Have you heard of Pokémon GO?
If you haven’t, you probably will soon: it’s an online game for mobile phones, and it’s taken the world by storm.
It works something like this.
You install the app, give it access to your location and your camera (amongst numerous other permissions), and set about finding Pokémon creatures in the game.
Unlike most “virtual world” games, however, the map used in Pokémon GO is the world around you, and the creatures you’re supposed to find are added to the map.
To collect them, you actually have to go to where the virtual creatures are supposed to be.
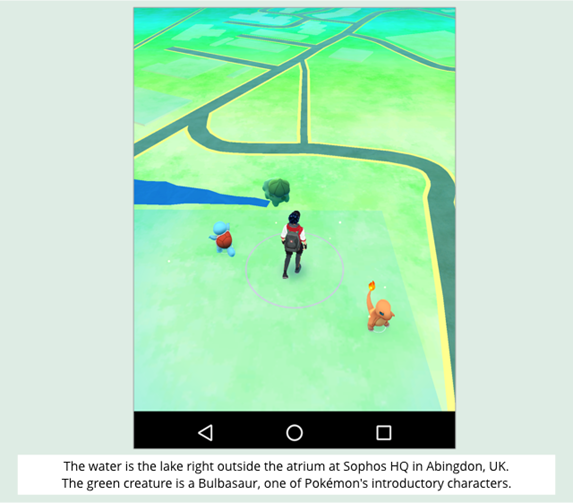
When the game figures your geolocation data is close enough to the target location, you turn on your phone’s camera, and, hey, look at that!
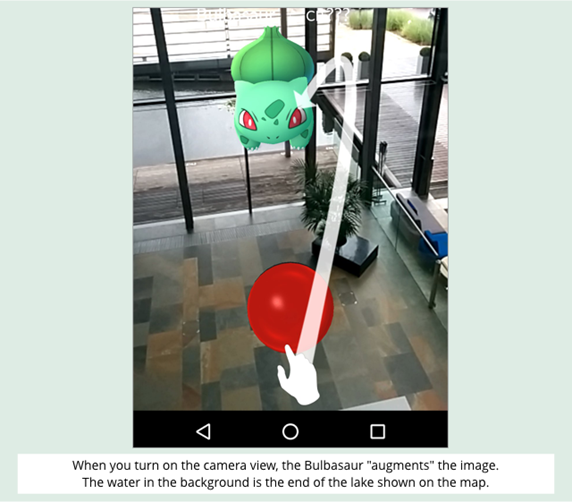
There’s the creature, grafted into the live image, in what’s called “augmented reality.”
Once you’ve caught the three starter Pokémons, you need to venture around your neighbourhood to find PokéStops.
PokéStops are supposed to be near important landmarks such as statues and monuments (our closest is at the local skateboard park), where you can get hold of the ammo, sorry, Poké Balls you need to catch more characters.
Once you’ve got the balls, you can wander afield looking for Pokémons to shoot, ahem, capture, ahhh, train.
Obviously, walking around an urban landscape while watching your mobile phone screen is both dangerous and anti-social, as the app warns you each time you start it up:
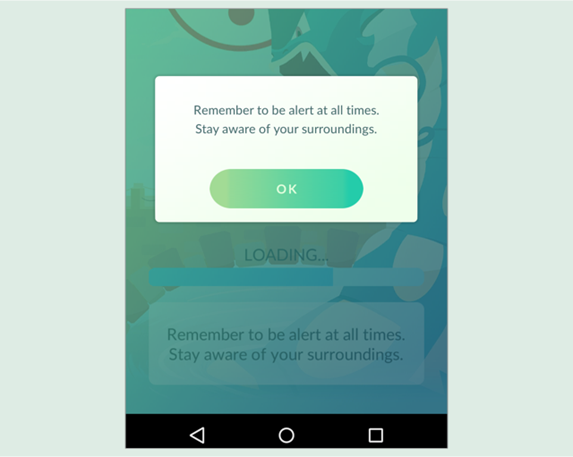
Runaway popularity
We’re not sure we understand why going to the skateboard park to stare at the world through your phone’s camera is more fun than going there to skate, or even just to stare at the world through your own eyes, but there’s no mistaking the runaway popularity of Pokémon GO.
