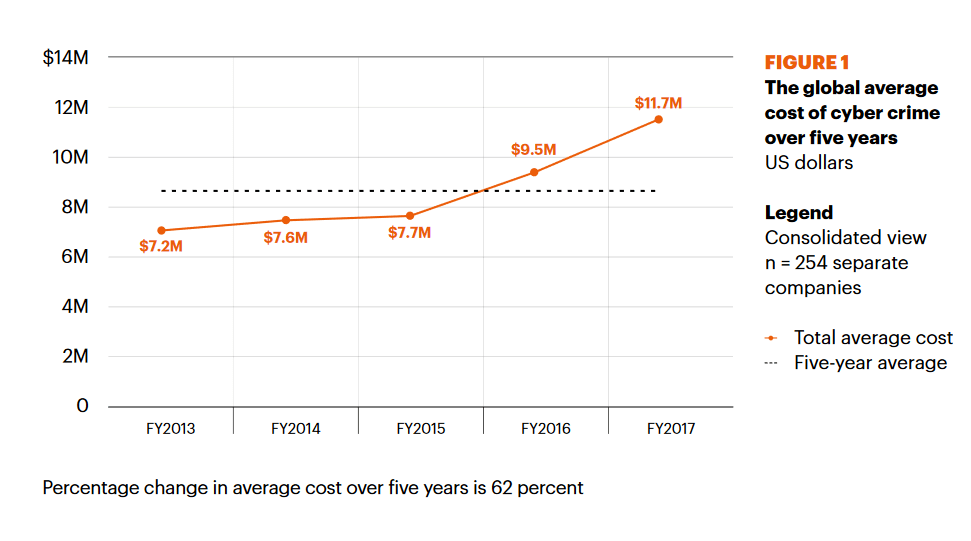Here’s how online criminals use the surprise factor to spread malware.
Cyber attacks continue to rise and impact both organizations and home users worldwide. Despite all the efforts and prevention measures taken by everyone, these attacks keep wreaking havoc, with no signs of slowing downs.
Why are these online threats still spreading? How do cyber criminals manage to change tactics during their attacks?
With these questions in mind, we will look into the threat landscape to see how malware authors have switched to more sophisticated attack vectors. They are now using more advanced and complex technology to find their next targets, infect various devices, and get access to users’ sensitive data.
Have you noticed that cyber criminals became ingenious during attacks and use a surprise factor?
This year, WannaCry was the largest global ransomware attack in the Internet history.
Why was this cyber attack a success for cyber criminals? What was different from the rest of attacks? It had a low detection rate. Attackers exploited a vulnerability in Windows system that allowed it to move laterally within networks and infect hundreds of computers. They used a leaked NSA exploit called EternalBlue, for quickly spreading malware and infecting a large number of computers.
This is just one of the examples that we’ll discuss in this article, so you can understand how online criminals are changing their ways.
How cyber attacks have evolved in 2017
So far, 2017 has proved to be a productive year for cybercriminals, as we witnessed a large number of new cyber attacks hitting the malware market. From the massive WannaCry ransomware of “unprecedented level” to the (non)Petya outbreak, from the historical Equifax data breach to the recent CCleaner incident; they come in all shapes and sizes, are difficult to be anticipated and cause a lot of damage.
It seems that this year cyber attacks are happening at a higher frequency than previous years, and still have a high impact rate. Everyone has been (and is) suffering from these large-scale attacks, whether they lose their valuable data or businesses are being disrupted. Everyone is vulnerable, but we can always learn to become more resilient to such attacks and take cyber security more seriously.
For example, the mid-year CheckPoint Research for 2017 found that most global regions have been hit by ransomware, already a mainstream and a widespread security threat.
The ransomware invasion has increased significantly this year with a big impact and causing data leakage/important financial loss for both organizations and home users. It continues to dominate the threat landscape and also affect important sectors such as hospitals, banks, universities, Government, law firms, mobile users.
The financial consequences of the cyber attacks don’t seem to be on a positive note, as the global average costs of cybercrime continue to increase. A recent “Cost of CyberCrime” Study conducted by Ponemon Institute and jointly developed by Accenture, has shown that cost of cybercrime is now 23 percent more than last year and is costing organizations, on average, US$11.7 million.
