Just when you thought Dropbox couldn’t get any better, it has.
Many interesting cloud storage services have come and gone, but Dropbox is probably the one that’s been here the longest. And now it has upped its game with a host of new features. Let’s explore some of them from 2015 as well as some old but lesser-known ones. What we’re saying is let’s discover more stuff that you didn’t know you could do in and with Dropbox.
1. Request Files from Anyone
Sharing files saved in your Dropbox has always been easy. Collecting files in Dropbox from people? Not so much. You had to rely on third-party services for quite a long time…until Dropbox introduced its own file request feature. The best thing about it is that you can gather files even from people who don’t have a Dropbox account. No reason to force them to sign up for one, is there?
To initiate a file request, first head straight to your Dropbox account and click on File Requests in the sidebar to go to the file requests page. See that big blue plus icon there? Click on it create a file request.
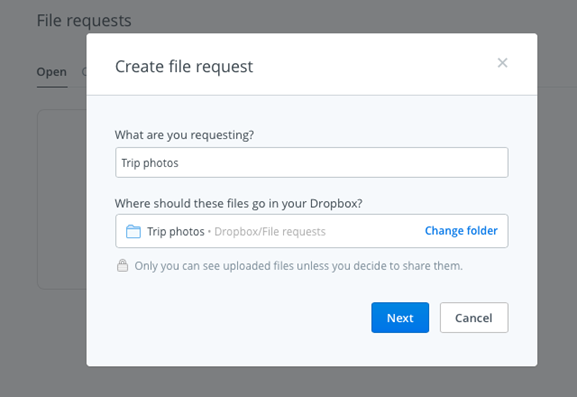
You’ll have to specify a catchall name for the files that you want to collect. Dropbox creates a new folder with this name to direct the incoming files to. You can also use an existing folder instead.
For every file request that you create, you’ll get a unique link to share with the people you want to receive files from. Ensure that you have enough space in your Dropbox account for the incoming files. Otherwise, the person sending the files will encounter an error message.
Don’t worry about the privacy settings for the received files. Only you can see them, and later share them if and when you want to.
If you’re on the receiving end of a file request, you’ll get an email with a link to upload the requested files. Click on it and Dropbox will walk you through the straightforward upload process. You’ll have to limit the file size to 2GB if you’re sending it to a Dropbox Basic user and to 10 GB if you’re sending it to a Pro or Business user.
We also recommend giving Balloon a try, if you don’t mind ditching the built-in file request feature in favor of a third-party app.
2. Preview Photoshop and Illustrator Files
Has someone shared a PSD file or an AI file with you on Dropbox? You don’t need access to the right Adobe software to preview it. You can do that right from Dropbox’s web interface, thanks to the interactive file preview feature introduced mid-2015.
Click on the file you want to preview and you’ll get an image toolbar that you can use to zone in on any portion of the preview.
You can preview files not only in PSD and AI formats, but also in PNG, JPG, EPS, SVG, and BMP. But, the previews for certain formats like PSD, AI, and SVG will be sharper and clearer than for the rest. The file preview feature also allows you to preview PDFs, slideshows, videos, and more.
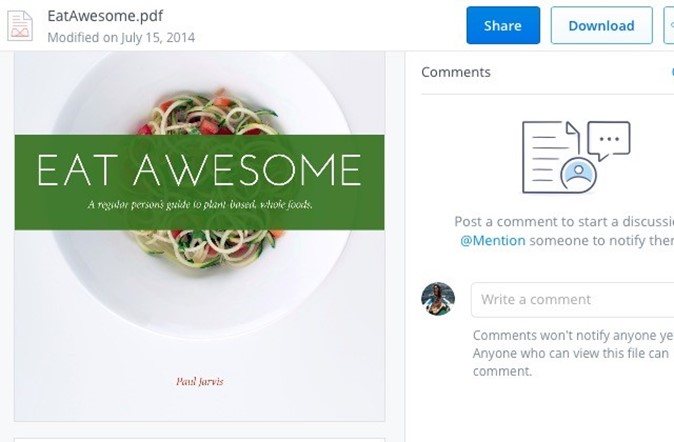
If you’re a creative professional, the preview feature ensures that you don’t have to worry about compressing high-resolution files or converting them to other, more easily viewable formats for sharing with clients. Share a Dropbox link to the design file and be done with it. Your client can preview the file (in full resolution!) and leave feedback on it from Dropbox on the web.
