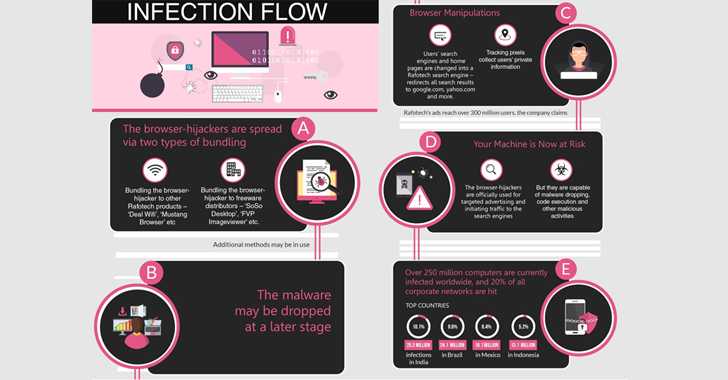
Security researchers have discovered a massive malware campaign that has already infected more than 250 million computers across the world, including Windows and Mac OS.
Dubbed Fireball, the malware is an adware package that takes complete control of victim’s web browsers and turns them into zombies, potentially allowing attackers to spy on victim’s web traffic and potentially steal their data.
Check Point researchers, who discovered this massive malware campaign, linked the operation to Rafotech, a Chinese company which claims to offer digital marketing and game apps to 300 million customers.
While the company is currently using Fireball for generating revenue by injecting advertisements onto the browsers, the malware can be quickly turned into a massive destroyer to cause a significant cyber security incident worldwide.
Fireball comes bundled with other free software programs that you download off of the Internet. Once installed, the malware installs browser plugins to manipulate the victim’s web browser configurations to replace their default search engines and home pages with fake search engines (trotux.com).
“It’s important to remember that when a user installs freeware, additional malware isn’t necessarily dropped at the same time.” researchers said. “Furthermore, it is likely that Rafotech is using additional distribution methods, such as spreading freeware under fake names, spam, or even buying installs from threat actors.”
The fake search engine simply redirects the victim’s queries to either Yahoo.com or Google.com and includes tracking pixels that collect the victim’s information.
Far from legitimate purpose, Fireball has the ability to spy on victim’s web traffic, execute any malicious code on the infected computers, install plug-ins, and even perform efficient malware dropping, which creates a massive security hole in targeted systems and networks.
“From a technical perspective, Fireball displays great sophistication and quality evasion techniques, including anti-detection capabilities, multi-layer structure, and a flexible C&C– it is not inferior to a typical malware,” researchers said.
At the current, Fireball adware is hijacking users’ web traffic to boost its advertisements and gain revenue, but at the same time, the adware has the capability to distribute additional malware.
“Based on our estimated infection rate, in such a scenario, one out of five corporations worldwide will be susceptible to a major breach,” researchers added.
According to researchers, over 250 million computers are infected worldwide, 20 percent of them are corporate networks:
- 25.3 million infections in India (10.1%)
- 24.1 million in Brazil (9.6%)
- 16.1 million in Mexico (6.4%)
- 13.1 million in Indonesia (5.2%)
- 5.5 million In US (2.2%)
“How severe is it? Try to imagine a pesticide armed with a nuclear bomb. Yes, it can do the job, but it can also do much more,” researchers warned. “Many threat actors would like to have even a fraction of Rafotech’s power.”
Warning Signs that Your Computer is Fireball-Infected
If the answer to any of the following questions is “NO,” that means your computer is infected with Fireball or a similar adware.
Open your web browser and check:
- Did you set your homepage?
- Are you able to modify your browser’s homepage?
- Are you familiar with your default search engine and can modify that as well?
- Do you remember installing all of your browser extensions?
To remove the adware, just uninstall the respective application from your computer (or use an adware cleaner software) and then restore/reset your browser configurations to default settings.
The primary way to prevent such infections is to be very careful when you agree to install.
You should always pay attention when installing software, as software installers usually include optional installs. Opt for custom installation and then de-select anything that is unnecessary or unfamiliar.
via: thehackernews