Security researchers have released several new decryption tools for TeslaCrypt ransomware following the publication of its master decryption key.
Slovakian IT security firm ESET explains they have been tracking TeslaCrypt for months. Most recently, the malware has been spotted in spam campaigns involving fake Visa Rewards offers as well as exploit kit attacks.
After learning its developers intended to abandon the crypto-ransomware, ESET decided to reach out in an effort to obtain its master decryption key.
They did not foresee what would happen next. As the security firm explains in a blog post:
“On this occasion, one of ESET’s analysts contacted the group anonymously, using the official support channel offered to the ransomware victims by the TeslaCrypt’s operators, and requested the universal master decryption key. Surprisingly, they made it public.”
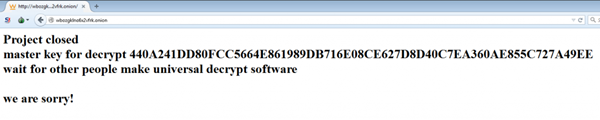
Since the release of that universal master decryption key, both ESET and researchers at BleepingComputer.com have created their own up-to-date decryption tools, which are available here and here for download.
This is not the first instance security researchers have released a decryption tool for TeslaCrypt. Analysts at BitDefender created such a utility back in March, but it is unclear whether that particular tool could work against all versions of the crypto-ransomware.
By contrast, ESET’s and Bleeping Computer’s tools make use of the master decryption key, which means they can decrypt files affected by any of TeslaCrypt’s iterations.
While TeslaCrypt might be out-of-commission, ESET is careful to point out that users still remain at risk of infection from other forms of ransomware.
“We must stress that ransomware remains one of the most dangerous computer threats at this moment, and prevention is essential to keep users safe.”
Users should avoid clicking on suspicious links, implement vendor patches as soon as they become available, and back up their important data just in case they experience an infection.
For more ransomware prevention tips, please click here.
Via: tripwire




Leave a Reply