This attack requires no clicks and takes advantage of your outdated apps.
Cybersecurity experts obsessively repeat two types of advice:
- Use stronger passwords.
- Update your software.
Today’s security alert is all about the importance of applying software updates as soon as possible after they’re released.
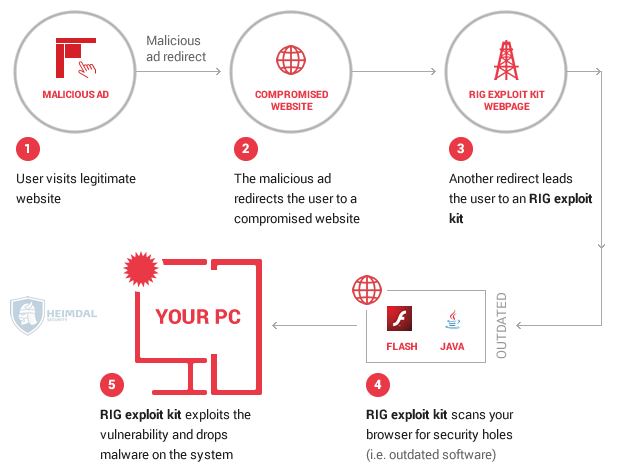
At the moment, cybercriminals are using a swarm of malicious domains to launch drive-by attacks against unsuspecting users.
The campaign works by injecting malicious scripts into insecure or compromised systems. Victims can get infected simply by browsing the compromised or infected websites, without clicking on anything. What exposes them to this attack are outdated versions of the following apps: Flash Player, Silverlight, Internet Explorer or Edge.
This is the short version of how it happens:
A total of 8 vulnerabilities scattered over several product versions might cause serious trouble for many users. That’s because RIG exploit kit will detect these unpatched vulnerabilities and then download Cerber ransomware by taking advantage of them.
Antivirus detection for this malicious campaign is low, as you’ll see in the details below.
Vulnerabilities exploited in the attack
The following apps – which you may also be using – can expose your system to a costly ransomware attack.
Affected software: Adobe Air, Adobe Air Sdk, Air Sdk Compiler, Adobe Flash Player
Vulnerability:CVE-2015-8651; can Execute Code, Overflow
CVSS Score: 9.1
This vulnerability includes 11 security holes in 4 products (see CVE link for details).
Patched on December 28, 2015.
Affected software: Adobe Flash Player, 99 vulnerable versions, see CVE link below for details.
Vulnerability:CVE-2015-5122; can cause Denial of Service, Execute Code, Memory corruption
CVSS Score: 10
Patched on July 10, 2015.
Affected software: Adobe Flash Player version 21.0.0.226
Vulnerability:CVE-2016-4117; can Execute Code
CVSS Score: 10
Patched on May 12, 2016.
Affected software: Adobe Flash Player, 14 vulnerable versions, see CVE link below for details.
Vulnerability:CVE-2016-1019; can cause Denial of Service, Execute Code
CVSS Score: 10
Patched on April 5, 2016.
USEFUL TIP: If you need a quick way to check what Flash version your system is running, go to this link provided by Adobe and find out. Flash is a notorious source of vulnerabilities for its users, so reading this guide we put together may help you understand why and what you can do about it.
Affected software: Microsoft Edge
Vulnerability: CVE-2016-7200; can cause Denial of Service, Execute Code, Overflow, Memory corruption
CVSS Score: 7.6
Patched on November 8, 2016.
Affected software: Microsoft Edge
Vulnerability:CVE-2016-7201; can cause can cause Denial of Service, Execute Code, Overflow, Memory corruption
CVSS Score: 7.6
Patched on November 8, 2016.
Affected software: Internet Explorer versions 9, 10, 11
Vulnerability: CVE-2016-3298; can obtain information
CVSS Score: 3.6
Patched on October 11, 2016.
Affected software: Silverlight version 5.0
Vulnerability: CVE-2016-0034; can cause Denial of Service, Execute Code
CVSS Score: 9.3
Patched in January 12, 2016.
To give you an example about what could happen if an attacker successfully exploits this vulnerability, here are some details shared by Microsoft last year:
In a web-browsing scenario, an attacker who successfully exploited this vulnerability could obtain the same permissions as the currently logged-on user. If a user is logged on with administrative user rights, an attacker could take complete control of the affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
This last bit is another good reminder to use a standard account on a daily basis, instead of using an administrator account.
The current drive-by campaign uses the following domains (sanitized for your protection):
mind.pci [.] news – Detection: 4/69 on VirusTotal
fun.rum [.] news – Detection: 5/68 on VirusTotal
open.oral [.] news – Detection: 4/69 on VirusTotal
one.pinot [.] news – Detection: 2/68 on VirusTotal
top.penile [.] news – Detection: 4/68 on VirusTotal
end.prayer [.] news – Detection: 5/68 on VirusTotal
top.rvlife [.] news – Detection: 2/68 on VirusTotal
old.prepaid [.] news – Detection: 2/68 on VirusTotal
see.pancreatic [.] news – Detection: 4/69 on VirusTotal
one.salesforce [.] news – Detection: 5/68 on VirusTotal
new.phonesystem [.] news – Detection: 2/68 on VirusTotal
All these domains are part of the so-called Pseudo-Darkleech gateway, which was also used in distributing Cerber ransomware in December 2016 and CrypMIC ransomware earlier, in September 2016.
The RIG exploit kit used in this malicious campaign is the Empire Pack version (RIG-E). This is what the Empire Pack panel looks like:
If this hasn’t persuaded you to automate your updates, maybe cyber security experts and their stories will convince you.
As you can see, cybercriminals often use vulnerabilities already patched by the software developer in their attacks, because they know that most users fail to apply updates when they’re released.
In spite of the wave of attacks, many Internet users still choose to ignore updates, but we hope that alerts such as this one will change their mind and make them more aware of the key security layer that updates represent.
via: heimdalsecurity




Leave a Reply