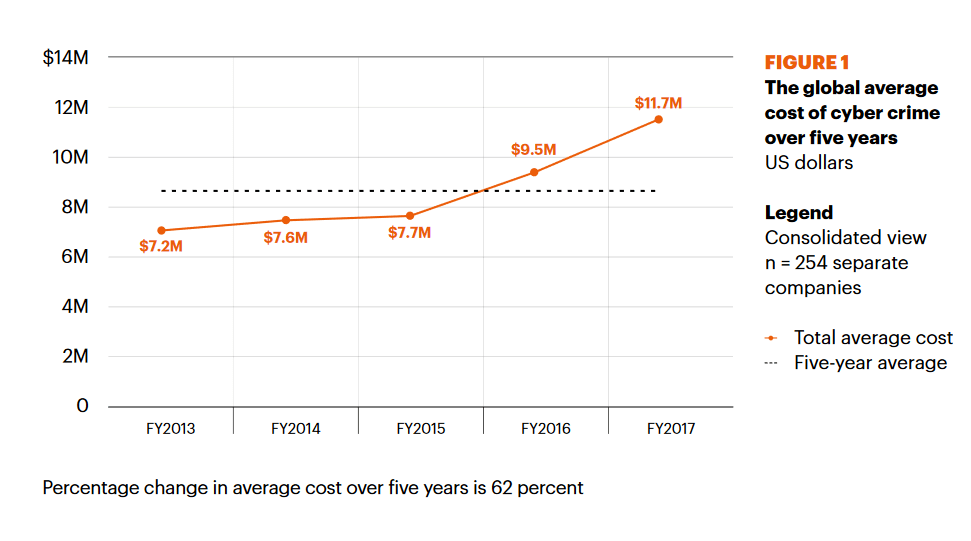
Source: Accenture
Inside the mind of cybercriminals
You might wonder: what’s inside the mind of a cyber criminal? What motivates these bad guys to take malicious actions and steal other people’s sensitive information? Is it just money or are they looking to show off?
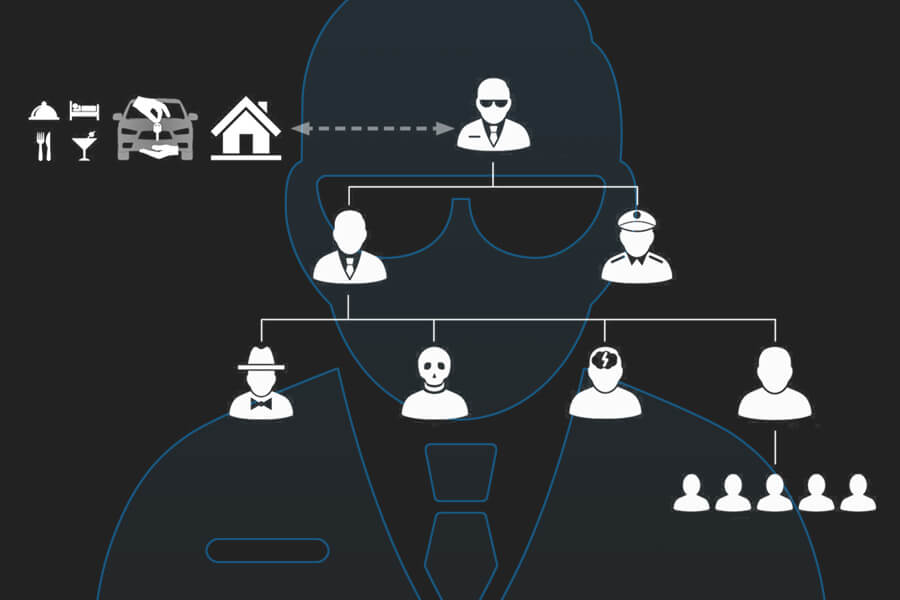
Source: Recordedfuture.com
Often, technology is being used against us, and not to our benefit, as expected. This happens with skilled people who are tech-savvy and know how to operate efficiently.They can reach these days further than before, into our private lives, our homes or work offices. And most of the time, we can’t do nothing about it.
