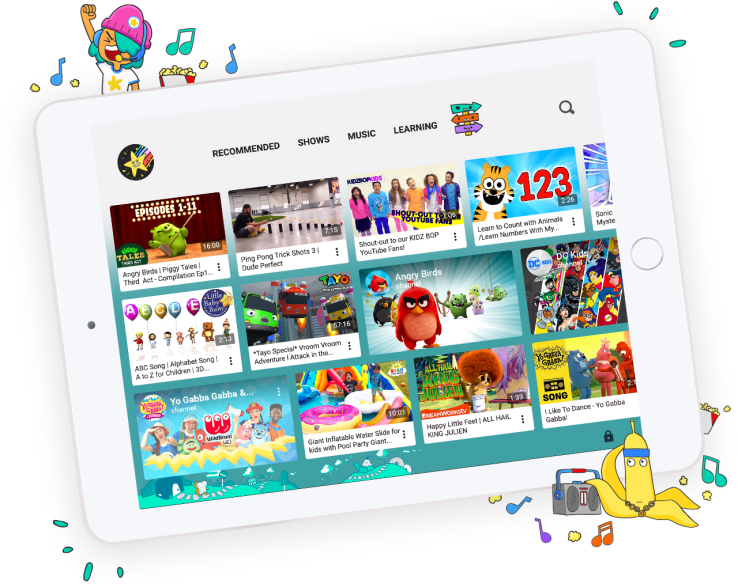
Amazon wants to be the hub for your connected home, and today the company announced two new products that will help it fill out that ambition, specifically in the area of home security. It announced a new “intelligent” camera called the Cloud Cam, and a new smart-lock service called Key.
You control both using Alexa, the voice-based assistant that powers its line of Echo speakers and screens and connected device controllers.
Pre-order pricing for the Cloud Cam starting at $119.99 and going up to $249.99 for Prime members if paired with Key as part of a larger In-Home Kit (which also includes a smart lock from Yale or Kwikset). As it did with the Echo Dot, Amazon is also selling multipacks of the Cloud Cam that bring down the unit cost. Amazon describes the Cloud Cam as a “premium product at a non-premium price.” But there are also subscription prices, which we’re detailing below.
Key, meanwhile, will launch on November 8 starting in 37 cities in the U.S. covering “millions of items,” Amazon said.
The moves underscore Amazon’s ambitions to be more than just an e-commerce hub for the home — although with Key aimed specifically at enabling deliveries, they clearly will help the company further its e-commerce business as well.
When Amazon launched the Echo Look earlier this year, people raised questions about how much Amazon was invading your privacy with a “smart” camera that could potentially record everything it sees. In light of that, it’s very interesting to see the company taking ownership of that theme with a new security cam product, which comes with even more enhanced camera features like night vision and motion detection.
It is also a sign of how the company is shaping up to be a formidable player in the area of productizing innovations in artificial intelligence.
“Cloud Cam has all the features you need to monitor your home, including a 1080p Full HD camera, night vision, two-way audio, and free storage for clips–and with the secure AWS cloud powering Cloud Cam’s advanced computer algorithms and intelligent alerts, the service is always getting smarter,” said Charlie Tritschler, Vice President, Amazon Devices, in a statement.
The Key, meanwhile, is something of a throwback to the old, human way of doing things — but with a smart lock twist. The idea with it is that the Cloud Cam is able to detect when someone has come to deliver a package and work the unlocking of the smart lock in tandem with that.
As Amazon describes it, when a delivery driver requests access to the customer’s home:
“Amazon verifies that the correct driver is at the right address, at the intended time, through an encrypted authentication process. Once this process is successfully completed, Amazon Cloud Cam starts recording and the door is then unlocked. No access codes or keys are ever provided to delivery drivers.”
“Amazon Key gives customers peace of mind knowing their orders have been safely delivered to their homes and are waiting for them when they walk through their doors,” said Peter Larsen, Vice President of Delivery Technology, Amazon, in a statement. “Now, Prime members can select in-home delivery and conveniently see their packages being delivered right from their mobile phones.”
It’s small consolation, but Amazon says that when all of the above goes wrong, “in-home delivery is backed by Amazon’s Happiness Guarantee.” I’ll be very curious to see how many people take up this offer.
The new products come swiftly on several other developments in the world of connected home security — a sign of how that market is heating up. Last week, Yale owner Assa Abloy acquired August, the smart lock startup — and we’ve heard rumors (but haven’t been able to confirm them yet) that it’s been eyeing up other connected home startups as well. Meanwhile, Alphabet-owned Nest is moving into home security on the back of acquiring Dropcam and most recently launching a secure alarm system. August had been running a trial with Walmart to allow its delivery people access to people’s homes when they are not in to securely drop off items.
While the “Cam” is clearly a physical object, there is also a “Cloud” component to the name, and that is where Amazon is hoping to make some recurring revenues. A free tier will give you access to 24 hours of clips stored in the AWS cloud (with support for three cameras). The paid tiers bring that number up to 10 with additional storage and unlimited downloads of clips, along with other features like Person Detection and Zones, which lets you indicate motions that you don’t want recorded (such as pets’ eating area or a ceiling fan). Prices for the subscriptions are as follows:
- Basic ($6.99/mo, $69/yr) offers access to the last 7 days of motion detection clips for up to 3 cameras
- Extended ($9.99/mo, $99/yr) offers access to the last 14 days of motion detection clips for up to 5 cameras
- Pro ($19.99/mo, $199/yr) offers access to the last 30 days of motion detection clips for up to 10 cameras
Also somewhat creepy but probably useful is that Cloud Cam has two-way audio to use your app to “tell your dog at home to stop barking or let your family know you’re leaving work.” The audio also works via the Echo Show and Spot.
via: techcrunch