Remember the recent payment card breach at Wawa convenience stores?
If you’re among those millions of customers who shopped at any of 850 Wawa stores last year but haven’t yet hotlisted your cards, it’s high time to take immediate action.
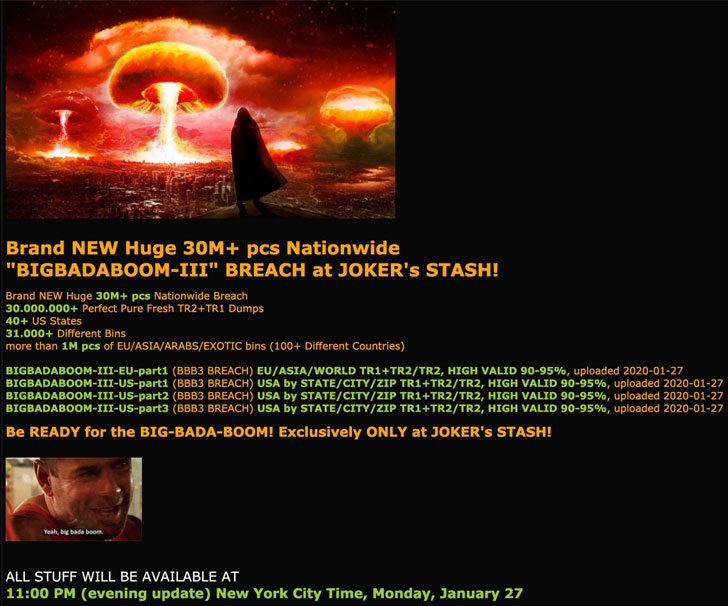
That’s because hackers have finally put up payment card details of more than 30 million Wawa breach victims on sale at Joker’s Stash, one of the largest dark web marketplaces where cybercriminals buy and sell stolen payment card data.
As The Hacker News reported last month, on 10th December Wawa learned that its point-of-sale servers had malware installed since March 2019, which stole payment details of its customers from potentially all Wawa locations.
At that time, the company said it’s not aware of how many customers may have been affected in the nine-month-long breach or of any unauthorized use of payment card information as a result of the incident.
Now it turns out that the Wawa breach marked itself in the list of largest credit card breaches ever happened in the history of the United States, potentially exposing 30 million sets of payment records.
According to threat intelligence firm Gemini Advisory, on 27th January 2020, hackers started uploading stolen payment card data from Wawa at Joker’s Stash marketplace, titled as ‘BIGBADABOOM-III,’ which reportedly includes card numbers, expiration dates, and cardholder names.
“While the majority of those records were from US banks and were linked to US-based cardholders, some records also linked to cardholders from Latin America, Europe, and several Asian countries,” Gemini Advisory said.
“Non-US-based cardholders likely fell victim to this breach when traveling to the United States and transacting with Wawa gas stations during the period of exposure.”
“The median price of US-issued records from this breach is currently $17, with some of the international records priced as high as $210 per card.”
In the latest statement released yesterday, Wawa confirmed that the company is aware of reports of criminal attempts to sell customers’ payment card data and to help further protect its customers, the company has ‘alerted payment card processors, payment card brands and card issuers to heighten fraud monitoring activities.’
“We continue to encourage our customers to remain vigilant in reviewing charges on their payment card statements and to promptly report any unauthorized use to the bank or financial institution that issued their payment card by calling the number on the back of the card,” Wawa said.
Customers who bought anything from any of the Wawa convenience stores between March and December last year are advised to block the affected cards and request a new one from your respective financial institution.
via: thehackernews