Researchers have discovered a botnet which comprises of tens of thousands of hijacked home routers.
A massive DDoS botnet made up of a slave network of hijacked home and office routers has been revealed.
According to a report released by cybersecurity firm Incapsula on Wednesday, lax security practices concerning small office and home office (SOHO) routers has resulted in tens of thousands of routers becoming hijacked — ending up as slave systems in the botnet network.
Distributed denial-of-service (DDoS) attacks are a common way to disrupt networks and online services. The networks are often made up of compromised PCs, routers and other devices. Attackers control the botnet through a command and control center (C&C) in order to flood specific domains with traffic.
This, in turn, can overwhelm a service, causing websites to effectively turn down legitimate traffic under the onslaught. DDoS attacks are also occasionally used as a distraction while a threat actor uses other methods to break into corporate networks.
Several dozen Imperva Incapsula customers were recently targeted by a DDoS botnet comprised of hijacked routers through a series of application layer HTTP flood attacks. The attacks were first detected in December last year, and the company has been mitigating the flood ever since. However, in the last 30 days, attacks have risen to a new height with double the number of attacking IPs than previous records.
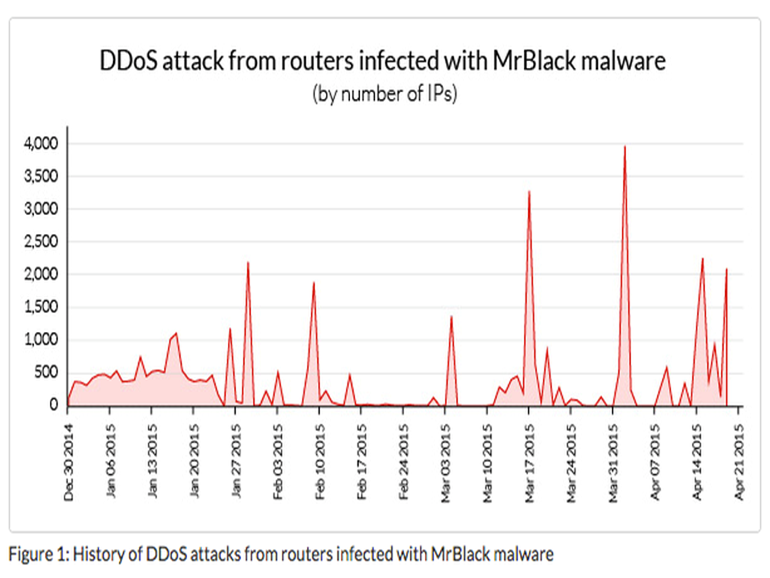
After investigation, Incapsula discovered the attacks on domains the company monitors were only a small part of the bigger picture — a far larger DDoS botnet assaulting “hundreds” of other domains outside of the Incapsula network. In addition, attack vectors beyond application layer HTTP flood attacks are being used and include network layer barrages.
However, what makes this botnet special is its reliance on SOHO routers, which are predominantly ARM-based Ubiquiti devices.
ISPs, vendors and users themselves — who do not lay down basic security foundations such as changing default passwords and keeping networks locked — have likely caused the slavery of “hundreds of thousands […] more likely millions” of routers now powering DDoS botnets which can cause havoc for both businesses and consumers, the firm says.
While it is not known exactly how many SOHO routers are part of the newly-discovered botnet, Incapsula researchers found that all of the units were remotely accessible via HTTP and SSH on their default ports — and on top of this, “nearly all are configured with vendor-provided default login credentials.”
Incapsula believes that new devices are added to the network through the execution of shell scripts which seek out devices with open SSH ports which can be accessed using default credentials.
As a result of these poor security practices, threat actors which have compromised these routers could potentially eavesdrop on communication, perform man-in-the-middle (MITM) attacks, hijack cookies and gain access to devices connected to the local network.
