The risk of sophisticated malware, especially of ransomware, has grown exponentially over the years. This means we need to evolve our techniques for mitigation, detection and monitoring of malicious behavior on our assets. It’s a wise move given the durability of this threat. Indeed, the rise of ransomware, which attempts to scare users and organizations into paying a fee to retrieve their hijacked data, is on the rise and is something we’ll probably see for years to come.
To prevent ransomware from abusing our networks, multiple layers of protection are needed for complete coverage. These in include: (1) Pre-breach/Mitigation, (2) Active Breach, (3) Post-breach, (4) Active Monitoring, and (5) Tuning Current Configurations. Addressing these five layers in tandem allows for a comprehensive approach of defending an enterprise against malware.
PRE-BREACH/MITIGATION
The first step to defending against ransomware is to stop it as close to the endpoint as possible. This means working with an anti-virus vendor that’s properly configured to assist with defending the system against the abuse of malware.
With this being said, not all anti-virus is created equal. The old school mentality of using signatures to defend against malware has lost its edge when it comes to guarding systems against present-day malware. Investing in next-generation antivirus (NG-AV) that isn’t based on signatures but is instead predicated on machine learning and common attack locations assists with a higher rate of detection among anti-malware vendors.
In the meantime, there should be a review of your current anti-virus solutions to make sure you have security software installed and appropriately configured on all necessary systems.
Having anti-virus fine-tuned, even with a NG-AV, won’t always protect you from ransomware. That’s why using native internal policies on the endpoints to restrict where files can be installed can go a long way in defending against attacks.
ACTIVE BREACH
The second layer of defense when creating a malware defendable network is to have systems in place that will determine when an active breach is occurring. These systems are designed to catch threats that bypass malware protection on the endpoint (if the system has endpoint protection to begin with) and issue an alert when a breach is detected on the network.
This is done passively, either by setting up network taps within the core of the network and alerting on user baselines or by utilizing deception technology/decoys (honeypots/honeytokens) that alert to the presence of something that shouldn’t have touched them.
Active breach technology doesn’t stop threats, but it proactively notifies of an attack that’s currently underway. It will also assist with limiting the scope of a response against an attack. Since this doesn’t rely on agents, it gives a holistic view of what might have been missed with endpoint AV agents.
POST BREACH
The post-breach defense is closely tied to the active breach layer to determine exactly where the malware is in use. These systems are more forensically capable to start packet captures, look for known indicators of compromise (IoC) that are tied to the particular variant of ransomware, and give investigators the ability to pinpoint what other systems in the network have the same files (or IoCs) as the infected systems.
This is an incident response and forensic tool to be used to isolate systems that are truly infected, also known as Endpoint Detection and Response (EDR). Many of these systems are dependent on agents installed on them to accomplish this task with the exception of sandboxes, which is why the active breach technology assists with filling the holes of missing agents in this needed layer.
ACTIVE MONITORING
With the systems in place now to defend and alert against malware, the next piece of the design is to monitor the network 24×7. Since malware will many times lay dormant for days or weeks, there’s a need to be consistently looking at alerts and notifications that come from the malware protection systems which have been put in place.
Sending these logs to a third party SOC, or establishing an internal SOC to act on these alerts while they’re occurring, gives the greatest potential for success when it comes to defending against malware.
TUNING CURRENT CONFIGURATIONS
While advanced technology might currently not be in place (E.G NG-AV, network anomaly tools, forensic IoC, sandboxing, etc), there are still areas of improvement in the network that can be worked on to defend against malware.
This includes verifying all systems are patched (both third party and OS), determining that every system is running the appropriate current AV agents, tuning the AV policies to be more restrictive when it comes to scanning files, blocking servers from egressing to the internet, denying split tunneling on the VPN, forcing all systems through a proxy, and verifying that you have up-to-date spam detection, properly segmented networks, and most important of all backups of all your data.
CONCLUSION
Creating a network that’s impervious to ransomware, or malware in general, is almost impossible, but there are internal tunings of current systems that can assist with making it harder for malware to infect your network while you wait for the budget or implementation of more advanced technology.
There is no silver bullet when it comes to defending against malware, just the ability to block what you can and contain what gets in. The faster you can respond against something that slipped past your defenses, the better chance you have to mitigate the risk moving forward.
Via: tripwire
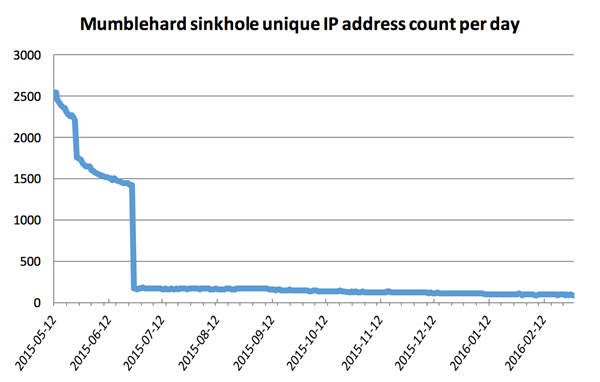 Statistics from Mumblehard sinkhole after the publication (Source: ESET)
Statistics from Mumblehard sinkhole after the publication (Source: ESET)