Here’s how hackers approach an attack:
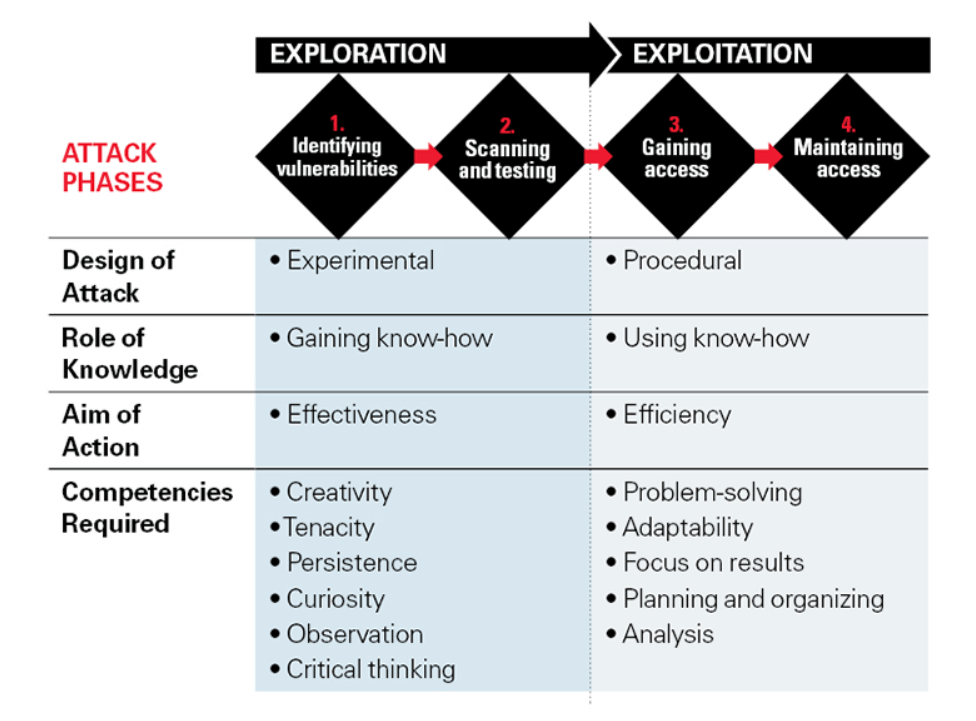
Source: MIT Sloan Management Review
Putting yourself in the shoes of cybercriminals gives you more insights of their behaviour and the way they think. They tend to be intelligent and creative individuals who enjoy taking risks, have a keen interest in computer science and are often labeled as geeks. Good social and communications skills are also required, as they might use them to easily manipulate victims or to better perform various critical actions. Sometimes they operate alone, sometimes they are organized in a group.
Cybercriminals now change tactics during attacks
As we live in an interconnected world, cyber attacks seem to become a cliche in today’s society. Without any doubts, we are more and more addicted to our smart devices and apps/software programs that should make our lives easier. While they are designed to help us better communicate and interact, they are vulnerable to online threats.
The vulnerability issue of our devices is linked with the fact that software isn’t 100% secure or perfect. It might have small flaws and fail at some point. Despite the engineers’ efforts of covering all the technical aspects and trying to make software better, computers become easy targets for the bad guys. What matters is to build quality software.
“Having a world with less software is not an option. The software is actually doing stuff that is helping us. So this should not be an excuse for deploying vulnerable software, but an incentive to make software better.” said Walter Belgers in an interview for DefCamp.
As expected, in many cases, cyber criminals take advantage of the vulnerable software, exploit flaws and start spreading malware. But they aim to do this in ways that are difficult to anticipate and, consequently, challenging to stop.
Cyber attacks have been happening for years, as malicious hackers focus on stealing money, financial data, intellectual property or simply disrupting the a company’s operations. What has changed is the modus operandi of cyber criminals. They’ve become more skilled and use new workarounds to help them avoid the usual security tactics employed by organizations worldwide. They seem to know which tactics (will) work.
The following examples are proof of the cyber criminals’ level of ingenuity.