3. Rejoin Shared Folders
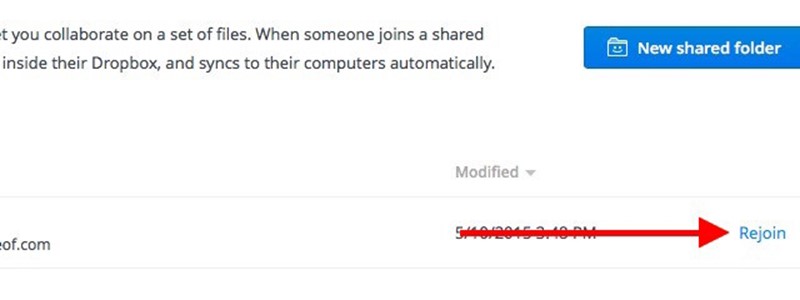
Let’s say you left a shared folder, accidentally or otherwise, by deleting it from your Dropbox, and now you want back in. Regaining access to that folder is as simple as clicking on Sharing in the sidebar and then clicking on the Rejoin link next to the folder you want fresh access to.
Remember, deleting files inside the shared folder works differently from deleting the shared folder itself. The former will make the files disappear from everybody else’s Dropbox account as well, but then again, anyone with access to the shared folder can restore them.
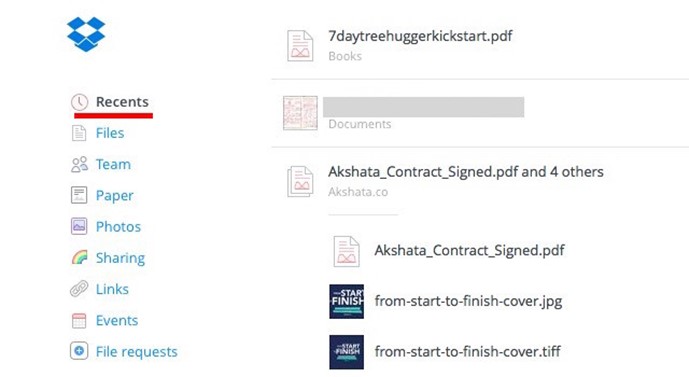
4. Find Files Faster with Dropbox Recents
You don’t have to dig through folder after folder to find a Dropbox file that you just edited. You’ll find a link to it under Recents in the sidebar. This section keeps an updated list of files that you have opened or modified recently. Share, download, comment, delete, or even view previous versions of the file straight from this list.
5. Work as a Team
Many Dropbox users — solopreneurs, for example — use the Basic and Pro versions of Dropbox for business. If you’re one of those users, congratulations. You can now collaborate better on projects using the new Team feature.
After you create a team, you’ll be able to add members to it, share files and folders with them, and create sub-folders for better organization. As the team administrator you get granular control over file and folder permissions. Also, you’re sure to appreciate the ability to link your work and personal Dropbox accounts and switch between them easily without having to log out of either.
Your work projects are not the only ones that can benefit from this collaboration feature. Personal projects also can. Have a family vacation coming up? Or a wedding? Or a friend’s birthday? Create a Dropbox team and get started on the planning!
6. Discuss Files You’re Viewing
You have probably noticed that Dropbox files on the web now come with a commenting mechanism. If you haven’t, shift your attention to the right sidebar when you have a file or file preview open, and there it is.
As is standard procedure on the web these days, you can @mention someone to get their attention, and in this case, to get their inputs on the file. They’ll receive an email notification about it and can leave a comment on the file even if they aren’t a Dropbox user.
