“Red Team” members were fired as they stepped off stage after presenting internal attack tool.
Enlarge / Meatpistol was supposed to be released at DEFCON. But Salesforce pulled the plug—and fired two security employees for presenting about it.
At Defcon in Las Vegas last month, word rapidly spread that two speakers—members of Salesforce’s internal “red team”—had been fired by a senior executive from Salesforce “as they left the stage.” Those two speakers, who presented under their Twitter handles, were Josh “FuzzyNop” Schwartz, Salesforce’s director of offensive security, and John Cramb, a senior offensive security engineer.
Schwartz and Cramb were presenting the details of their tool, called Meatpistol. It’s a “modular malware implant framework” similar in intent to the Metasploit toolkit used by many penetration testers, except that Meatpistol is not a library of common exploits, and it is not intended for penetration testing. The tool was anticipated to be released as open source at the time of the presentation, but Salesforce has held back the code.
“Meatpistol is a framework for red teams to create better implants,” and an “offensive infrastructure automation tool,” Schwartz and Cramb explained in their presentation. It is intended to automate the grunt work of deploying new malware attacks for multiple types of targets. Rather than testing for common vulnerabilities as penetration testers often do, the internal red team Schwartz led until last month had the job of constantly probing and attacking Salesforce’s systems. It even stole data like real adversaries, operating with nearly unrestricted rules of engagement internally.
Meatpistol, while still in its early stages of development, had already improved the efficiency of the Salesforce red team. “Malware implant creation used to take days,” Schwartz said during his presentation. “Now it takes seconds,” he said, cutting “weeks off our operation time.”
Schwartz had reportedly gotten prior approval to speak at Defcon from Salesforce management, and he was working toward getting approval to open-source Meatpistol (which is currently in a very rough “alpha” state but was at use internally at Salesforce). But at the last moment, Salesforce’s management team had a change of heart, and it was trying to get the talk pulled. As ZDNet’s Zach Whittaker reports, a Salesforce executive sent a text message to Schwartz and Cramb an hour before their scheduled talk, telling the pair not to announce the public release of the code.
According to one source Ars spoke with at Defcon, Schwartz turned off his phone prior to the presentation so that he couldn’t be told directly not to speak.
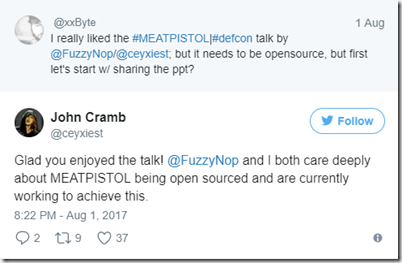
Schwartz told the audience during the presentation that he would push to get the tool published as open source because he felt that it could only get better through community contributions. Following the presentation, Cramb posted to Twitter:
There’s no indication that Salesforce is taking any further action against Schwartz and Cramb. The Electronic Frontier Foundation’s deputy executive director, Kurt Opsahl, confirmed to Ars in an e-mail that the EFF is “representing Josh Schwartz and John Cramb with respect to their talk at Defcon. However, we are not aware of any charges or complaints, whether filed or pending, nor is there any reason to believe that any would be warranted.”
A Salesforce spokesperson contacted by Ars would not comment, stating, “We don’t comment on matters involving individual employees.”
Ars has been unable to contact Schwartz and Cramb directly. We’ll update this story as more details become available.
via: arstechnica




Leave a Reply