Microsoft released eight security patches to protect machines from nasty tricks such as three zero-days. After adding in Oracle and Adobe patches, and you’ve protected all machines under your care, then it’s time to treat yourself to whatever makes you happy.
Ladies and gentlemen, for this National Cyber Security Awareness month, prepare yourself for a monster load of patches and restarts. Microsoft released nine Security Bulletins, but only eight security patches. Although there are five patches for remote code execution vulnerabilities, Microsoft rated only three of those as “Critical.” Since RCE-flavored vulnerabilities can allow an attacker to take control and execute code on your PC, it seems wise to patch all RCE bugs ASAP as if they were all rated Critical. Three of these RCE fixes are for zero-days being exploited in the wild.
Sandworm
You’ll want to patch CVE-2014-4114 with MS14-060 as a vulnerability in the OLE package manager can be exploited to remotely execute arbitrary code in Microsoft Windows versions Vista SP2 to Windows 8.1 and in Server 2008 and 2012. iSight, working in “close collaboration with Microsoft”—since before September Patch Tuesday, has tracked and monitored the exploitation of the vulnerability in the wild. A Russian cyber-espionage campaign dubbed “Sandworm” was used against targets including a U.S. academic organization, NATO, Ukrainian and Western European government organizations, European telecommunication firms and energy sector firms in Poland.
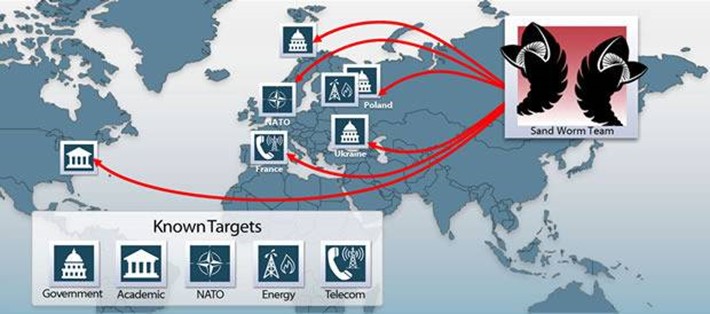
iSight added:
The vulnerability exists because Windows allows the OLE packager (packager .dll) to download and execute INF files. In the case of the observed exploit, specifically when handling Microsoft PowerPoint files, the packagers allows a Package OLE object to reference arbitrary external files, such as INF files, from untrusted sources.
This will cause the referenced files to be downloaded in the case of INF files, to be executed with specific commands. An attacker can exploit this vulnerability to execute arbitrary code but will need a specifically crafted file and use social engineering methods (observed in this campaign) to convince a user to open it.
Let that be a lesson to highlight one more reason never to use PowerPoint again….just kidding. However, patching the vulnerability is no joke.
Despite the name, Sandworm “is not a ‘worm’ in the sense of computer virus that can self-propagate.” (It’s a hat tip to killer worms in the movie Dune.) Ross Barrett, senior manager of security engineering at Rapid7, added, “The average system administrator or home users should not panic about Sandworm.…This is a local file format exploit” and “not a remote.” Nevertheless, Microsoft’s deployment chart shows it as an “Important” fix for an RCE.
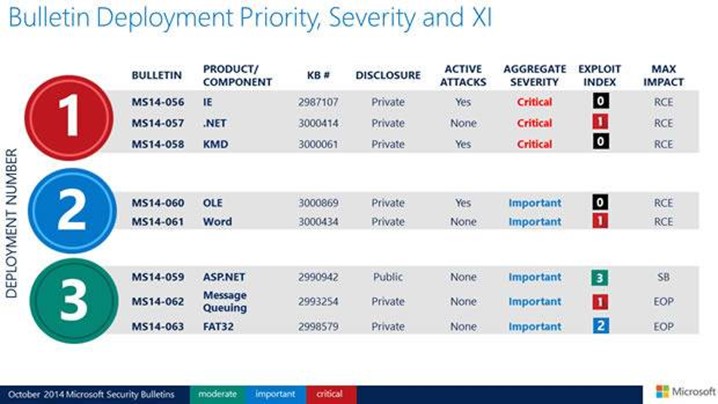
3 Critical RCE vulnerability patches
Microsoft’s deployment schedule shows three zero-days, yet only two of those are rated Critical and suggested to be deployed first.
MS14-056 closes 14 privately reported RCE bugs in Internet Explorer. It’s listed as a top priority for deployment with an exploitability index of zero meaning it’s in the wild. It’s rated Critical for IE 6 – 11 on Windows clients and moderate for IE 6 – 11 on Windows Servers 2008 and 2012.
MS14-058 fixes two privately reported RCE flaws in Microsoft Windows kernel-mode driver. It is rated as Critical and affects all supported versions of Windows. It is the second zero-day Microsoft patched this month.
MS14-057 resolves three privately reported RCE vulnerabilities in Microsoft’s .Net framework. Rated Critical, it has an exploitability index of one.
5 patches for vulnerabilities rated as Important
The two RCE fixes rated as Important are MS14-060 and MS14-061. MS14-060 addresses the zero-day OLE “Sandworm” vulnerability revealed by iSight. MS14-061 patches one privately reported flaw in Microsoft Office, specifically “Microsoft Word 2007, Microsoft Office 2007, Microsoft Word 2010, Microsoft Office 2010, Microsoft Office for Mac 2011, Microsoft Office Compatibility Pack, Word Automation Services, and Microsoft Office Web Apps Server 2010.” Microsoft recommends deploying these two patches second.
MS14-062 and MS14-063 are the fixes for elevation of privilege flaws. MS14-062 addresses a publicly disclosed hole in Microsoft Windows Message Queuing Service and is rated as “Important” with an exploitability index of one for all supported editions of Windows Server 2003. “Successful exploitation of this vulnerability could lead to full access to the affected system.”
Rated as Important for all supported editions of Windows Server 2003, Windows Vista, and Windows Server 2008, MS14-063 resolves one privately reported EoP bug “in the way the Windows FASTFAT system driver interacts with FAT32 disk partitions.” Microsoft rates it as a two on its exploitability index.
MS14-059 fixes one publicly disclosed security feature bypass bug in ASP.NET MVC, specifically ASP.NET MVC 2, ASP.NET MVC 3, ASP.NET MVC 4, ASP.NET MVC 5, and APS.NET MVC 5.1. It’s recommended as one of three patches to be deployed third, but is the only one this month with an exploit index of three.
Microsoft “revised Security Bulletin
MS14-042: Vulnerability in Microsoft Service Bus Could Allow Denial of Service (2972621) and Security Advisory 2755801: Update for Vulnerabilities in Adobe Flash Player in Internet Explorer.” Tracey Pretorius, Director of Microsoft’s Response Communications, added:
Microsoft also announced upcoming updates to the out-of-date ActiveX control blocking feature. Beginning November 11, 2014, the out-of-date ActiveX control blocking feature will automatically be expanded to block outdated versions of Silverlight, in addition to outdated versions of Java. It is also being expanded to support Internet Explorer 9 on Windows Vista SP2 and Windows Server 2008 SP2.
You can grab Adobe’s patch for Flash Player here and hotfixes for ColdFusion here. Adobe promised it will soon release a patch for the privacy hole in Digital Editions 4.
But wait, there’s more! Lucky you, Oracle rolled out its quarterly critical patch update which includes 155 security fixes “across ‘hundreds’ of Oracle products.”
After you’ve protected all machines under your care from any nasty tricks, then it’s time to treat yourself to chocolate and a beer (or whatever makes you happy). Happy patching!
Via: networkworld




Leave a Reply