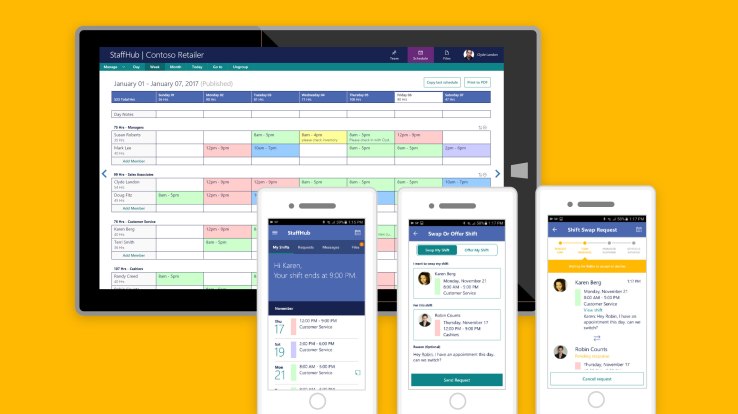
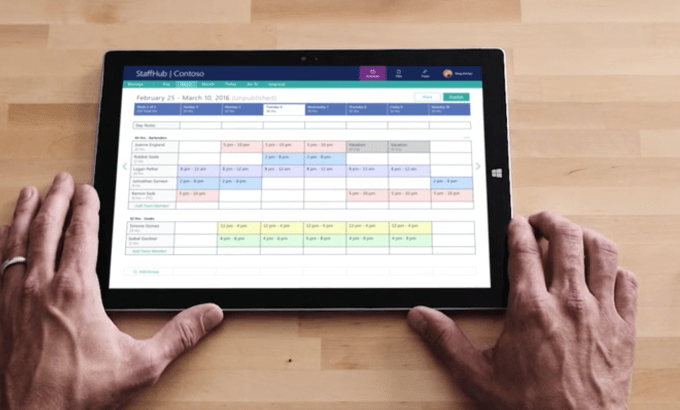
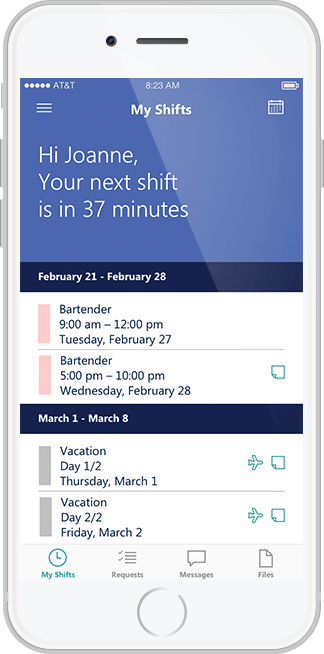
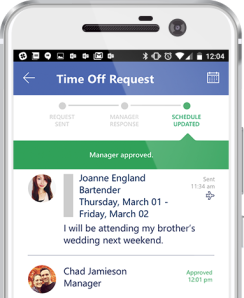
It’s no secret that Microsoft wants customers to update to Windows 10, the latest version of the company’s operating system. With extended support for the older Windows 7 OS set to expire in 2020, Redmond has been pushing companies to start migrating to the latest OS for a while now.
But Microsoft gave some added urgency to the situation in a blog post from its German subsidiary, saying that even with the security upgrades offered by extended support, Windows 7 can no longer be considered adequately protected against the current environment of malware and other hacking tools.
Doesn’t Meet the Requirements of Modern Tech
“Today, Windows 7 can no longer keep up with the increased security requirements,” Milad Aslaner, senior product marketing manager for Windows Commercial and Cyber Security, said in the blog on the German site. Aslaner said that enterprises that have been holding off upgrading to the new operating system will incur higher operating costs in the form of higher maintenance fees, time lost due to malware attacks and increased need for technical support.
In addition, Aslaner said that many hardware manufacturers are no longer producing drivers for the seven-year-old system, making it impossible for the OS to recognize some newer peripherals. “Today, it does not meet the requirements of modern technology, nor the high security requirements of IT departments,” according to Markus Nitschke, head of Windows at Microsoft Deutschland.
New Security Features
Basic support for Windows 7 was discontinued in January 2015. Since that time, users have been able to receive security upgrades, but no new upgrades to its functionality. Furthermore, Aslaner said that the older system is based on security architecture that is now outdated.
Microsoft said that enterprise clients in particular should begin migrating sensitive data over to the new platform as quickly as possible, or face “enormous dangers” from new cyberattacks the older system was never designed to protect against.
Windows 10, meanwhile, features a whole suite of security features that make the system safer than older systems, according to Microsoft. For example, two new zero-day exploits that the company was forced to patch in November for its older operating systems were ineffective against the latest version of Windows 10.
The new OS comes with some new built-in protections, such as Windows Hello, a biometric security system that allows users to log in using fingerprint, facial or iris recognition, obviating the need to use insecure passwords that can be easily stolen from a database, according to Microsoft.
Windows 10 also comes with Windows Defender Advanced Threat Protection, a cloud-based threat analytics package that uses machine learning, behavior and pattern recognition to detect when a breach has occurred or recognize incoming attacks as they happen.
Whether companies decide to heed Microsoft’s warnings is unclear. Many companies stuck with Windows XP long after Microsoft had discontinued its primary support, and many may also be slow to migrate to Windows 10.