Microsoft Office exploits are cunningly-crafted, deliberately malformed chunks of data, inserted into Office files, that crash the application in a way that gives cybercriminals control, so that they can install malware without you noticing.
With a reliable exploit in hand, they don’t need to persuade you to click a web link, or to download and install a program, or to enable Office macros (which are off by default, with very good reason) and re-open the document at a lower security level.
Just opening the document to read it, or in some cases merely looking at it in a preview window, may be enough to infect your computer with malware.
TRACKING THE THREAT
In order to keep track of the burgeoning appetite of the criminals for Office-based attacks, we’ve been monitoring the usage patterns of the most popular Microsoft Office exploits.
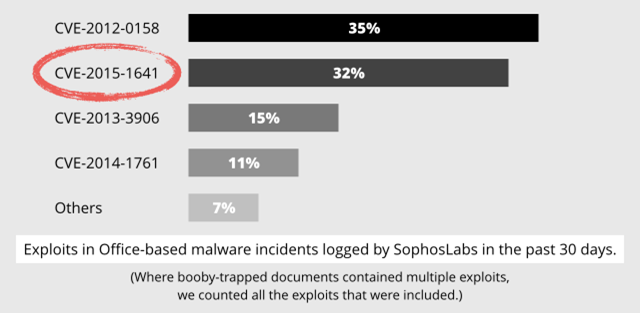
For many years, one exploit has been at the top of our charts: CVE-2012-0158.
As explained above, document-based malware is an alternative infection vector for malware authors, and in recent months, some cybercrime groups have started using documents as their primary malware-spreading mechanism.
In a typical infection scenario, booby-trapped documents are attached to phishing email messages and sent out:
-
To large numbers of random recipients in the case of cybercriminals who are in it for the money.
-
To a small number of selected recipients in the case of Advanced Persistent Threat (APT) groups, who are typically focused on specific organizations.
Older exploits still work against a surprising percentage of users, thanks to poor patching habits, but new exploits have more value, because even fewer users are likely to be patched against them.
As the name tells us, CVE-2012-0158 has been around for more than three years now, so it is no wonder that the malware authors were looking for a replacement.
Over the years there were a few candidates, such as CVE-2013-3906 and CVE-2014-1761, but none of those threatened the dominant position of the old exploit, presumably because they simply didn’t work as effectively in the real world.
NEW KID ON THE BLOCK
Nothing endangered the reign of CVE-2012-0158 until August 2015, when a new Office exploit known as CVE-2015-1641 started to become popular with the crooks.
This exploit showed up only in small APT incidents before that time, but it was August when it found its way into the broader cybercrime scene.
The new exploit quickly became popular, and as we reach the end of 2015, it is poised to move into first place:
As we have written before, malware authors usually don’t concern themselves with the details of how Office exploits work, and they don’t need the technical skills to produce booby-trapped documents of their own.
They can simply do a deal, via the cyberunderground, with an exploit provider – “crimeware as a service” (CaaS), as it is known – who will arrange for the delivery of their malware to a specified number of victims, using booby-trapped documents as the infection vector.
IN CONCLUSION
Cybercrime gangs find Office documents a convenient way to spread their malware.
They have been using this method steadily over the past two years, and there is every sign that they will continue to do so.
Their approach is evolving over the time: they use various underground tools to generate their booby-trapped documents, and thanks to the development of these tools they automatically get to use newer Office exploits.
The good news is that they aren’t using zero-days, which are security holes for which an exploit appeared before a patch was available. (They’re called “zero-days” because there were zero days during which you could have been proactively patched).
Even the freshest exploit in their arsenal was fixed six months ago.
In other words: patch early, patch often!
Via: sophos




Leave a Reply