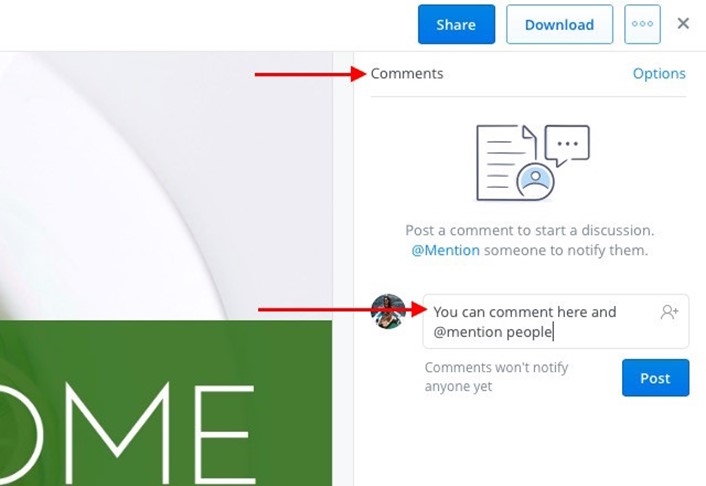
The added advantage is that if it’s a Microsoft Office file that you’re discussing, you can edit it right there based on the feedback, thanks to the Dropbox-Office Online integration. Your edits will automatically get saved back to Dropbox.
7. Sync Files Faster
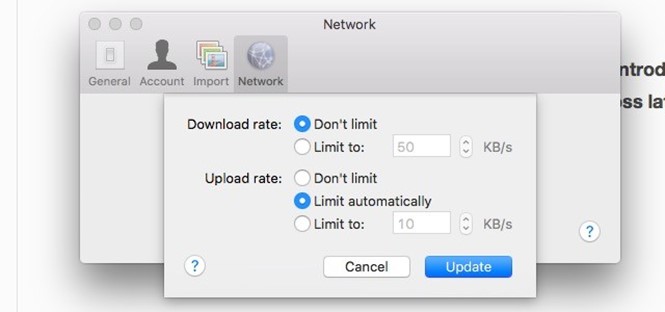
By default, Dropbox limits the bandwidth allocated to the files being uploaded to your account. If you want to take advantage of your network’s higher capacity, you can remove this limit altogether or set a custom one from Dropbox’s settings.
To remove bandwidth limits for file uploads on a Mac, first open Preferences from Dropbox’s menu bar icon.
Next, switch to the Network tab and click on the Change Settings button next to Bandwidth: Now select the radio button next to Don’t limit, or if you want to specify a limit, select the radio button next to Limit to and type in an upload speed. You can also limit the download rate from the same section. Hit the Update button once you have made the changes.
To access the bandwidth settings on Windows 7 and above, click on the Dropbox icon in the system tray and go to Preferences > Bandwidth.
8. Instantly Delete Sensitive Files for Good…
Files that you delete from your Dropbox don’t disappear immediately from your computer or your Dropbox account. They get queued up for permanent deletion and stay part of the Dropbox ecosystem for at least 30 days. The deleted files also stay in the cache folder (.dropbox.cache) within Dropbox’s root folder on your computer for three days.
Note: If you have a Pro account with Extended Version History, the deleted files stay in the online deletion queue for up to one year.
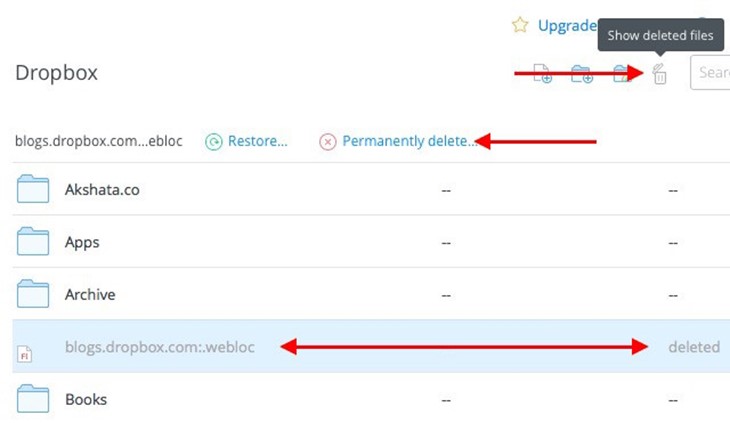
If the files you deleted contain sensitive data, you might want to clear them out from the deletion queue manually. To do so, go to the home page of your account and click on the trash icon to the left of the search box. This displays the deleted files and they appear grayed out.
