Centrify Backs “Bring Your Own Mac” Initiatives with Day One Support and Interoperability of New Mac Mavericks Operating System — Leading Active Directory-based Solution for Identity and Access Management of Mac and Mobile Devices Supports Apple’s New Mac OS X 10.9 Mavericks OS Released
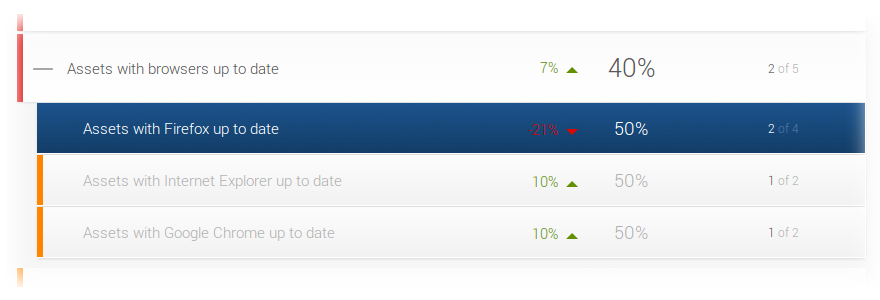
Centrify Corporation, the leader in Unified Identity Services across data center, cloud and mobile , announced that its Centrify User Suite offering supports the just-released Apple OS X 10.9 Mavericks operating system for Macs, enabling organizations to leverage Centrify’s proven Active Directory-based security service to manage users and devices and address enterprise mobility and BYOD challenges, including “Bring Your Own Mac.” The Centrify User Suite solution maximizes security and visibility through centralized access management and reporting of enrolled devices and installed applications, allowing IT staff to quickly and securely bring large populations of Macs and Apple and Android devices under management by leveraging existing Active Directory identity infrastructure and skill sets.
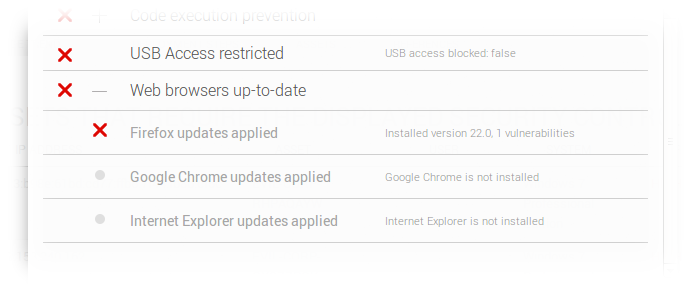
With Centrify User Suite, Mac Edition (“Centrify for Mac”), both on-premise and remote Macs and mobile devices are seamlessly integrated into Microsoft Active Directory, leveraging organizations’ existing AD infrastructures, processes and skill sets to deliver enhanced security and centralized management for IT; and secure, single sign-on access for Mac users at work. This unparalleled integration with an organization’s on-premise Active Directory infrastructure and Group Policy-based management tools makes it easy to enforce and update Mac and mobile security settings. From locking or remotely wiping devices to securing access to email networks and enforcing use of passcodes, the Centrify solution enables administrators to easily assign devices to users and manage the associated properties and settings for each user’s device without the hassle of deploying complex new infrastructure or a separate management console.
“The fact that Apple is increasing the security of its Mac platform and is making it even better for the enterprise use will further fuel the rapid growth of Macs operating in organizations today, both company owned and personally owned devices,” said David McNeely, Centrify senior director of product management. “With Centrify for Mac, we make it just as easy to manage Mac workforces as it is to manage Windows users with Group Policy. And for Mac users, we are the first to add Single Sign-On to all their approved enterprise services and applications. Customers appreciate Centrify’s commitment for continued ‘day one’ support of every new Apple operating system release.”
Centrify’s day one support includes Smart Card (CAC, CAC NG, PIV and PIV-I) login support on OS X 10.9, ensuring strong authentication and single sign-on to other applications and services for Active Directory users. Smart card login combined with Centrify’s ability to enforce security policies required in high security environments helps to ensure compliance with corporate and federal policies, enabling further adoption of Mac OS X 10.9 systems in these environments. Additional features such as user self-service support enable users to upgrade, wipe or lock devices themselves without involving IT, reducing overall IT costs.
Availability
Centrify support for the Apple OS X 10.9 Mavericks release is available as part of the Centrify User Suite, Mac Edition. For more information, see http://www.centrify.com/mac.