Google Calendar is the latest Google app to get an update focused on improving users’ “digital wellbeing.” The company announced today it’s rolling out a new “Out of Office” feature in Google Calendar, alongside a setting for customizable working hours. The working hours signal to others when you’re unavailable, and allows Google Calendar to automatically decline meetings on your behalf outside those hours.
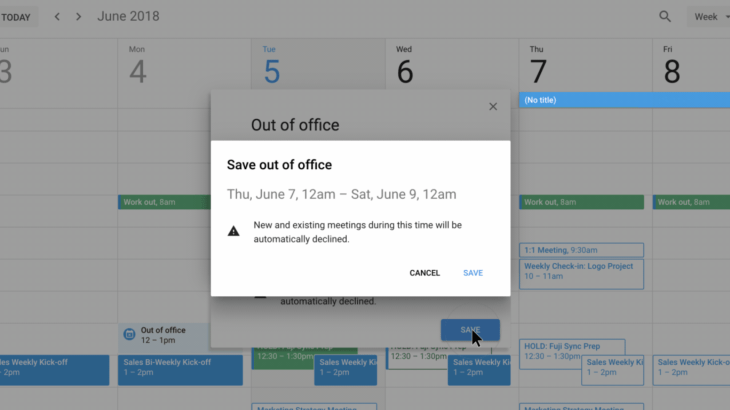
For starters, you’ll find there’s a new “Out of Office” calendar entry type you can select when you’re creating an event via Google Calendar on the web.
For example, if you’re scheduling the dates of your vacation, you could mark that event as “Out of Office.” If others send you meeting invites during this period, Google Calendar will decline them without your involvement.
It’s a feature users have requested for years to complement Gmail’s Vacation Responder.
Google also says it will attempt to automatically detect when event types should be denoted “Out of Office,” based on the event title.
Another new feature will allow you to better customize your working hours in Google Calendar.
Currently, you can set working hours to one interval for all days of the week, but now you’ll be able to customize your hours for each day separately. This will help people who have irregular availability — not the usual 9 to 5, so to speak.
Google Calendar will also try to infer your working hours based on your prior scheduling patterns, and may prompt you to confirm them in the app’s Settings.

The changes, while seemingly small, are part of a broader movement at Google to promote digital wellbeing across its platforms.
In recent months, the company has introduced a number of features focused on helping people better manage their time, and fight back against the addictive nature of smartphones and digital services.
For example, at its I/O developer conference in May, Google introduced new time management controls for Android users, and it has a set of screen time tools for parents to use with children via Family Link.
It even rolled out new tools to help YouTube users cut down the time they spend mindlessly watching videos.
Other services, like Gmail and Google Photos, utilize machine learning and AI to reduce the time spent in-app, by doing things like prioritizing the important mail, or automatically editing your photos.
The new Google Calendar tools are rolling out now to G Suite users, Google says. Presumably, a broader consumer release will soon follow.
via: techcrunch