Google announced on Wednesday plans to expand its Safe Browsing initiative aimed to protect users against social engineering attacks, such as deceptive online ads that install unwanted software or reveal personal information.
The Mountain View, California-based company said in a blog post it will begin to target embedded content on a web page that it considers social engineering. For example, ads that either:
-
Pretend to act, or look and feel, like a trusted entity – like a user’s device, or the website itself
-
Try to trick users into doing something they would only do for a trusted entity – like as sharing a password or calling tech support.
When Internet users visit a site with such deceptive content, Google Safe Browsing may warn users and offer the option to automatically report details of possible security incidents to Google:
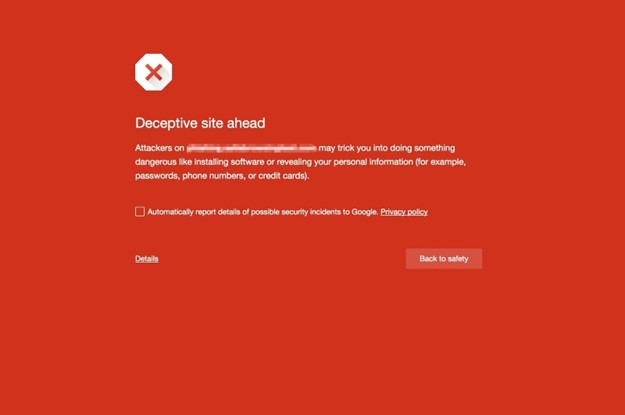
“You may have encountered social engineering in a deceptive download button, or an image ad that falsely claims your system is out of date,” explained Lucas Ballard, a senior staff engineer on the Safe Browsing Team.
The misleading buttons or ads are often not distinguishable from the rest of the page, says Ballard, as they appear like they will produce legitimate content that relates to the site.
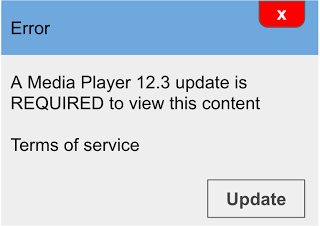
‘This image claims that your software is out-of-date to trick [users] into clicking ‘update’,” says Google.
“Our fight against unwanted software and social engineering is just beginning,” Ballard added. “We’ll continue to improve Google’s Safe Browsing protection to help more people stay safe online.”
The Safe Browsing technology is used by Google’s own Chrome browser, as well as Apple’s Safari and Mozilla’s Firefox browsers – protecting an estimated one billion people from potentially unsafe sites.
For webmasters whose sites have been flagged for social engineering content, Google suggests troubleshooting with Search Console and visiting its Social Engineering Help page.
Via: tripwire




Leave a Reply