Allowing BYOD has unfavorable implications for both the company and employees. Michael P. Kassner explores what businesses are doing to mitigate the risk.
In all my years working IT, I’ve never seen as divisive a chasm between users and IT professionals as the one brought on by Bring Your Own Device (BYOD). I’ve talked to several IT managers preparing for this article; every manager, but one, has agonized over what to do about BYOD.
One high-level IT manager told me about a meeting with her company’s C-level executives — the subject, BYOD. Her strategy was to convince the executives to move slowly in order to avoid any legal or business-related pitfalls from allowing personal devices in the workplace.
“Michael,” she said, “as I walked into the conference room, the execs already there, as if on cue, started fiddling with their personal smart phones.”
I think the discussion is over, unless do as I say, and not as I do is policy where my friend works. So how do IT departments cope? Do nothing and hope that some of the thorny legal issues concerning BYOD never happen?
Gambling that nothing will happen usually is not a good career move; we all know what happens when the blame game starts. Let me ask this, what if the BYOD problem could be solved in a way to make everyone happy?
The solution
My introduction to “the solution” occurred while reading a SANS paper by Adam Walter titled, “Endpoint Security through Application Streaming.” The first thing that caught my eye was the question Adam asked at the beginning of the paper:
Businesses are moving from a centralized core infrastructure to a decentralized one. This causes a number of issues as our businesses grow. The main issue is data flow. How do businesses maintain security when data is continually moving to the edges of our logical boundaries?
Could Adam be referring to BYOD? He continues:
A solution is needed that solves the problem while allowing the user to complete business tasks efficiently and without incident. Why not centralize again? The solution proposed in this paper works around keeping business work flows decentralized while centralizing data through application streaming.
I almost stopped reading right there. I wasn’t ready for yet another “how the cloud will solve all my problems” utterance. But my curiosity overruled:
Application streaming takes software and encapsulates it to fool the client operating system into believing it is running in the local run time. The client has an application experience similar to a local one. However, data never leaves the host server.
The term “application streaming” seemed familiar; if I remember correctly, something to do with Citrix. I also remember Citrix as being temperamental, and slow — really slow — when I first became acquainted with it many years ago.
Citrix has grown up
Once again my curiosity won, so I contacted Citrix hoping to talk to someone in the know about application streaming. My timing could not have been worse; Citrix was right in the middle of their biggest show of the year, Synergy 2013.
I was having no luck at all, then Latoya Mayo answered the phone. Latoya somehow managed to find Karen Gilles, Director of Communications, at the show. (Thank you, Latoya.) Karen then worked her own magic, hooking me up with Kevin Strohmeyer, Director of Product Marketing Desktops and Apps.
First thing I did was explain to Kevin what I thought Adam had in mind; a solution that removes BYOD from IT’s most hated list. Kevin then asked what it would take to get off the list. I suggested the following:
- Personal devices used for work cannot store company data locally.
- Personal devices and application-streaming software must meld seamlessly with the company’s network.
- Using personal devices cannot be a security risk.
I also had a few thoughts about the app-sharing client. It must be able to work with a whole lot of different devices and operating systems, and be convenient to use.
I wasn’t remotely prepared for Kevin’s answer: “No problem, Michael. We have an application called Citrix Receiver. It meets all your requirements, and works with all major operating systems. We even have a version for Kindle.”
Kevin also said he didn’t mind the term app streaming, but Citrix calls that particular technology “Session Virtualization.” I noticed in my research there are a whole host of names given to this technology. I’d like to continue using app streaming, with the understanding that neither the application nor the data resides on the user’s mobile device.