1. Leveraging vulnerabilities that affect widely used types of software
During the massive WannaCry ransomware, cyber criminals used theEternalBlue method for quickly spreading malware and infecting a large number of computers. The reason why this particular malicious campaign became so extensive is that it exploited a vulnerability in Windows system that allowed it to move laterally within networks and infect other computers.
It’s the same type of ransomware that hasn’t changed, but cybercriminals decided to use a different tactic: exploiting an unpatched vulnerability found in a piece of software used on a global scale. This ransomware outbreak was different because of its self-replicating abilities that enabled it to spread fast and affect many companies and public institutions worldwide.
2. Changing the type of malware delivered during the same cyber attack
Petya (Petya.A, Petya.D, or PetrWrap) was another ransomware outbreak similar to WannaCry, that spread fast, but changed the type of malware from ransomware to wiper. Unlike WannaCry, it used multiple attack vectors and dropped a malware cocktail meant to encrypt and then take in and exfiltrate as much confidential data as possible. The purpose of a wiper is to destroy and damage, while ransomware is mainly focused on making money.
Using a different type of malware during cyber attacks is another surprise factor from cyber criminals. Malware cocktails proved to have a high rate of success with the Cerber ransomware campaign where they injected malicious scripts to drive infection rates.
In another malicious campaigns, attackers used GootKit and Godzilla info stealers to collect and steal victims’ financial information. These types of banking Trojans are part of a more complex malware cocktail, that can include rootkits, worms or other malware that enslave a computer to a botnet. Cyber criminals used these info stealers to compromise users of various online banking solutions.
This type of malware with a low detection rate was also used during the (non)Petya ransomware outbreak. Attackers decided to change the type of malware from ransomware to wiper, and they also dropped a malware cocktail to encrypt users’ files.
3. Changing ransomware extensions to delay strain detection
