Why you need to know about the new variant of Locky ransomware.
After infecting computers with recurring malicious email campaigns sent to random recipients in organizations from all over the world, Locky ransomware strikes again.
Locky’s persistence is already famous, as cyber criminals use it frequently to exploit vulnerabilities in outdated systems. The most recent campaign, which started late last night, uses a new extension called .lukitus and has been discovered by Rommel Joven. As expected, Internet users can get their files back, after paying a ransom required by attackers.
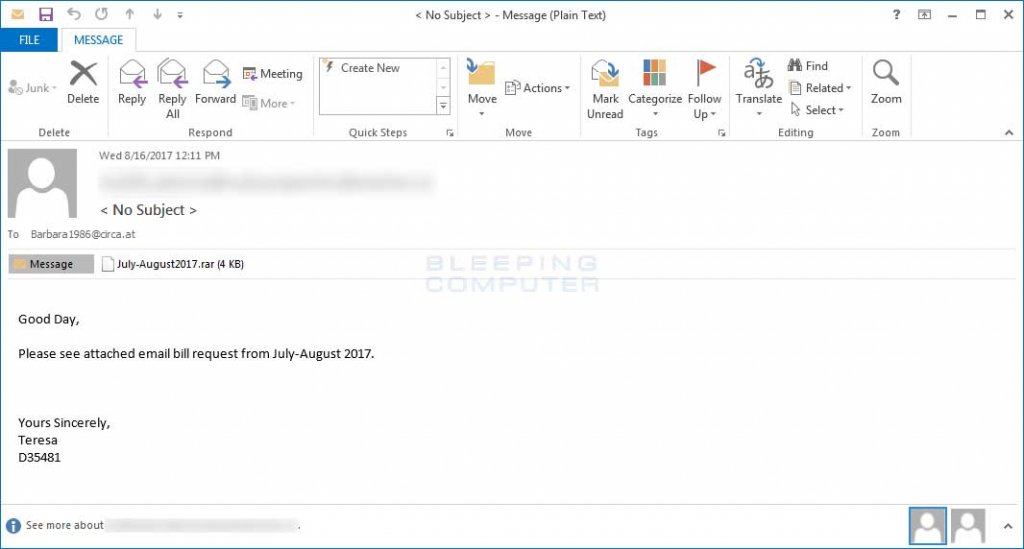
The malicious email arrives into users’ inboxes with the following subject lines:
< No Subject > or Emailing – CSI- [0-9] * _ MB_S_ [A-z0-9]
The email also includes zip or rar attachments with JS files. When these files are executed, they will download the payload from various malicious URLs, like the ones in the selection below (sanitized for your online safety):
http: // angel demon [.] com / jbYUF6D
http: // Antibody Services [.] net / jbYUF6D
http: // ttytreffdrorseder [.] net / of / jbYUF6D
http: // asliozturk [.] com / jbYUF6D
http: // antwerpiastamps [.] BE / jbYUF6D
This is another variation of the same attack, spotted yesterday as well:
Source: Bleeping Computer
To ensure that Locky can communicate with its underlying C&C servers unhindered, a DGA (Domain Generation Algorithm) is also used, which provides the following domains and many, many more (sanitized for your online safety):
http: // sorqjivpyfrwlo [.] Click / imageload.cgi
http: // dxeqiniexovy [.] org / imageload.cgi
http: // kokalgfsnepogq [.] ru / imageload.cgi
http: // kljidoejmiqx [.] org / imageload.cgi
http: // jcanepkjyu [.] biz / imageload.cgi
Once the files are downloaded and executed, they start scanning the user’s computer and encrypting system files, modifying their names with the following format:
[first_8_hexadecimal_chars_of_id]-[next_4_hexadecimal_chars_of_id]-[next_4_hexadecimal_chars_of_id]-[4_hexadecimal_chars]-[12_hexadecimal_chars].lukitus.
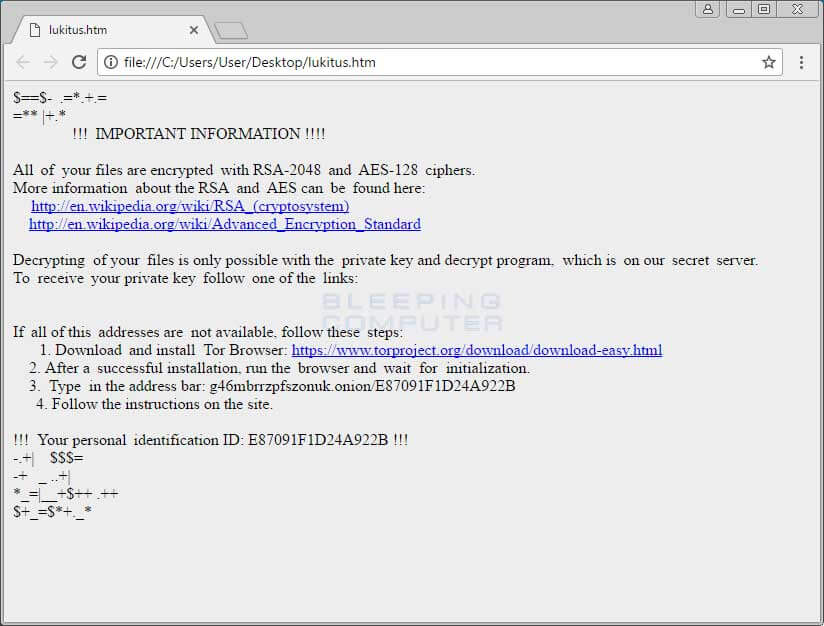
After the encryption is done, Locky removes the downloaded executable, and shows a ransom note – having these names: lukitus.htm and lukitus.bmp – on users’ display on how they can pay it and get their files back.
