sure to provide the high levels of security and protects your data by a master password and encrypted it with 256-bit AES using open-source encryption engine SQLCipher, before uploading backup onto the cloud.
“We do not host your Enpass data on our servers. So, no signup is required for us. Your data is only stored on your device,” EnPass says.
Additionally, by default, Enpass locks itself every minute when you leave your computer unattended and clears clipboard memory every 30 seconds to prevent your passwords from being stolen by any other malicious software.
Download EnPass Password Manager: Windows, Linux | Mac | iOS | Android
3. RoboForm Password Manager (Cross-Platform)
You can easily find good password managers for Windows OS, but RoboForm Free Password Manager software goes a step further.
Besides creating complex passwords and remembering them for you, RoboForm also offers a smart form filler feature to save your time while browsing the Web.
RoboForm encrypts your login info and accounts’ passwords using military grade AES encryption with the key that is obtained from your RoboForm Master Password.
RoboForm is available for browsers like Internet Explorer, Chrome, and Firefox as well as mobile platforms with apps available for iOS, Android, and Windows Phone.
Download RoboForm Password Manager: Windows and Mac | Linux | iOS | Android
Best Password Manager for Android
More than half of the world’s population today is using Android devices, so it becomes necessary for Android users to secure their online accounts from hackers who are always seeking access to these devices.
Some of the best Password Manager apps for Android include 1Password, Keeper, DashLane, EnPass, OneSafe, mSecure and SplashID Safe.
1. 1Password Password Manager (Cross-Platform)
1Password Password Manager app for Android is one of the best apps for managing all your accounts’ passwords.
1Password password manager app creates strong, unique and secure passwords for every account, remembers them all for you, and logs you in with just a single tap.
1Password password manager software secures your logins and passwords with AES-256 bit encryption, and syncs them to all of your devices via your Dropbox account or stores locally for any other application to sync if you choose.
Recently, the Android version of 1Password password manager app has added Fingerprint support for unlocking all of your passwords instead of using your master password.
Download 1Password Password Manager: Windows and Mac | iOS | Android
2. mSecure Password Manager (Cross-Platform)
Like other popular password manager solutions, mSecure Password Manager for Android automatically generates secure passwords for you and stores them using 256-bit Blowfish encryption.
The catchy and unique feature mSecure Password Manager software provides its ability to self-destruct database after 5, 10, or 20 failed attempts (as per your preference) to input the right password.
You can also sync all of your devices with Dropbox, or via a private Wi-Fi network. In either case, all your data is transmitted safely and securely between devices regardless of the security of your cloud account.
Download mSecure Password Manager software: Windows and Mac | iOS | Android
Best Password Manager for iOS
As I said, Apple’s iOS is also prone to cyber attacks, so you can use some of the best password manager apps for iOS to secure your online accounts, including Keeper, OneSafe, Enpass, mSecure, LastPass, RoboForm, SplashID Safe and LoginBox Pro.
1. OneSafe Password Manager (Cross-Platform)
OneSafe is one of the best Password Manager apps for iOS devices that lets you store not only your accounts’ passwords but also sensitive documents, credit card details, photos, and more.
OneSafe password manager app for iOS encrypts your data behind a master password, with AES-256 encryption — the highest level available on mobile — and Touch ID. There is also an option for additional passwords for given folders.
OneSafe password manager for iOS also offers an in-app browser that supports autofill of logins, so that you don’t need to enter your login details every time.
Besides this, OneSafe also provides advanced security for your accounts’ passwords with features like auto-lock, intrusion detection, self-destruct mode, decoy safe and double protection.
Download OneSafe Password Manager: iOS | Mac | Android | Windows
2. SplashID Safe Password Manager (Cross-Platform)
SplashID Safe is one of the oldest and best password manager tools for iOS that allows users to securely store their login data and other sensitive information in an encrypted record.
All your information, including website logins, credit card and social security data, photos and file attachments, are protected with 256-bit encryption.
SplashID Safe Password Manager app for iOS also provides web autofill option, meaning you will not have to bother copy-pasting your passwords in login.
The free version of SplashID Safe app comes with basic record storage functionality, though you can opt for premium subscriptions that provide cross-device syncing among other premium features.
Download SplashID Safe Password Manager: Windows and Mac | iOS | Android
3. LoginBox Pro Password Manager
LoginBox Pro is another great password manager app for iOS devices. The app provides a single tap login to any website you visit, making the password manager app as the safest and fastest way to sign in to password-protected internet sites.
LoginBox Password Manager app for iOS combines a password manager as well as a browser.
From the moment you download it, all your login actions, including entering information, tapping buttons, checking boxes, or answering security questions, automatically completes by the LoginBox Password Manager app.
For security, LoginBox Password Manager app uses hardware-accelerated AES encryption and passcode to encrypt your data and save it on your device itself.
Download LoginBox Password Manager: iOS | Android
Best Online Password Managers
Using an online password manager tool is the easiest way to keep your personal and private information safe and secure from hackers and people with malicious intents.
Here I have listed some of the best online password managers that you can rely on to keep yourself safe online:
1. Google Online Password Manager
Did you know Google has its homebrew dedicated password manager?