Not only are spam campaigns more frequent, but they’re also larger in scale and use new infection vectors. Locky ransomware made its appearance again and the most recent campaign used a new extension called .lukitus to encrypt files.
Locky stands out from the pack, because of its frequent attacks, but other ransomware strains have applied the same tactic in the past years as well.
Each time a new extension pops up, victims wonder how they can retrieve their data and it usually takes a few days, depending on the strain’s complexity, to figure out what the type of malware really is.
4. Using auto-updating elements to automate new payload delivery
Attackers also turned to auto-updating links in malicious emails, which is a fairly new tactic. This approach was different because “the file exploits a Microsoft Word feature that can make files automatically update links included in them as soon as they are opened”.
The same attack can thus be used to deliver multiple types of malware, depending on the attacker’s objectives.
We recommend keeping an eye on these malicious spam emails!
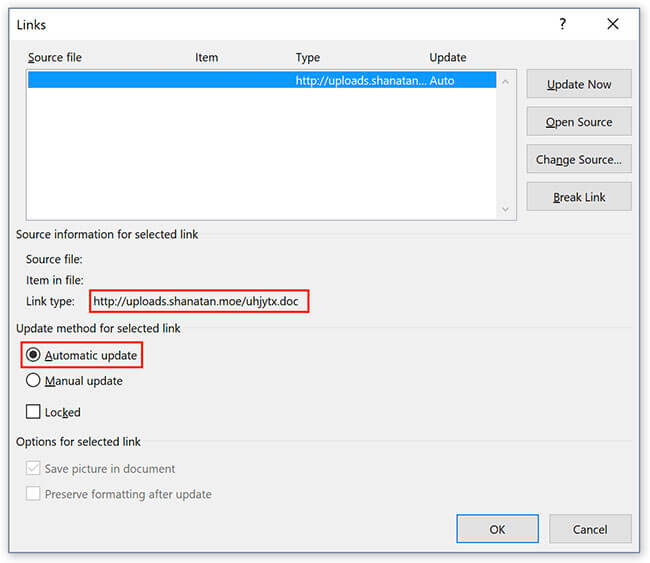
Source: Helpnet Security
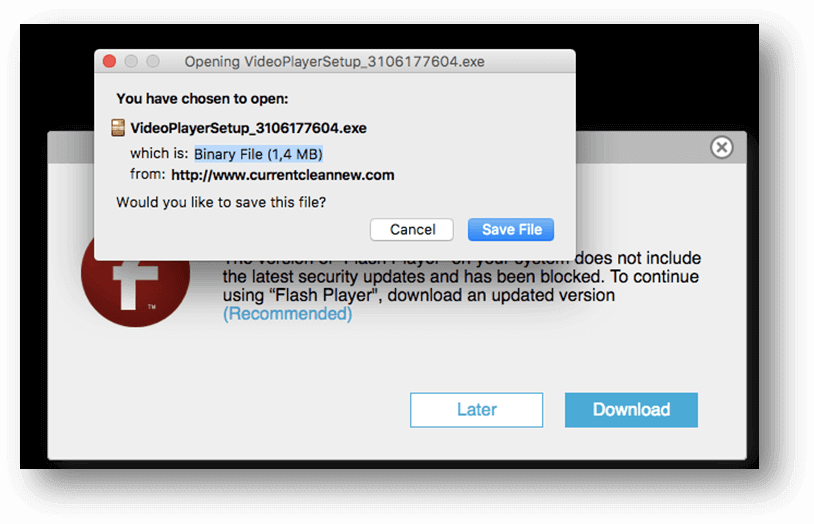
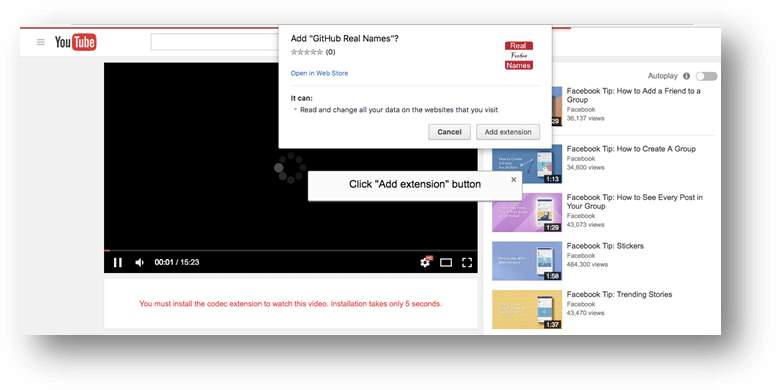
5. The matrioshka social engineering attack
For the malware threat discovered via Facebook Messenger, cyber criminals used a slightly different form of social engineering.
The unusual factor comes from the various angles used in the same attack. Online criminals employed a malicious browser extension for Chrome and Firefox and a binary package that installed adware on users’ computers.
They tried to trick people by convincing they access a legitimate link from one of their Facebook friends, so they can click on the malicious link. The message included a BIT.LY link which had a video with the person’s name.
Although this approach to luring victims with malicious links in social media messages is not new, it still works to the dismay of many home users.
6. Spoofing gets more difficult to identify
Spoofing attacks have changed and became more difficult to be spotted. During an email spoofing attack, the malicious hackers disguise and sent a fake email which looks similar to the original one. Cyber criminals aim at making victims believe they receive a genuine email from the real sender, while it is quite difficult for the untrained user to spot the suspicious elements.
