Researchers have developed a utility that allows victims affected by CryptXXX ransomware to decrypt their files for free.
CryptXXX is one the newest crypto-ransomware samples to be observed in the wild. It is being delivered to users as a Dynamic-Link Library (DLL) dropped by Bedep, a piece of malware which has the ability to download additional harmful software onto a victim’s computer.
Currently, malicious websites hosting the Angler exploit kit are helping to distribute Bedep to unsuspecting users.
Once it fully installs itself on a victim’s machine, CryptXXX appends the .CRYPT extension to each infected file, displays a ransom message, and asks for US $500 in payment. That demand will double in value if the fee has not been paid within a few days.
CryptXXX can also steal Bitcoins and other information, capabilities which security firm Proofpoint feels might link the ransomware directly to the authors of Angler and Bedep.
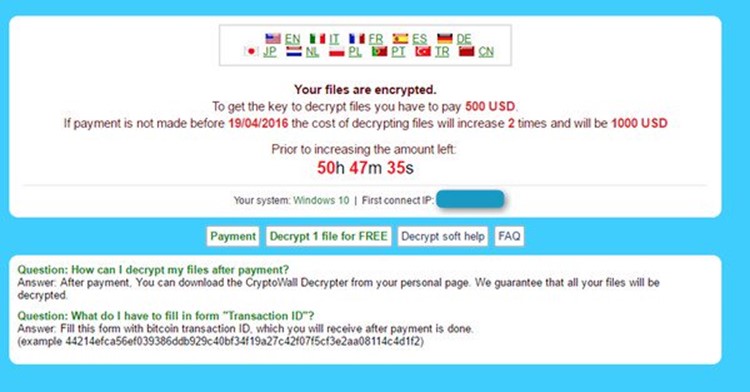
Victims of crytpo-ransomware have little choice but to pay the ransom in most cases.
Fortunately, researchers at Kaspersky Lab have given users affected by CryptXXX another option.
“The RannohDecryptor utility was initially created to decrypt files, which suffered from Rannoh ransomware,” Kaspersky says in a post. “In time it acquired additional and useful features. Now it can be used to cure your files from CryptXXX activity.”
Victims of the ransomware should download Kaspersky’s utility (available here), open “Settings,” and choose which drive types they want to have scanned. They should then click “Start scan” and choose where the encrypted .CRYPT file lies.
After asking for where the original file is located, the decryption tool will look for all other files with the .CRYPT extension and will attempt to decrypt those, as well.
Ransomware infections pose a significant threat to users’ and organizations’ data. Fortunately, people can take certain steps to protect themselves against variants like CryptXXX.
Via: tripwire




Leave a Reply