One of the recent triumphs against cybercrime is the disruption of the activities of the Gameover ZeuS botnet. Perhaps what makes this more significant is that one major threat was also affected—the notorious CryptoLocker malware.
However, this disruption hasn’t deterred cybercriminals from using file-encrypting ransomware. In fact, we saw new crypto-ransomware variants that use new methods of encryption and evasion.
Cryptoblocker and its Encryption Technique
Just like other ransomware variants, the Cryptoblocker malware, detected as TROJ_CRYPTFILE.SM, will encrypt files for a specific amount. However, this particular variant has certain restrictions. For one, it will not infect files larger than 100MB in size. Additionally, it will also skip files found the folders C:\\WINDOWS, C:\\PROGRAM FILES, and C:\PROGRAM FILES (X86).
And unlike other ransomware variants, Cryptoblocker will not drop any text files instructing the victim on how to decrypt the files. Rather, it displays the dialog box below. Entering a transaction ID in the text box will trigger a message stating that the “transaction was sent and will be verified soon.”
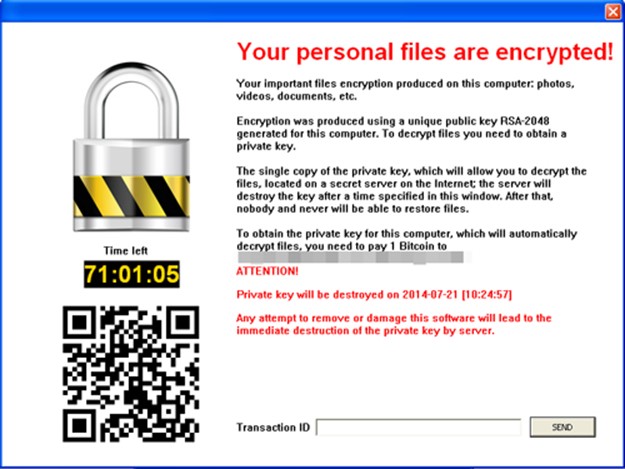
Figure 1. Dialog box
Another distinction is that its encryption routine. This malware does not use CryptoAPIs, a marked difference from other ransomware. CryptoAPIs are used to make RSA keys, which were not used with this particular malware. This is an interesting detail considering RSA keys would make decrypting files more difficult. Instead, we found that the advanced encryption standard (AES) is found in the malware code.
A closer look also reveals that the compiler notes were still intact upon unpacking the code. This is highly interesting as compiler notes are usually removed. This is because this information could be used by security researchers to detect (and thereby block) files from the malware writer. The presence of the compiler notes would suggest that perhaps the bad guy behind Cryptoblocker is new to the creation of ransomware.
Based on feedback from the Trend Micro Smart Protection Network, the US is the top affected country, followed by France and Japan. Spain and Italy round up the top five affected countries.
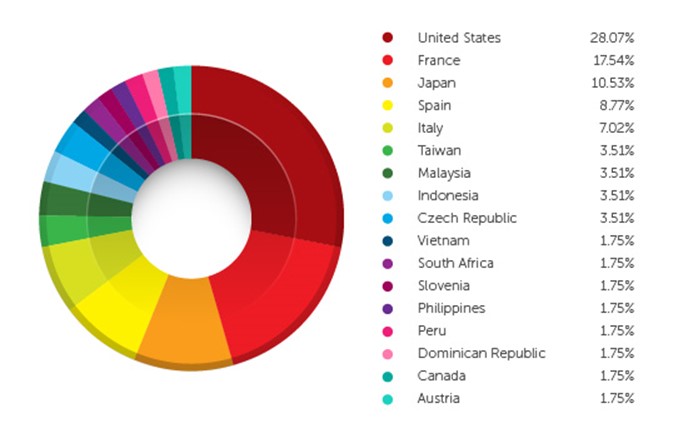
Figure 2. Countries affected by Cryptoblocker
Critroni and the Use of Tor
The Tor network has gained a lot of attention due to its association with cybercrime. Cybercriminals have been using the network to mask their malicious activity and hide from law enforcement agencies.