Even the most perfunctory online search will bring up dozens of articles offering advice all the way from how to fix “GPS not found” errors to “when to evolve and when to power up.”
Apparently, the success of the app has also been a problem: overloaded servers, delays in signing up, and more.
For that reason, it’s currently only available in the Apple App Store and on Google Play in a handful of countries.
Nevertheless, as you can see in the screenshots above, we’ve managed not only to install the app on Android in the UK, but also to use it successfully, with the UK maps and game infrastructure working just fine.
Indeed, the game’s already wildly popular over here in the UK, which means…
…that most players will have headed off to alternative markets to grab the software unofficially:
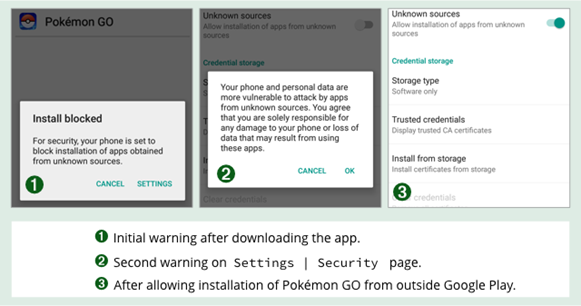
We’re not naive enough to assume that Google Play is immune to malware.
Nor do we buy into Google’s efforts in 2015 to “define away” the problem of malware in the Play Storeby renaming all malware as Potential Harmful Applications (ironically divided into categories such asspyware, call_fraud, ransomware and even generic_malware).
But Google’s warnings about untrusted apps are worth heeding anyway, because the Play Store is relatively safe, especially compared to many alternative app markets where anything goes, and anyone can upload anything.
Pokémon GO malware
In fact, the crooks have gone there already, with at least one hacked “malware remix” of the official Pokémon GO app doing the rounds.
The “remix” is deliberately poisoned with an Android spyware/RATware/zombie toolkit that hides malware code inside a fully-functional and otherwise identical-looking version of the original app.
Spyware is malware that snoops on your online activities, such as listening into phone calls, intercepting SMSes and logging all your web browsing. RATs are Remote Access Trojans, an acronym coined to reflect the sort of creep who uses them, typically for leering secretly through other people’s webcams. Zombies, also know as bots, are remote control tools that let crooks send commands to a whole raft of infected devices at the same time, for example to steal data, send messages in bulk, or DDoS other people’s servers with massive spikes in unwanted traffic.
Sophos products blocked this Pokémon GO-based malware proactively as Andr/SandRat-C, a name that is derived from SandroRAT, a remote control toolkit that was announced publicly back in 2014, and that morphed into a snoopware “product” known as DroidJack, or DJ for short.
The big question
The big question, if you’re one of the many global users who has gone off-market to get your Pokémon GO fix, is this: “Would you back yourself to spot the difference if you downloaded a dodgy version by mistake?”
DroidJack doesn’t create an app that looks and behaves similarly to a well-known app in order to act as as a cover.
It takes an existing app and simply repackages it into an app that effectively is the original, but with some added spyware-related code that runs in the background.
For example, here are the startup screens of the original and of the malware-infected version:
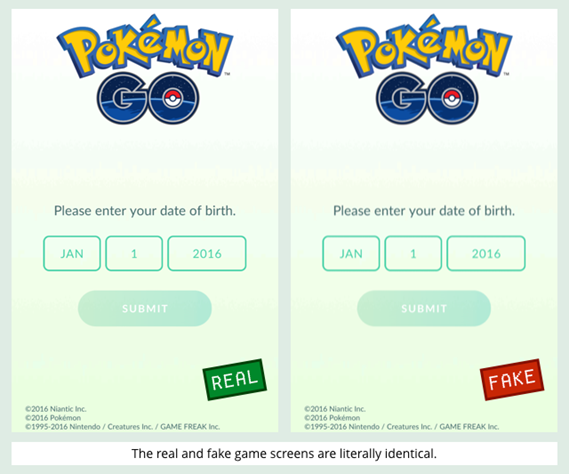
Those screenshots, and the program code that’s controlling them, don’t just look identical, they areidentical.
