Short Bytes: Two malware which go by the name FruitFly and FruitFly 2 have been discovered over the course of the last few months, starting Janaury this year. The malware, known to have infected hundreds of Macs, are being assumed as surveillance tools instead of some ransomware or some other type of malware.
Adistant malware, designed to infect Apple’s macOS, is leaving a bewildered look on the face of the security researchers. The first variant of the malware called FruitFly, aka the first Mac malware of 2017, was discovered earlier this year by the security firm Malwarebytes and analyzed by Thomas Reed.
Back then, an IT admin at the firm had spotted some unusual outgoing traffic from a particular Mac. The “simplistic” malware consisted of only two files, carrying some “ancient” obfuscated Perl. Some of the code even dates back to 1998, before the existence of macOS. The malware could take screenshots, log keystrokes, spy through web cams, and it was known to have targeted some biomedical research centers as well. According to Malwarebytes, an update was released by Apple to take care of the same.
Fast forward a few months, another malware with similarities to FruitFly was detected by ex-NSA hacker Patrick Wardle who is now a security researcher at Synack. Known as FruitFly 2, it’s assumed that the malware is in existence for a decade or so, undetected by many antivirus software.
During the breakdown, Wardle found that FruitFly 2 could connect to a C&C server and send the data back to to the hackers, Motherboard reports. Backup servers were also present if some issues occur with the primary ones. More than 400 victims were discovered when Wardle infected his virtual machine after registering a domain that hackers planned to use as a backup.
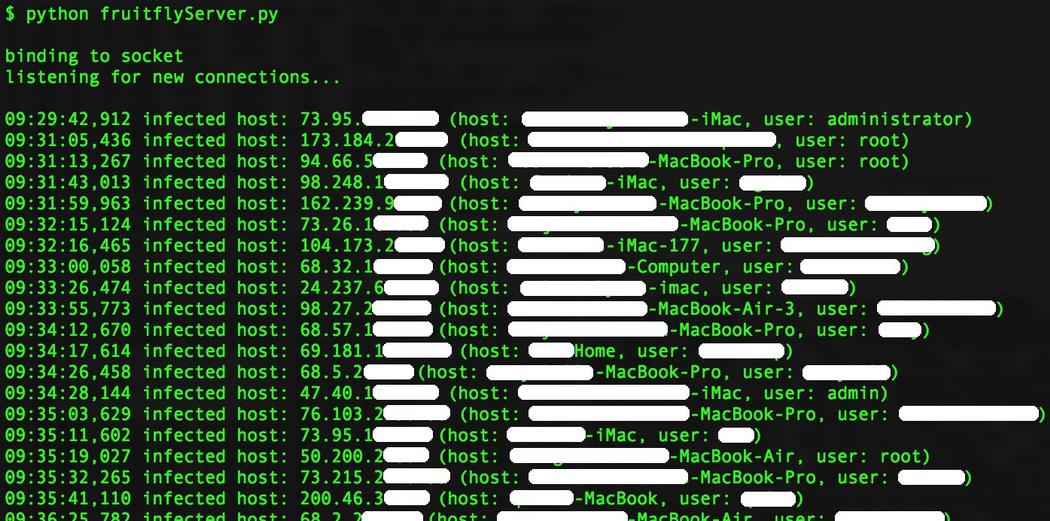 List of detected IP addresses. (Credit: Patrick Wardle/Twitter)
List of detected IP addresses. (Credit: Patrick Wardle/Twitter)
He could see the IP addresses of the victims and even the names of the Mac computers. However, this number might increase as Wardle didn’t have access to all the C&C servers used to control the malware. Wardle contacted law enforcement and reported his findings. He has also talked about his findings at this year’s Black Hat conference.
Both Wardle and Reed are unaware of the origins of malware, who made it, and what is its purpose. In the case of the Wardle, around 90 percent of the FruitFly 2 victims are living in the US or Canada.
The possibility of the malware being baked by a federal body gets thinner as the malware isn’t sophisticated enough and it hasn’t targeted any high-profile individuals, writes Motherboard. FruitFly 2 isn’t a ransomware and it doesn’t log keystrokes. But, according to Wardle, both FruitFly malware might have been designed to perform surveillance.
FruitFly 2 is also written in Perl and allows the attacker to control the mouse and keyboard remotely. It even notifies the attacker when the victim starts using the mouse and keyboard.
Wardle said that malware seems to have been to target specific individuals, maybe normal Mac users or families, but the intentions are unclear. He calls the situation “worrisome.” He warns Mac users to be cautious while using their machines. “Just because they have a Mac, it doesn’t mean that they’re safe.”
via: fossbytes




Leave a Reply