We recently came across one variant, detected as TROJ_CRYPCTB.A and known as Critroni or Curve-Tor-Bitcoin (CTB) Locker, which uses Tor to mask its command-and-control (C&C) communications. After encrypting the files of the affected machine, the malware changes the computer’s wallpaper to the image below:
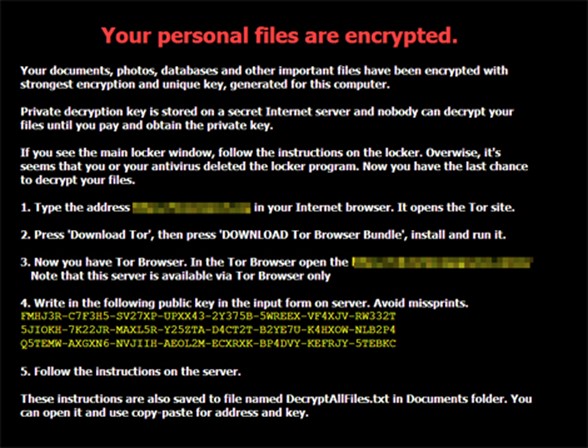
Figure 3. Wallpaper displayed
It also displays a ransom message. Users must pay the ransom in Bitcoins before the set deadline is done. Otherwise, all the files will permanently remain encrypted.
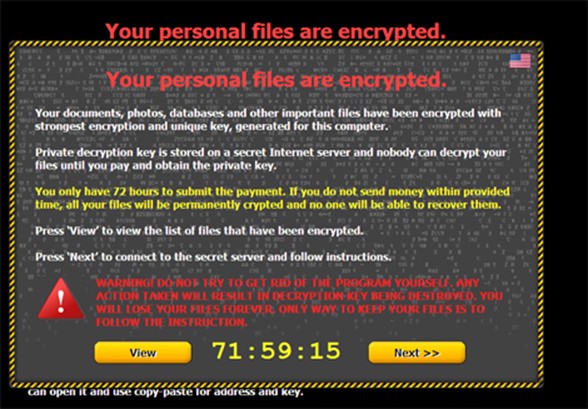
Figure 4. Ransom message
According senior threats researcher Jamz Yaneza, this malware uses the elliptic curve cryptography in comparison to using RSA or AES. To put this into context, the Bitcoin ecosystem relies on one elliptic curve cryptographic schemes, the Elliptic Curve Digital Signature Algorithm (ECDSA).
This isn’t the first time we have seen ransomware take advantage of the anonymity offered by the Tor network. In the last weeks of 2013, ransomware variants called Cryptorbit asked their victims to use the Tor browser (a browser pre-configured for Tor) for ransom payment. We also came across Android ransomware that uses Tor for its C&C communications.
BAT_CRYPTOR.A Uses Legitimate Apps
Last June, we reported about POSHCODER, a ransomware variant that abuses the Windows PowerShell feature to encrypt files. We recently spotted yet another ransomware that, like POSHCODER, uses legitimate apps for its encryption routine.
Detected as BAT_CRYPTOR.A, this variant uses the GNU Privacy Guard application to encrypt files. However, based on our analysis, the malware will still execute its encryption routines even if the system does not have GnuPG. As part of its infection chain, the dropper malware will drop a copy of GnuPG to use for encryption. The said routine is written in batch file.
The malware will delete the %appdata%/gnupg/*, which is the directory wherein generated keys are saved. It will then generate new keys using genkey.like. Two keys will be generated, one public (pubring.gpg) and the other, private (secring.gpg).
The public key pubring.gpg will be used to encrypt the files on the system. The private key, which can decrypt the files, is left on the affected system. However, this key is also encrypted (using the key secrypt.like), making encryption difficult. The newly-encrypted private key will be renamed to KEY.PRIVATE.
BAT_CRYPTOR.A renames encrypted files with the file name {file name and extension}.paycrypt@gmail_com. In the ransom note, users are instructed to contact an email address for details on how to decrypt their files.
The Importance of Caution
These ransomware variants prove that despite significant takedowns, cybercriminals will continue to find ways to victimize users. Users should remain cautious when dealing with unfamiliar files, emails, or URL links. While it might be tempting to pay the ransom for encrypted files, there is no guarantee that the cybercriminals will decrypt the ransomed files. Users can read other security practices the blog entry, Dealing with CryptoLocker.
Via: trendmicro