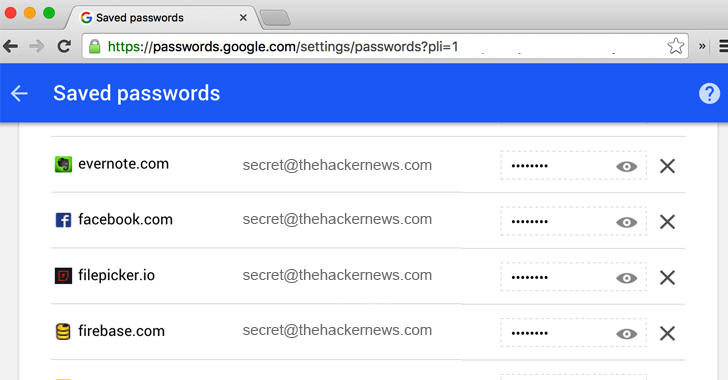
Google Chrome has a built-in password manager tool that offers you an option to save your password whenever you sign in to a website or web service using Chrome.
All of your stored accounts’ passwords are synced with your Google Account, making them available across all of your devices using the same Google Account.
Chrome password manager lets you manage all your accounts’ passwords from the Web.
So, if you prefer using a different browser, like Microsoft Edge on Windows 10 or Safari on iPhone, just visit passwords.google.com, and you’ll see a list of all your passwords you have saved with Chrome. Google’s two-factor authentication protects this list.
2. Clipperz Online Password Manager
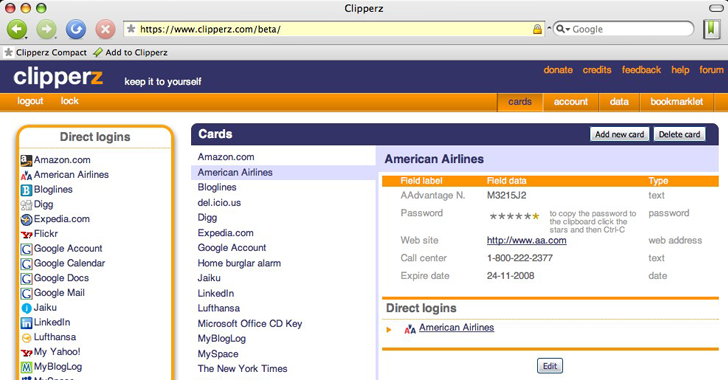
Clipperz is a free, cross-platform best online password manager that does not require you to download any software. Clipperz online password manager uses a bookmarklet or sidebar to create and use direct logins.
Clipperz also offers an offline password manager version of its software that allows you to download your passwords to an encrypted disk or a USB drive so you can take them with you while traveling and access your accounts’ passwords when you are offline.
Some features of Clipperz online password manager also includes password strength indicator, application locking, SSL secure connection, one-time password and a password generator.
Clipperz online password manager can work on any computer that runs a browser with a JavaScript browser.
3. Passpack Online Password Manager
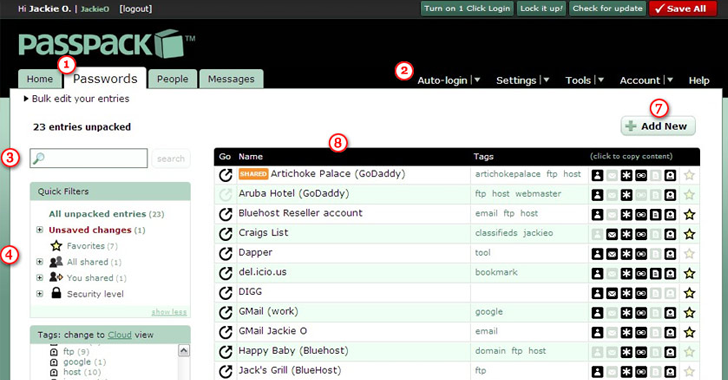
Passpack is an excellent online password manager with a competitive collection of features that creates, stores and manages passwords for your different online accounts.
PassPack online password manager also allows you to share your passwords safely with your family or coworkers for managing multiple projects, team members, clients, and employees easily.
Your usernames and passwords for different accounts are encrypted with AES-256 Encryption on PassPack’s servers that even hackers access to its server can not read your login information.
Download the PassPack online password manager toolbar to your web browser and navigate the web normally.
Whenever you log into any password-protected site, PassPack saves your login data so that you do not have to save your username and password manually on its site.
Best Enterprise Password Manager
Over the course of last 12 months, we’ve seen some of the biggest data breaches in the history of the Internet and year-over-year the growth is heating up.
According to statistics, a majority of employees even don’t know how to protect themselves online, which led company’s business at risk.
To keep password sharing mechanism secure in an organization, there exist some password management tools specially designed for enterprises use, such as Vaultier, CommonKey, Meldium, PassWork, and Zoho Vault.
1. Meldium Enterprise Password Manager Software
LogMeIn’s Meldium password management tool comes with a one-click single sign-on solution that helps businesses access to web apps securely and quickly.
It automatically logs users into apps and websites without typing usernames and passwords and also tracks password usage within your organization.
Meldium password manager is perfect for sharing accounts within your team member without sharing the actual password, which helps organizations to protect themselves from phishing attacks.
2. Zoho Vault Password Management Software
Zoho Vault is one of the best Password Manager for Enterprise users that helps your team share passwords and other sensitive information fast and securely while monitoring each user’s usage.
All your team members need to download is the Zoho browser extension. Zoho Vault password manager will automatically fill passwords from your team’s shared vault.
Zoho Vault also provides features that let you monitor your team’s password usage and security level so that you can know who is using which login.
The Zoho Vault enterprise-level package even alerts you whenever a password is changed or accessed.
For Extra Security, Use 2-Factor Authentication
No matter how strong your password is, there still remains a possibility for hackers to find some or the other way to hack into your account.
Two-factor authentication is designed to fight this issue. Instead of just one password, it requires you to enter the second passcode which is sent either to your mobile number via an SMS or to your email address via an email.
So, I recommend you to enable two-factor authentication now along with using a password manager software to secure your online accounts and sensitive information from hackers.
via: thehackernews