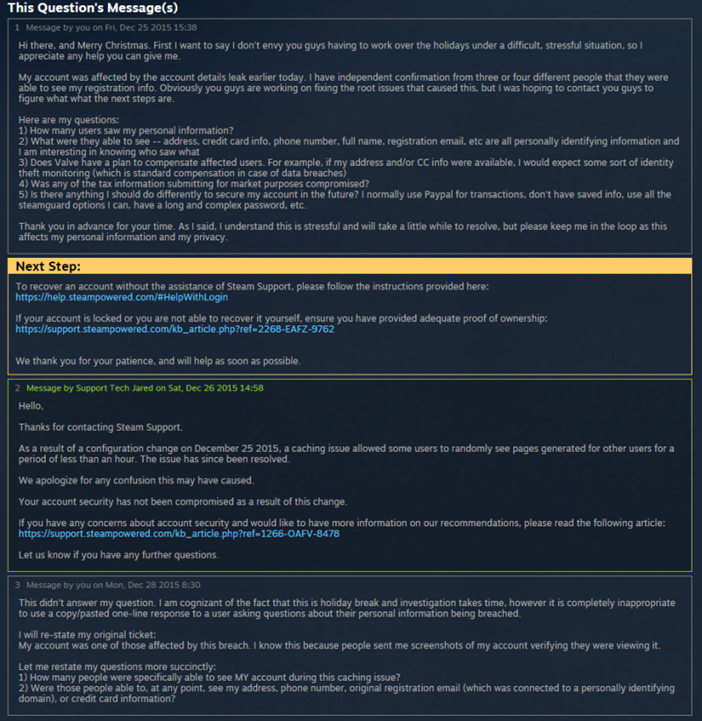
Gone are the days of the 40-hour work week that kept us at work eight hours a day (I find that most startup founders or business owners in Silicon Valley work 50-60 hours a week).
Freelancing is becoming the accepted norm of the startup world. As more startups are starting to use the millions of freelancers, it’s driving more and more people to join the freelancer generation.
Regardless if you’re a startup or enterprise, it’s in your best interest to pay attention to the freelance movement if you want to succeed in this new economy.
The Freelancer Generation Is Booming
Recent research states there are more than 53 million (almost 54 Million) freelancers in the U.S.; it’s quickly becoming one of the largest workforces. Indeed, more than one-third of all U.S. workers have partaken in freelance work in the past year. Compared to the previous year, that’s more than 700,000 new freelancers.
It’s also predicted that by 2020, contingent work (freelancing jobs) will become the dominant form of labor, making up to 50 percent of the labor force. Another interesting stat is that 43 percent of freelancers are Millennials. That’s important to know, because 1 in 3 American workers today are Millenials.
This is in part due to: advances in technology that allow increased remote work; an increasing digital economy; a growing part-time workforce; and labor force gains and losses.
Furthermore, people have realized they can thrive financially as freelancers, enjoy the flexible schedules that can create a favorable work-life balance and easily promote their services to potential clients.
Business owners soon may not have many other options when looking for top talent, as a majority of the workforce will be freelancers in the very near future. This is factoring in all the freelancers who have a full-time job and are working on the side (this is how I found my last technical business partner, which worked out well for us both).
Freelancers Are Politically Active
Freelancers are typically satisfied with their decision to leave behind the 40-hour work week. However, that doesn’t mean they don’t still face challenges that many traditional workers may take for granted.
For example, freelancers don’t have access to traditional programs like 401ks. They also must pay out-of-pocket for insurance and deal with high taxes for being self-employed. Because of this, freelancers are urging politicians to make a change — primarily income and insurance stability. Why wouldn’t they, if they are becoming such a large percentage of the American workforce?
It would be one thing for freelancers to demand a change and do nothing about it. The fact is, however, that freelancers are voicing their concerns to politicians. Of the almost 54 million freelancers in the country, an astounding 86 percent have claimed that they’re going to vote in the 2016 general election.
To put that into perspective, that figure is higher than the amount of voters who helped Ronald Reagan and Bill Clinton sweep their presidential elections. Additionally, 62 percent of freelancers would vote for a candidate who supports the interests of freelancers.
Whether it’s through changes in government regulations or staying competitive, businesses of all sizes need to be aware of the concerns facing freelancers and provide programs that address these challenges. It’s an important issue for most freelancers, and they’re actively making sure that these changes are implemented.
Freelancers Bring A Lot To The Table
For business owners like myself, especially startups, freelancers offer a wide range of benefits that most full-time employees don’t. For starters, freelancers understand the everyday tasks and challenges that business owners face. They’re at least somewhat familiar with everything from bookkeeping, billing, branding, marketing and engaging an audience on social media. Because freelancers are their own bosses, they’re completely aware of these tasks and how important they are for the success of a business.
Unlike a recent graduate who probably has never had to be concerned with paying taxes, sending invoices or building and maintaining a brand, it is almost a guarantee that freelancers already have this type of experience.
A freelancer may be able to assist you in these areas as you’re launching your business. Even if you’re established, at least they are cognizant and respectful of these duties. For example, they won’t harm your brand by going on a social media tangent that offends your customers.
Another perk of hiring freelancers is that they are experts in their respective fields. They have years of experience, a portfolio and referrals to back-up their work. Even if they are young (which many are), they still are the best at what they do. Instead of just looking at a resume, you can dissect real-world examples of their work prior to bringing them on-board.
Whether it’s a copywriter, graphic designer, CPA, customer service rep or social media strategist, freelancers are seasoned pros within their niche and are ready to dive into the projects that you assign them. Best of all? You can search for the best talent from anywhere in the world, thanks to technology that allows freelancers to work remotely.
Finally, freelancers can help reduce costs. No matter the size of your business, the bottom line is always a concern. Freelancers can be a more affordable option than hiring a full-time employee. Remember, most freelancers work from home; you don’t have to train them; they’ll generally accept projects cheaper than salaried employees; and you don’t have to worry about taxes or retirement plans.
I’ve been able to successfully launch and grow my personal business with freelancers. I also like using freelancers because you pay for metrics that are measured. You want a blog post written for your company? You pay for the job or amount of words. If you need a programming job done (as I have in the past), you can get a quote based on the project and know you’re not going to spend more. It helps me get the best person in the world for that job and only pay for what I need, without committing full-time resources to it.
Via: techcrunch
 in
in