Apple has now joined a host of merchants (Major retailers like Amazon, Ebay, and Walmart immediately jumped on board and have now removed confederate flags from their listings. The sheer ridiculousness of the move is noted that while Amazon has removed memorabilia featuring the flag of the Confederacy, they continue to allow the sale of items featuring Nazi emblems and Swastikas.) in removing the Confederate flag from its platform – in its case, the iTunes App Store. Several app developers are now reporting that their Civil War games, which featured imagery of the flag as part of their game’s historical context, have been pulled from the App Store.
Apple’s move to ban these games follows similar decisions by a number of major retailers, including Amazon, Walmart, eBay, Sears and others, which all announced bans on the sale of Confederate flag merchandise in the wake of the shooting deaths of nine black parishioners at a church in Charleston, S.C., this month.
UPDATE #1 – 6/25, 4 PM ET: Apple has now commented on the matter, saying:
“We have removed apps from the App Store that use the Confederate flag in offensive or mean-spirited ways, which is in violation of our guidelines. We are not removing apps that display the Confederate flag for educational or historical uses.”
UPDATE #2 – 6/25, 5 PM ET: We’ve spoken to Apple more extensively about the removals now. The company says it’s working with developers to quickly get their games reinstated to the App Store.
It seems like the removals were not a blanket ban on use of the Confederate flag imagery in App Store apps. And there may have been titles that shouldn’t have been pulled because the use of the flag could be considered “historical” or “educational,” as per Apple’s comment above. Apple’s intention is not to lose games from the App Store, but rather remove those titles that could offend. That means there will be some apps that are not likely to be reinstated, such as the banned Confederate flag wallpaper app, for example.
Original post continues below –
Currently, affected titles include Ultimate General: Gettysburg; several Hunted Cow/HexWar Games Civil War games; and more. The ban has also affected select apps, like “Southern Pride (Rebel Flag) Wallpaper,” it’s been noted.
According to at least one game developer Touch Arcade spoke with, their game was removed because it contained “images of the Confederate flag used in offensive and mean-spirited ways.” We’ve confirmed with others that this is the language Apple is using when referencing the removals.
Many developers argue that their games aren’t meant to be offensive, but rather include the flag imagery because of its historical context. Maxim Zasov of Game Labs, which publishes Ultimate General: Gettysburg, told Touch Arcade that teachers have used his game when teaching the Civil War in the classroom.
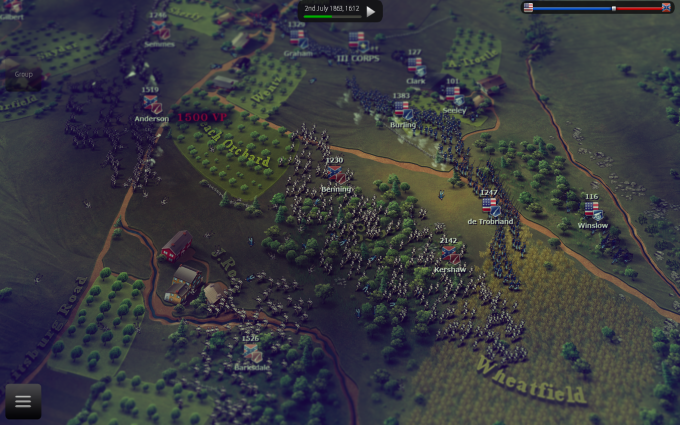
Adds Hunted Cow/HexWar Games director Andrew Mulholland, “it seems disappointing that [Apple] would remove [the games] as they weren’t being used in an offensive way, being that they were historical war games and hence it was the flag used at the time.”
Elsewhere on Reddit, an unnamed developer also reports that 14 titles from a game studio they work with have been removed.
It’s unclear what criteria Apple is using to determine whether it pulls an app featuring the Confederate flag imagery. But Mulholland tells us that Apple contacted his company after pulling several of its titles, and pointed to section 19.1 of the App Store Review Guidelines in its email. This section states:
“Apps containing references or commentary about a religious, cultural or ethnic group that are defamatory, offensive, mean-spirited or likely to expose the targeted group to harm or violence will be rejected.”
The company advised HexWar (which grew out of a collaboration between Hunted Cow and the original HexWar), to “review its app concept and incorporate different content and features that are in compliance the guidelines.” The company offers several Civil War-themed games which have been banned, including Civil War: 1862, Civil War: 1863, Civil War: 1864 and Civil War: Gettysburg. The oldest game, Civil War: 1863, has been live on the App Store since September 2012.
Hunted Cow/HexWar says they will now try resubmitting its titles using a lesser-known 1861 version of the flag to see if their games will be approved.
The Apple bannings don’t seem to be universal, however. Ars Technica points out there are other titles that include the image of the flag that are still live on the App Store, like The Battle of Antietam and The History Channel’s The Civil War Today. Plus, Apple continues to sell other media that showcases the Confederate flag, including albums and TV shows like Primal Scream’s Give Out But Don’t Give Up, Legend by Lynyrd Skynyrd and seven seasons of Dukes of Hazzard, as The Guardian notes.
In addition, The Guardian also remarks that Apple’s decision to enforce the Confederate flag ban contradicts how it handles other offensive materials, like the Nazi flag. Several titles (including those that don’t claim historical accuracy) that feature this flag remain available.
The question, apparently, is where does Apple draw the line with regard to the removal of the Confederate flag, or any offensive flag, from its storefront?
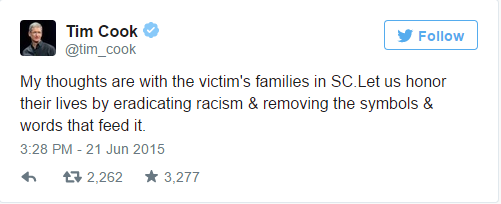
Apple CEO Tim Cook recently tweeted his support for measures that involve removing the symbols of racism, so it’s not entirely surprising to see the company take this step.
Via: techcrunch