Critical infrastructure runs your organization. It creates and delivers products and services. It is also used to collect and process customer information during operations. If these systems are compromised, operations fail and revenue is at risk.
Much appears in blogs, articles, and news reports about the security challenges facing critical infrastructure. Critical infrastructure is usually defined as energy and water processing and delivery systems. It goes beyond this, however, and is not government’s responsibility in most cases.
In this article, we define critical infrastructure in terms of what systems are required for the continued operation of a business. Our definition also includes high-risk processes involving intellectual property or customer identities. Examples include payment card processing systems, patient health delivery systems (such as operating room equipment), systems on the manufacturing floor, and supply chain distribution systems.
Also in this category are control systems used by your vendors to manage HVAC and other facility management services. Most organizations have not yet taken appropriate steps to protect critical infrastructure, including segmentation, protection, and detection controls.
The challenges
Figure A displays a flat network with both administrative and critical infrastructures on the same network. No separation exists between critical systems and admin systems. Information flows to and from critical systems with little or no control. Finally, users of critical systems have access to the Internet and remote attackers can potentially see these systems during scanning and enumeration steps.
Figure A
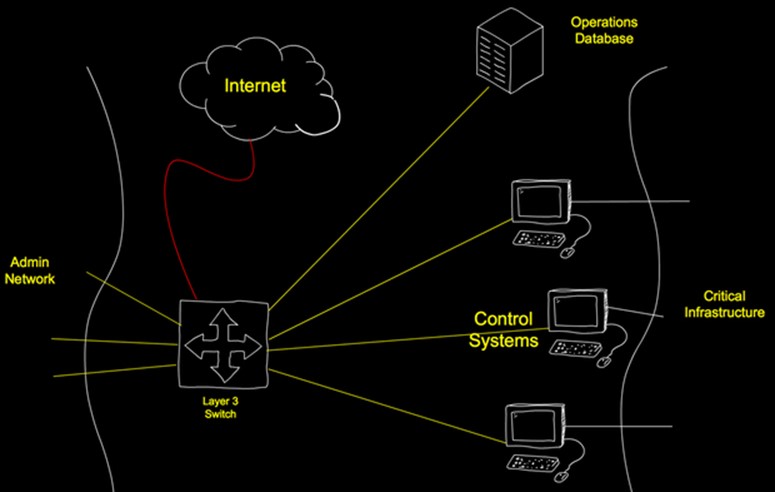
Flat Network
The Solutions
Segmentation
Let’s start with fixing one of the biggest risks in our Figure A sample organization. The network is not segmented. Ask Target how this worked for them. They will tell you they wish they had segmented their production network from their vendor support network.
Segmentation is also important for any business accepting payment cards for products and services. PCI DSS stipulates that payment card processing should be separate from Internet access and from networks where Internet access is allowed. The PCI Council also advises to place payment card systems on their own isolated segment to streamline compliance assessments.
Finally, no manufacturing or other critical operations management systems should be part of the administrative network. If this is not possible, these management systems should at least be blocked from Internet access.
Figure B depicts a segmented network. A layer 3 core switch separates the admin (highlighted in yellow) and critical systems (highlighted in red) into two VLANs. A VLAN access control list prevents traffic from flowing to the critical systems from the admin VLAN. Further, Internet access is only allowed for admin VLAN systems. Internet access is blocked for critical system users. No critical system user should be able to use the Internet… period.
Figure B
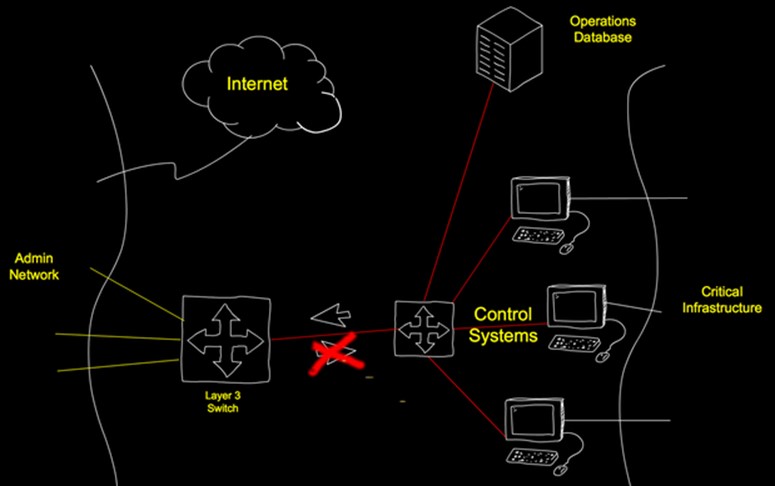
VLAN Segmentation
In addition to blocking Internet traffic, all information created on the critical system VLAN are pushed to explicitly allowed business management systems. No traffic is allowed to pass the other way.
Air gaps are sometimes used to achieve this separation, but air gaps are not appropriate in many cases. For example, payment card or manufacturing systems must report information to admin systems. This requires movement of large amounts of information. Use of mobile storage for this, as we see next, is a security issue all by itself.
Mobile Storage Restrictions
As always, security must be applied to harden the critical systems. We start by disallowing use of mobile storage, as shown in Figure C. These devices are commonly used to trick a user into installing malware or to access devices once the attacker gains physical access.