Now select a binned file that you want to erase permanently and click on the Permanently delete… option in the menu bar at the top. Do this for each file that you want to erase right away. Of course, you can select multiple files using Ctrl on Windows or cmd on a Mac.
Here comes another important step: getting rid of the deleted files from Dropbox’s cache folder. You can’t see this folder unless your system is set to show hidden files. You’ll need to access it and once again delete the files from there to get rid of them for good. Of course, if you do nothing, Dropbox will still clear the cache folder in three days’ time.
Based on whether you’re using Windows, Mac, or Linux, you’ll have to look up Dropbox’s instructions to reveal the cache folder on your computer.
Warning: You can’t recover any of the files you have deleted using the steps above, but someone with access to your computer and a good recovery software might be able to.
-
Be 100% sure that you want to delete a file before you delete it.
-
Look for a more advanced security solution to remove even the most deeply hidden remnants of deleted files.
9. Add a 4-Digit PIN to the Dropbox App on Your Mobile
You know all about protecting your Dropbox account with two-factor authentication and you have set it up already, right? Have you also secured the Dropbox app on your phone or tablet with a PIN or passcode? The passcode feature is not new, but it’s one that many people overlook.
Set a passcode for the Dropbox app now via Dropbox settings > Advanced Features > Configure Passcode on your Android device or via Dropboxsettings > Passcode Lock on your iPhone. For iPads and Windows tablets, here are the instructions to set a passcode.
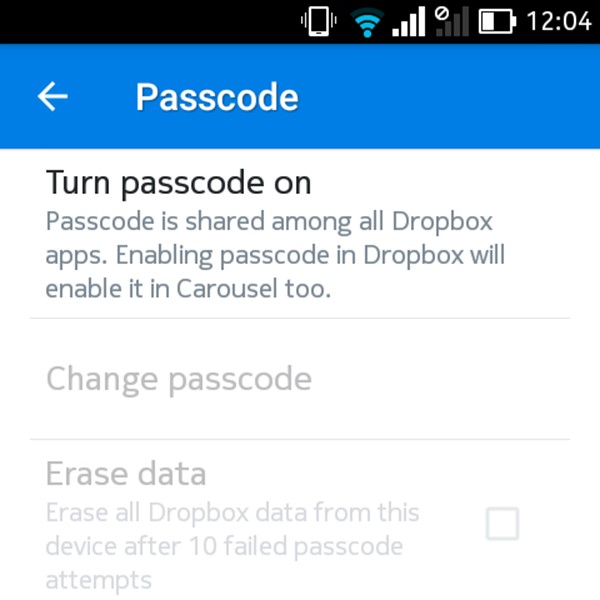
Are you a Pro user? Then in addition to setting a passcode, you can enable the setting to remotely erase all Dropbox data on that device after 10 failed attempts at entering the correct PIN. This can prove helpful if your phone ever falls into the wrong hands. There’s a catch though. You can proceed with the remote data wipe only if the device is online.
Also, if you’re a Basic user, you have to content yourself with unlinking the lost device by clicking on the “x” icon next to its name under Dropbox Settings >Security > Devices.
10. Carry Your Bookmarks Everywhere
Dropbox being such a great way to sync anything, we have all come up with various makeshift ways to sync bookmarks to the cloud. But we don’t need them anymore, because Dropbox has now added a feature to do just that.
You can now drag and drop links to Dropbox on the web or on your computer. They get backed up just like your files do, so you can open them from any location.