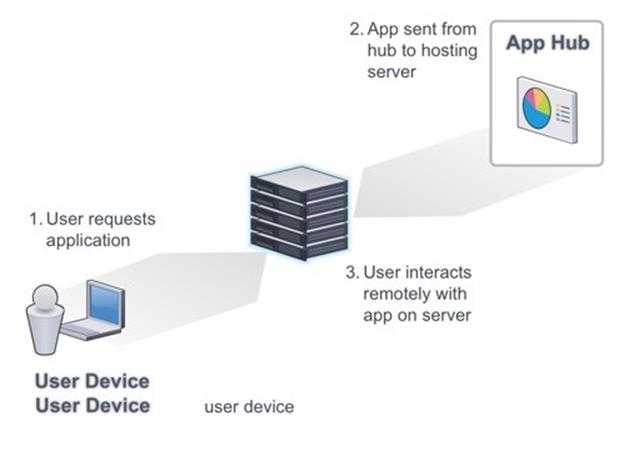
The above diagram depicts how Citrix Receiver works. The user first logs into Citrix Receiver. Once the Receiver desktop opens (image below), the user selects the application needed.
XenApp then connects the user’s device to the host server where the application has been delivered. The user interacts with the application remotely by sending input to the server. The server then responds by sending screen updates back to the user’s device.
As I see it, Citrix Receiver:
- Allows the user to get their preference in mobile device, and the IT department does not care as long as Citrix Receiver can be installed.
- Isolates sensitive personal information from privileged company information (company data is never on the mobile device). This is particularly important to the individual and company if legal issues surface.
- Reduces costs and simplifies device management. Licensing and maintenance of company applications occurs on the server, not each individual computing device.
- Eliminates concern about malicious apps or over-reaching permissions in the case of devices using Android.
I’m usually above-average cynical, but it seems application streaming has a chance of being a bona fide solution. I say that with even more confidence after looking at several companies that started using Citrix or enlarged their Citrix environment just to accommodate BYOD.
An example
Remember my mentioning every manager but one was agonizing over BYOD? Well, the unworried manager works in the health-care field, and according to him; he only stays sane because Citrix services allow him to fulfill everyone’s IT needs, along with meeting all necessary government regulations.
A case in point: when doctors asked if they could use portable devices at the office and when they were at the hospital making rounds, it was a non-issue as long as there was a Citrix Receiver app for the tablet, phone, or notebook they wanted to use.
Just to make sure
I still had a few questions for Adam, particularly if what he had in mind matched what Citrix is offering.
Kassner: Adam, app-streaming technology similar to Citrix has been around for a long time. What has changed to make you feel it will help improve the mobile-device situation?
Walter: I feel products such as Citrix have been very good at responding to customer feedback, and their products have evolved to fit the changing corporate atmosphere. We now see a product that doesn’t just virtualize, but does so seamlessly. Also, we have a variety of vendors creating products that behave differently. This is a boon to corporations, because it allows them to find the solution that fits their needs.
Kassner: I read the following in your paper:
With application streaming you are moving towards an environment that is much easier to grasp. The security problems don’t go away, but by simplifying your environment you can make mitigation something much more attainable.
Would you explain what you mean? What is easier to grasp? And, why is mitigation more attainable?
Walter: As technology has evolved, it’s also grown increasingly complex. Ten years ago, networks were relatively simple. Today we have a plethora of virtual environments, complex routing tables, and so on.
Securing such environments requires significant technological knowledge, and a lot of effort to cover all traffic flows. With application streaming, we can move important data and applications to a secure core, and serve the rest of the company from there. That means you can establish smaller boundaries for compliance purposes and focus on them rather than the whole network.
Kassner: It’s hard to disagree with the notion that applications and data can be better protected residing in a data center. But lately, it seems having to focus on a single location helps the bad guys as much, if not more than the IT department: breached credit-card processing centers come to mind. Do you see this as a problem?
Walter: As mentioned in the white paper, most attacks are easily preventable. The problem is the networks are too complex. By reducing the number of egress points, we make security more attainable. A good analogy here is that it’s easier to guard the door of your house than it is to protect the Smithsonian.
Final thoughts
I have to thank Adam Walter — until I bumped into his paper; I felt BYOD was going to be one of those “have to live with” situations. Now it becomes a risk assessment, deciding whether the cost of using app-streaming software by Citrix or other vendors to mitigate legal, regulatory, and business downfalls is cheaper than the alternative.
I’d also like to thank everyone at Citrix, particularly Kevin Strohmeyer, for helping further my understanding of app streaming.
Via: techrepublic




Leave a Reply