Figure C
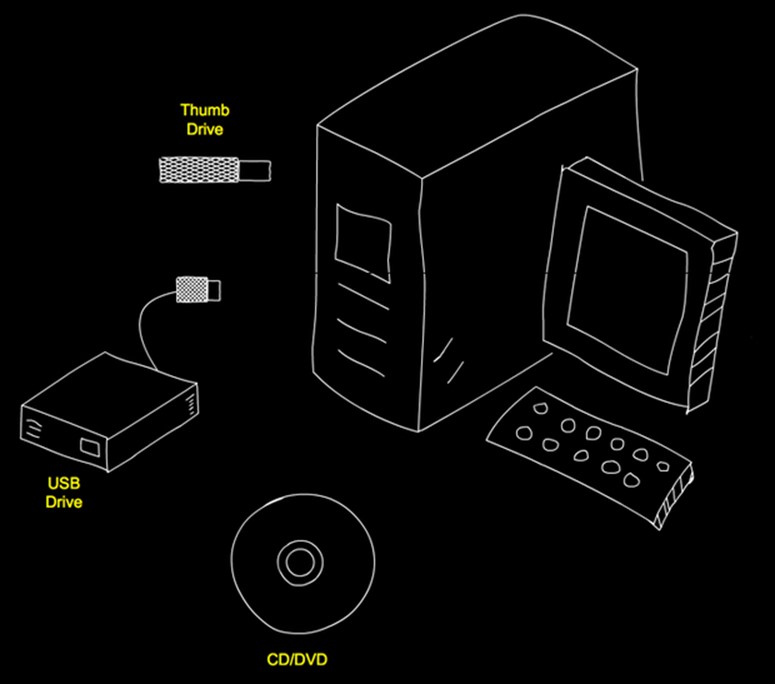
Mobile Storage
Under no circumstances should we allow use of mobile storage on critical systems for anything other than system maintenance, including shutting down the use of CD/DVD drives. This is possible via GPO settings and the use of third-party security apps.
Logical and Administrative Controls
Although not shown in Figure D, system hardening via software configuration begins by shutting down unused ports and services as well as removing all applications not needed for day-to-day operations management.
Figure D
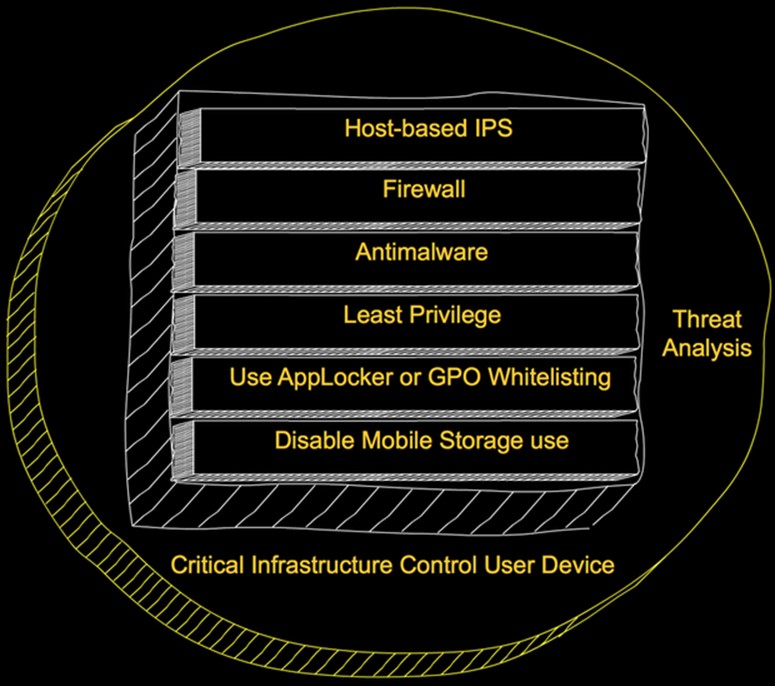
Endpoint Security Layers
In addition to disabling mobile storage, we also block users from installing or running unapproved applications. This is easily done on Windows systems with AppLocker or software restriction policies. In either case, we only allow installation and execution of whitelisted applications. We also remove the capability of any non-administrator account from installing applications on the critical management user devices.
We allow no one to operate critical systems with unrestricted user accounts. Enforcement of least privilege is always important. This is enforceable with authentication and authorization processes. AppLocker can also be applied by user or group to reach for role-based access control.
Next, the old standbys of antimalware, firewall, and host-based IPS fill the remaining prevention gaps. They also begin the threat analysis process. Threat analysis involves log aggregation, correlation, and threat intelligence. It requires us to look for the inevitable breach and manage it quickly.
Finally, patch, patch, patch… and patch.
The Final Word
Most of the controls listed in this article have been best practices for years, and many organizations use them. However, project specific risk assessments might miss or ignore the dangers when placing critical systems on existing network segments. Configuration documentation specific for critical systems might not exist resulting in use of common business device build documentation. Further, policies addressing critical systems are often missing from the security program. Secure configuration and management of critical systems requires relevant policies, procedures dedicated to building and managing critical systems, and a trained IT staff.
Via: csoonline




Leave a Reply