This is how a message with the Locky Lukitus Ransom Note appears on an infected computer display:
Source: Bleeping Computer
Although there are a sum of decryption tools out there to unlock your data for free, this Locky Ransomware Lokitus variant remains still unbreakable with no possibility to decrypt .lukitus files for free.
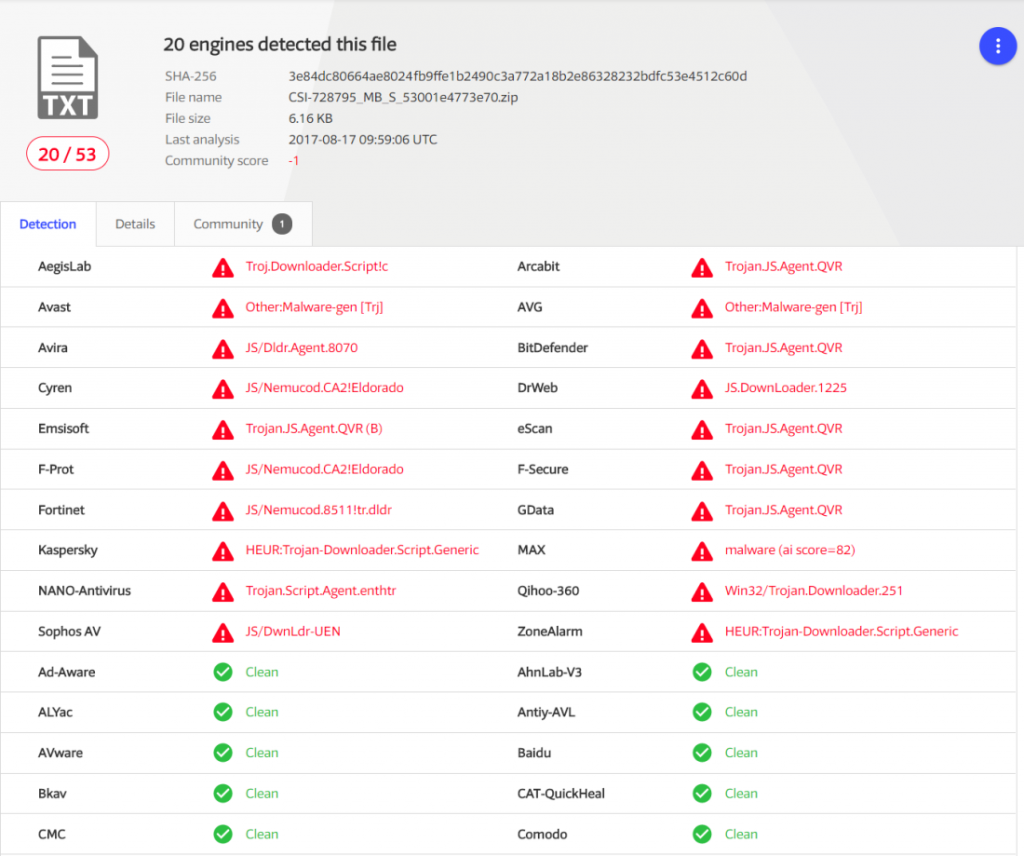
Initially, VirusTotal showed that 7 of 53 antivirus solutions were detecting this malicious file at the time it was posted. After a new and recent analysis, more engines (20 of 53 antivirus products) also identify this threat.
Source: VirusTotal
Here’s what you can do to protect from this new ransomware attack:
- Backup, backup and backup again! Make sure you have at least 2 backups of your important data on external sources such as a hard drive or somewhere located in the cloud (Google Drive, Dropbox, etc.). This guide shows how to do it.
- Update, update and update again! Once again, we remind users to install all the latest updates for their apps installed on the device, including the operating system.
- Do not open, download email (messages) or click on suspicious links received from unknown sources that could infect your device.
- Make sure you have a security software product (antivirus) that is updated or use a proactive security product to block access to infected domains or servers.
Ransomware attacks are on the rise and continue to appear in different forms. Once again, we remind you about the importance of being proactive and taking all needed security measures to protect your sensitive data.
via: heimdalsecurity




Leave a Reply