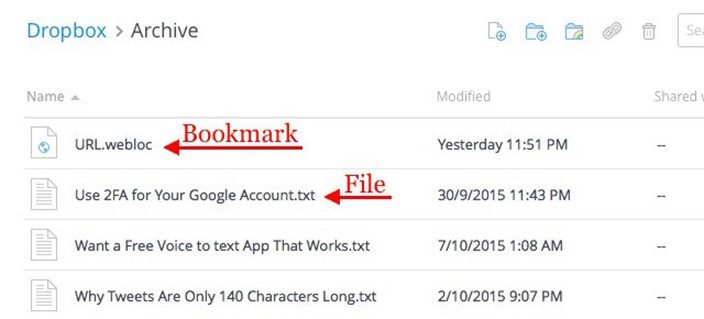
Unfortunately, clicking on a bookmark from Dropbox’s web interface loads a preview page for the bookmark instead of the link suggested by the bookmark. That’s why we recommend using the bookmark’s context menu to open the link in a new tab.
You’ll really appreciate the convenience of this bookmarking feature when you’re collaborating with someone on a project and have a bunch of shared links to keep track of.
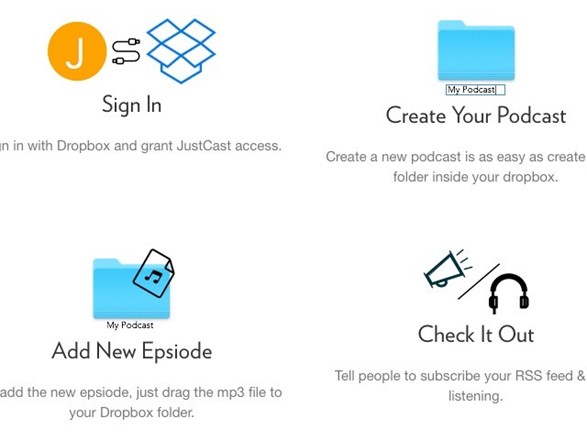
11. Host a Podcast from Dropbox with JustCast
We recently shared an exhaustive guide on how to start a successful podcast. If you’re gearing up to start a podcast yourself and are on the lookout for a decent, easy-to-manage podcast host, your search ends here — with JustCast, which is ridiculously simple to use.
Once you connect JustCast to your Dropbox, a folder named JustCast will appear in /Dropbox/Apps. Any mp3 file you add to Dropbox/Apps/JustCast/podcast_name will automatically go in your podcast’s RSS feed. All you have to do is tell people to subscribe to the feed. Use the in-built metrics feature to track the subscriber and download count.
To publish the podcast on iTunes, visit this link for podcast submission and paste the link to your RSS feed there to proceed.
Now let’s talk money. You don’t have to shell out any if you’re content having just three of the most recent episodes showing up in the feed. For unlimited feed items, you have the Pro plan at $5/month.
Here’s something you should make a note of. Dropbox has some restrictions in place on file hosting and sharing. So once your podcast gathers momentum and your audience grows, you’ll need to consider upgrading your Dropbox account to keep up with the increasing number of file downloads.
Even if starting a podcast is not in your plans, you can put JustCast to good use by turning it into a personal podcast playlist. Put any MP3 audio files you want to listen to into Dropbox as described above and use the RSS feed in your podcast client — just as you would with any other podcast.
Be mindful of copyright restrictions for any files you’re uploading to Dropbox.
12. Theme Your Dropbox with Orangedox
If you use Dropbox for work, you might want to tweak its interface to align with your brand. And that’s where Orangedox steps in. It gives you tools to add special touches to the Dropbox portal, such as you own logo and color scheme.
Orangedox also allows you to track the documents you have shared and get download stats for them. Note that only this feature is available in the Free Forever plan.
We must admit that Orangedox has not quite picked up steam despite being launched more than a year ago i.e. in 2014. But considering that there seem to be zero apps that allow you to theme Dropbox, Orangedox is still worth a shot.
13. Create Photo Galleries Using Dropbox Photos with Photoshoot
Okay. We admit that we’re cheating a bit here. You already know of apps that turn your Dropbox photos into galleries. But we had to include Photoshoot in this list because it makes the process so easy.
You drag and drop photos into Dropbox and Photoshoot takes care of creating the gallery, complete with items like thumbnails, titles, dates, and a lightbox display. You can leave the gallery visible to the public or hide it behind a password.
Via: makeuseof