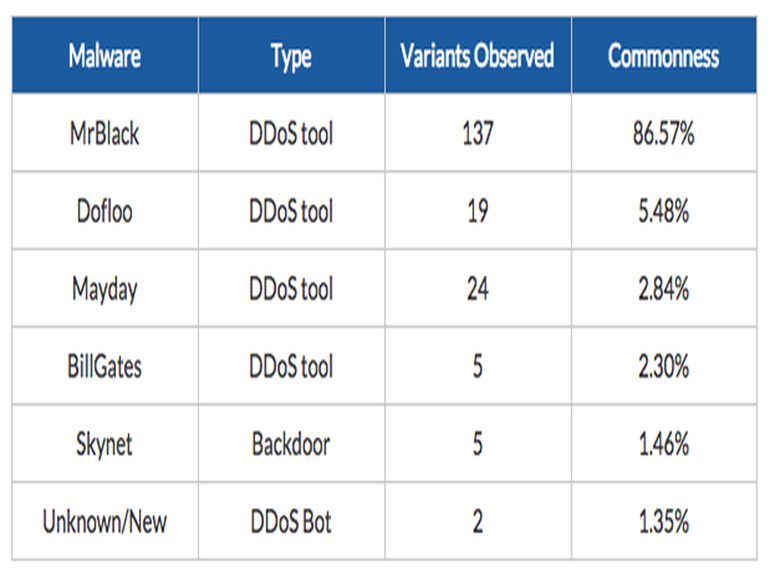
After analyzing 13,000 malware files, the researchers determined that the victim routers were all compromised through variants of the MrBlack malware — Trojan.Linux.Spike.A — as well as Dofloo and Mayday, all previously used for DDoS attacks. However, the researchers believe several groups or individuals are pulling the strings, and new malware types are constantly being added.
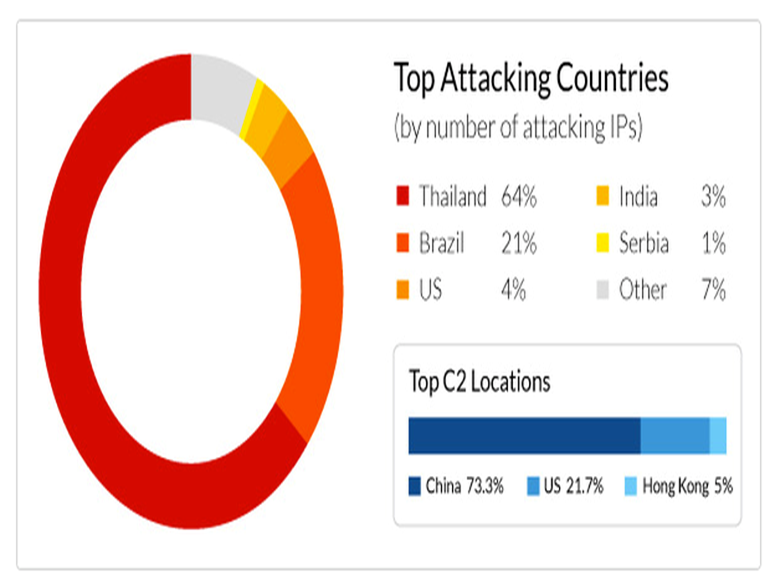
Between December 30, 2014 and April 19 this year, Incapsula recorded attack traffic from 40,269 IPs belonging to 1600 ISPs worldwide, as well as at least 60 C&C centers. The majority of compromised routers, 85 percent, are in Thailand and Brazil. However, the majority of C&C centers are within China and the United States, at rates of 73 percent and 21 percent respectively.
Attack traffic has been traced from 109 countries.
The new botnet is similar to hacking group Lizard Squad’s DDoS for hire scheme. The Lizard Stresser is a DDoS botnet, reportedly also making use of slave routers, which can be hired for as little as a few dollars. However, while Incapsula’s botnet uses Spike to compromise devices, Lizard squad relies on Linux.BackDoor.
Prior to publishing their findings, the cybersecurity firm contacted the router vendors and ISPs “found to be most open to abuse.” Router owners are urged to disable all remote access to their router management platforms and change their login credentials.
Via: zdnet




Leave a Reply