During a new Locky spam campaign, cyber attackers used these tactics to spoof Dropbox, and here’s how a misleading email looks like as opposed to the legitimateone:
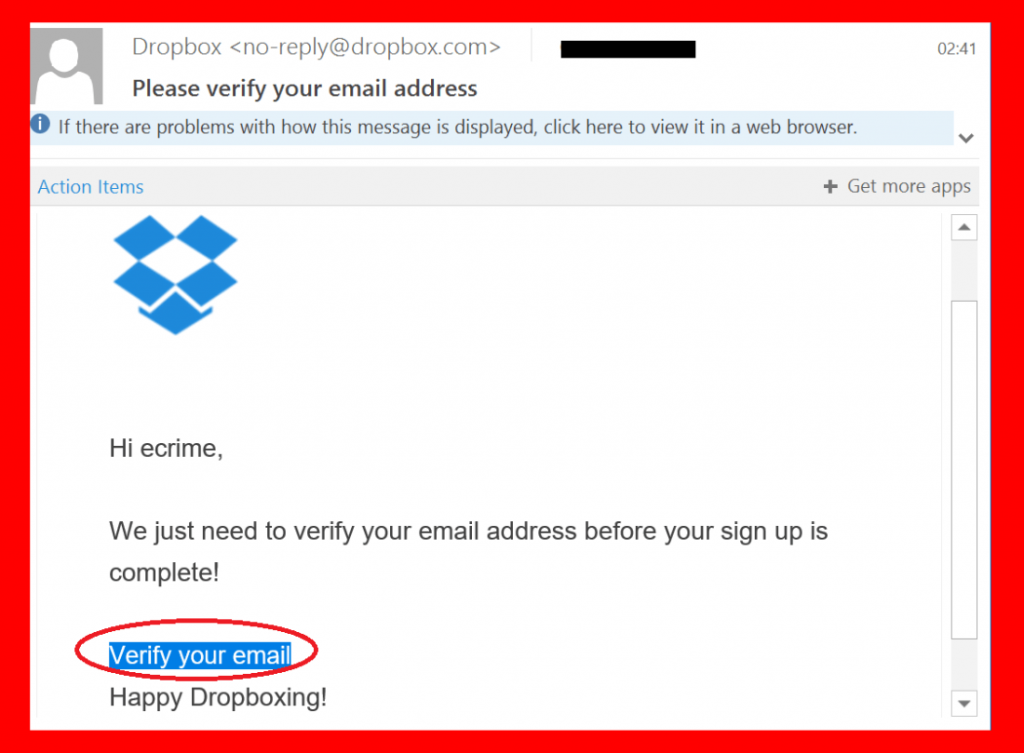
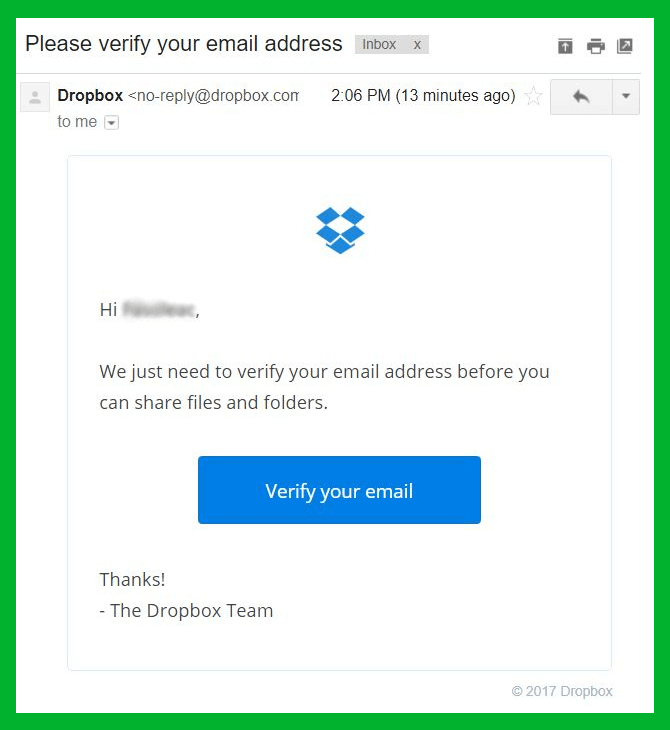
As you can see, attackers are getting better and better at impersonating legitimate entities. With so many online accounts, it’s becoming increasingly difficult to identify spoofing or phishing, which leads to more users getting compromised.
Filtering this kind of threats and educating users to identify them proactively is an uphill battle that will certainly continue in the next years.
7. Proof of concept attacks targeting widespread vulnerabilities get scarier
Last month, researchers warned about a new attack vector – known as “Blueborne” – can potentially enable cyber attackers to spread malware through thin air and potentially infect all devices that include Bluetooth wireless technology. This method of operation was different from two points of view: zero human interaction and no Internet connection. The result? More than 5.3 billion devices across Android, Windows, iOS, or Linux were found vulnerable to BlueBorne!
These are proof of concept attacks and similar to car hacking that happened a few years ago. We could anticipate that such attacks might become a reality showing us how easily attackers can take advantage of vulnerabilities in software or hardware to compromise our devices.

