Trend Micro spotted yet another threat lurking around social media sites targeting users of either Google Chrome or Mozilla Firefox. This threat uses fake extensions for both browsers to infiltrate user systems and hijack social media accounts – specifically, Facebook, Google+, and Twitter accounts.
To install these fake extensions, users would see various lures on social media sites to try to get users to install a fake video player update. In reality, this player update is a malicious file detected as TROJ_FEBUSER.AA, installs a browser plugin depending on the browser currently being used.
One earlier version we saw for Google Chrome, detected as JS_FEBUSER.AA, identifies itself as Chrome Service Pack 5.0.0. In the case of Mozilla Firefox, the fake plugin is Mozilla Service Pack 5.0.
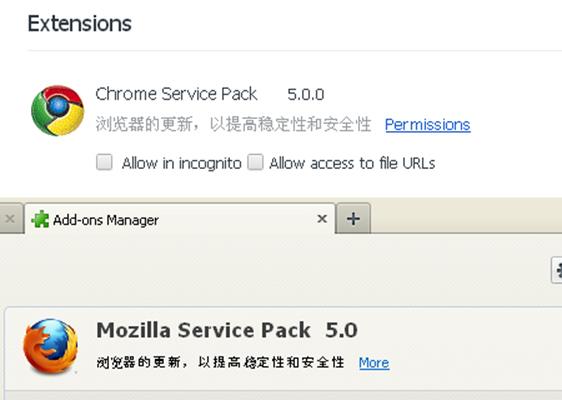
Figure 2. Names used by the malicious plugin
Google Chrome has since flagged this particular plugin as malicious. An updated version of the plugin, detected as JS_FEBUSER.AB, is identified as F-Secure Security Pack 6.1.0 (for Google Chrome) and F-Secure Security Pack 6.1 (for Mozilla Firefox) .
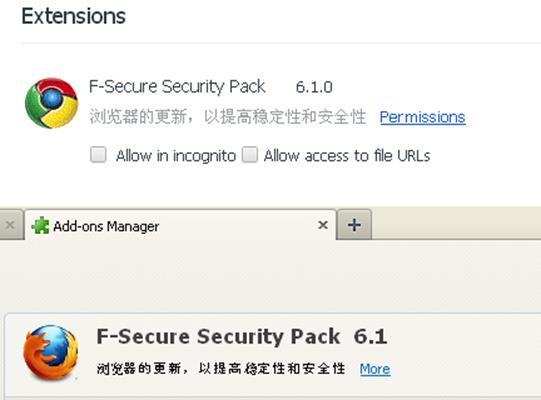
Figure 3. Names used by the updated malicious file
Once installed, it connects to a malicious URL to download a configuration file. It uses the details on that configuration file to hijack the user’s social media accounts and perform the following actions, without any authorization from the user:
- Like pages
- Share posts
- Join a group
- Invite friends to a group
- Chat with friends
- Post comments
- Update status
This threat tries to perform the above actions on three different social networks: Facebook, Google+, and Twitter. Because of this, in effect, the attackers are able to hijack the accounts of the users and could, for example, use them to spread links to other malicious sites.
One more thing to note: the fake video player update is digitally signed. Digital signatures are a way for developers and publishers to prove that a file did come from them and has not been modified. Potential victims may take this to mean that the file is legitimate and harmless.
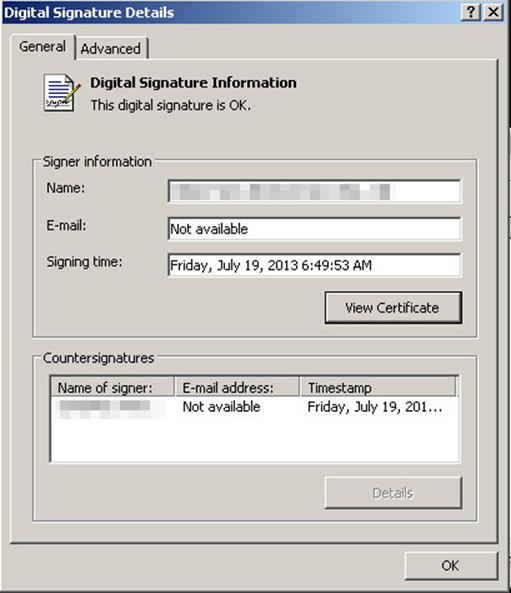
Figure 5. Valid digital certificate of the malicious video player update file
It is not yet clear if this signature was fraudulently issued, or a valid organization had their signing key compromised and used for this type of purpose.
Users are once more reminded to always be aware and vigilant of such scams. Cybercriminals are getting better at making their lures much more convincing, even resorting to abusing legitimate services and users in order to appear legitimate.
Via: trendmicro




Leave a Reply