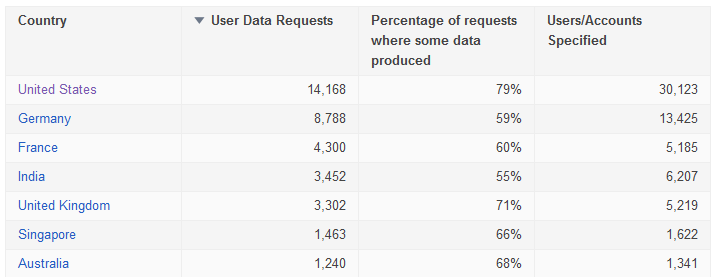
Challenging work, skills training and flexible work hours are important for the highest skilled workers.
Challenging work, skills training and flexible work hours are important for all cybersecurity employees, but especially so for the highest skilled workers, according to a report released today by the Center for Strategic and International Studies.
In addition, these employees were nearly twice as likely to want promotions that did not require them to move into management.
“We figured out who the cybersecurity ninjas were by asking people what their day-to-day tasks were,” said report author Katrina Timlin, an associate fellow in the center’s strategic technologies program.
Examples of tasks that ninjas perform more often are penetration testing, hunt team activities, security monitoring and event analysis, digital forensics, secure coding, and security engineering.
“Both sets of people had the priority of having important and challenging tasks,” she said. “But people with advanced skill sets wanted flexible work schedules and being able to get training and advance without having to go into management,” she said.
Specifically, 72 percent of ninjas and 71 percent of non-ninjas said that having engaging and challenging tasks were “very important.” And 72 percent of ninjas and 69 percent of non-ninjas said the same of having employer-provided training to keep their skills current.
The question of training came up during the interviews Timlin conducted for the report.
“One of the things that struck me was how much it would cost someone if they wanted to get the training, go to conferences, and get the certifications on their own,” she said. “One guy said he could easily spend $20,000 a year.”
Offering training opportunities could be one way to incentivize these highly skilled employees to join a company, and then to continue to retain those employees.
“That’s a major driving factor in being seen as a place where people want to work,” she said.
The gap between ninjas and non-ninjas grew wider when it came to flexible work schedules, with 67 percent of ninjas saying it was important to be able to set their own hours, compared to 52 percent of non-ninjas. And only 58 percent of ninjas said that competitive pay and benefits were very important, compared to 64 percent of non-ninjas.
“Our assumption with this is that the ninjas are already fairly well compensated,” said Timlin. “So some of these other factors make more of a different when finding a new job or staying with their current companies.”
The most dramatic gap was in the area of career advancement, where 46 percent said that they wanted to be able to get promotions while staying in technical jobs instead of moving to management. This was very important to only 26 percent of non-ninjas.
The report also asked employees about the traits that made companies particularly attractive. The top factors were being in an industry that prioritizes cybersecurity, offering exposure to diverse and high-impact projects, and having a mission that motivates employees.
And the top three factors that ninjas ranked as being most important in motivating them to stay with their job were having a variety of tasks instead of solving the same problem over and over again, having the time to explore new technologies, and being able to engage with other experts.
These factors can also help bring new people into cybersecurity, said Max Shuftan, business development manager of SANS CyberTalent Program at SANS Institute, which sponsored the report.
“There are only so many people in the field now,” he said.
In addition, flexible work schedules and ongoing training can help a company draw from a wider pool of talent, both geographically and in terms of gender.
“A lot of security professionals are job seekers [who] are very interested in a work-from-home model,” he added.
While this might not be easy to do with a traditional security operations center, consulting organizations often have staff who split their time between traveling to different work locations and working at from home offices.
Shuftan said he’s also talked with a number of people about how to make a work environment more challenging, and the most common recommendation was job rotation.
“For two years, you’ll be focused on incident handling,” he said. “For two years, on incident response. For two years, continuous monitoring or penetration testing. That keeps challenges coming and the employees motivated and positive.”
via: csoonline