Spot the difference
Of course, there are tell-tale signs, if you know what to look for.
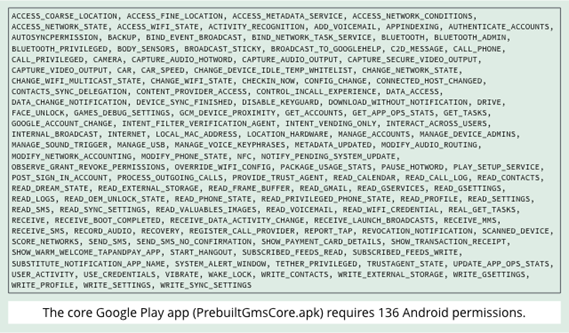
The Andr/SandRat-C remix of Pokémon GO has a whole load of additional sneaky features that run in the background, so it needs security permissions that the legitimate app doesn’t require:

But permissions aren’t always a good giveway: legitimate apps routinely ask, like Pokémon GO does, for access to your camera (which includes access to the microphone), to location data, and to external storage.
A spyware Trojan that was slightly less ambitious than Andr/SandRat-C, and stuck to a smaller set of eavesdropping “features”, could put you at almost as much risk with few or no additional permissions.
In any case, how many permissions are too many?
The Google Play app that you get with closed-source versions Android 5.1, for example, grants itself more than 100 special app permssions, from READ_VOICEMAIL and READ_GMAIL, throughCAPTURE_VIDEO_OUTPUT, to DOWNLOAD_WITHOUT_NOTIFICATION. (If those aren’t enough, it also grabs the right toOBSERVE_GRANT_REVOKE_PERMISSIONS, just in case.)
Inside the SandRat
Decompiling the Andr/SandRat-C app makes the malicious parts stand out, even if you don’t have a legitimate copy of Pokémon GO to compare it with:
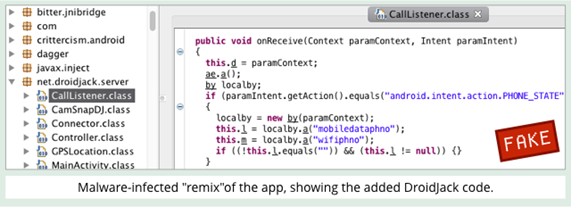
The functionality of these added DroidJack parts are, indeed, what their names suggest.
However, as with additional permissions, malware doesn’t have to be so blatantly obvious, and even a well-informed user with the Android Development Tools installed might struggle to spot the malicious needle in the haystack of a booby-trapped app.
For example, more subtle spyware could add fewer functions, could give them more legitimate-looking names, and could patch its extra code into existing parts of the app so it wasn’t directly visible in the application package.
After all, even to an expert, some of the components of the legitimate Pokémon GO app look suspicious at first sight:
In a programming ecosystem where names such as spacemadness.com.lunarmodule and javax.inject are unexceptionable, even a thinly digsuised malware component might effectively end up hidden in plain sight.
What to do?
What to do?
-
Avoid apps with a poor or non-existent reputation. Don’t trust an app about which no one yet seems to know anything.
-
Stick to Google Play if you can. Despite this and other recent failures, it’s still safer than unregulated Android markets where anything goes.
-
Use an Android anti-virus. The Sophos Mobile Security product is free, and protects you automatically from malicious and low-reputation apps.
-
Manage your business phones centrally. Sophos Mobile Control, for example, allows you to take control of options such as whether to allow untrusted app sources on phones used for work.
Via: sophos




Leave a Reply