Source: Google Play
8. Everyone’s data is (now) leaked
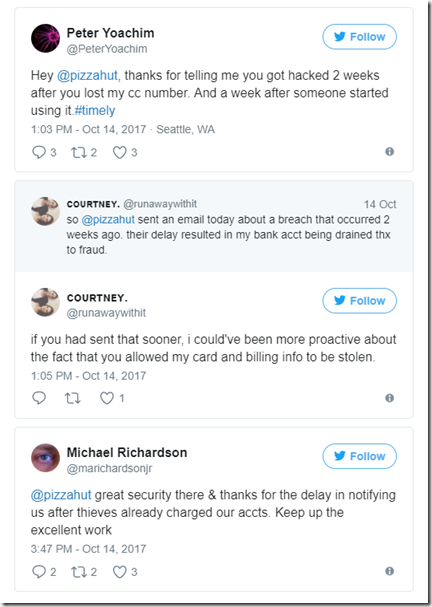
Data breaches have reached catastrophic proportions. The recent Equifax data breach has potentially impacted 145.5 million US consumers who might have had their sensitive personal information exposed. During this attack, cyber criminals took advantage of a security hole in the Apache Struts web application framework (CVE-2017-5638), the one supporting the Equifax online dispute portal web application. Failing to install the security updates can lead to massive business disruption and many other negative effects.
This only gives cyber criminals a massive amount of confidential information about potential victims that they won’t shy away from using in the next months.
9. Spambots on steroids
Emails are still an easy target for cyber criminals and the recent (yet biggest) data dump confirms it. Over 700 million of email addresses (and passwords) were exposed online with the help of a spambot operation, which sent out emails en masse to people hoping they’ll be tricked into clicking on them.
This massive spam operation showed us how vulnerable our inboxes are, and why attackers can easily plan a spam campaign to spread malicious code and infect as many users as possible.
I found out that cyber criminals use the surprise factor during cyber attacks
CLICK TO TWEET
10. Sophisticated supply-chain attacks with deeper geopolitical implications
Supply-chain attacks that involve exploiting vulnerabilities in the supply network used by a specific organization are not new. But the way cyber criminals used the backdoor tactic and managed to infiltrate malware into two versions of CCleaner, the popular PC cleaner software application, is. Not only did they potentially impact millions of devices and their users, but they also affected IT infrastructure and led to severe business disruption.
But the story doesn’t end here, as investigations are still under way, the geopolitical implications of this attack seem to ramificate.
At the recent Virus Bulletin 2017 conference, Jakub Kroustek and Jiri Bracek shared technical details on the attack and said there are more than three stages of this attack.
“This suggests it was very targeted and used only against a specific group of users,” Bracek said.
Protection guide against malware threats
In the context of the sophisticated nature of modern cybercriminals, both organizations and home users should acknowledge this threat and understand the importance of software patching. This is why we need to prioritize things by proactively changing our behaviors in a way that will enhance our security online.
Knowing that the online landscape isn’t safe anymore, securing our valuable data should be on top of everyone’s list of priorities.
Here are some useful ways to maximize your protection against these attacks:
- Keep all your software up to date, and install the latest updates, as soon as possible. Having the system up to date and protected with multiple layers of security decrease the chances of being infected with malware.
- Use unique and strong passwords with the help of a password manager program.It’s worth reminding not use the same password for all your email/social accounts, as it gets easier to be hacked and every account will be vulnerable.
- Secure your data and have at least two backups for them: an external hard drive and another one in a cloud system. Also, check to see if your backups are intact and can be restored if needed.
- When cyber criminals launch a new attack, they use various tactics and businesses with an outdated infrastructure or software are the most vulnerable to such online threats. This is why it is essential for businesses to keep their infrastructure up to date and actively defend it by closing potential holes in cyber security.
- To enhance protection, it is recommended to use an antivirus program and aproactive cyber security software solution (together).
- Users need to change their “it can’t happen to me” mindset and focus on education themselves to stay safe online. Cyber security education is essential for everyone to have minimum cyber security knowledge, so they can easily discern the good from the bad, and be safer in the online landscape.
What can we learn from cyber criminals’ malicious actions so we can have the best defense against their criminal tactics? We have to keep on investigating what makes them tick and always have a proactive behavior and react to attacks in a timely manner.
via: heimdalsecurity