Learn about a new type of ransomware that has the potential to snare many victims – and it’s not even malware.
Some of you may be familiar with ransomware, and how to avoid being conned by it. The trouble is there are millions of people who aren’t. That alone ensures ransomware will continue to cull people of their hard-earned money. To make matters worse, there’s a new version winding its way through the Internet. And, those in the know predict what’s being called HTML ransomware will be more successful than previous versions.
HTML ransomware
I first learned about HTML ransomware from Jerome Segura, Senior Security Researcher at Malwarebytes, and his blog post, “FBI Ransomware Now Targeting Apple’s Mac OS X Users.” Initially, I was suspicious; OS X is not vulnerable in the same way Windows operating systems are, so what’s up?
As I continued reading, I learned the only requirements for HTML ransomware to work are JavaScript must be enabled, and the victim’s web browser incorporates the “Recover browser session after a crash” feature, which is part and parcel to all major web browsers — including Chrome, Firefox, Internet Explorer, and Safari.
Here’s what HTML ransomware has going for it:
- Does not require installation.
- Disabling JavaScript breaks many popular websites; so people aren’t willing to turn off JavaScript, something the bad guys are relying on.
- AV applications, even with current malware signature sets, are of no use against HTML ransomware.
How it works
One way the scam starts is when an unlucky person selects a search result with a falsified link. Instead of the expected web page being presented, the victim’s web browser loads something similar to the following slide (courtesy of Jerome Seguro and Malwarebytes).
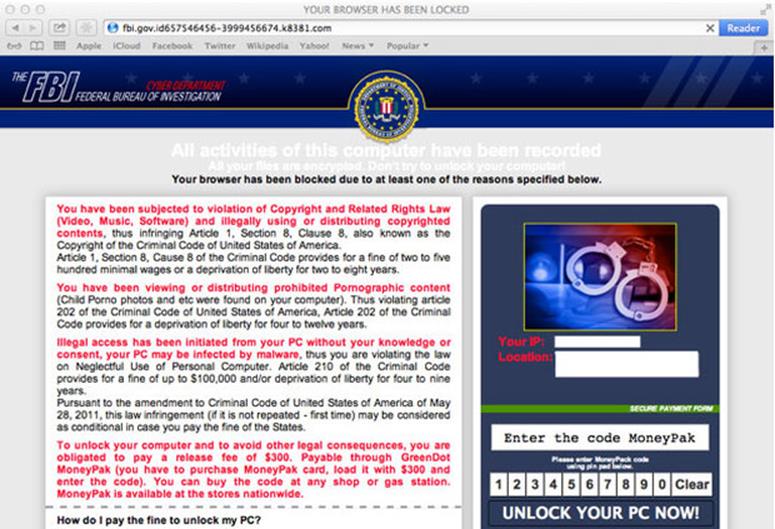
While the victim is coming to grips with the above screen, associated JavaScript code is loading copies of the same screen (150 typically) onto the browser. By creating a 150 iFrame loop, HTML ransomware gives the impression the computer is locked up. Ironically, if the victim is determined, leaving the web page, and revisiting it 150 times will remove the problem.
I doubt I’d even consider reloading the web browser that many times; my inclination would be to reboot the computer, but that doesn’t help either because HTML ransomware taps into the “Recover browser session after a crash” feature I mentioned earlier, bringing the same FBI screen back up.
It’s not malware
Something else that makes HTML ransomware unique: by most definitions, it’s not malware. It is a snippet of JavaScript code readily available on the Internet that digital extortionists use to fool victims by controlling what is visible in the browser window. No other computer function is affected, at least as of this writing, but Jerome mentioned the potential is there, especially for Windows-based computers.
It not being malware is why HTML ransomware is a great idea for the bad guys: simple to set up, easy to move to different domain names, and no concerns on how to install code onto computers. To see if bad guys agreed, we can look at how many instances of HTML ransomware have been seen?
“This ransomware is quite active; bad guys are registering new domain names several times per day. While it is not malicious (as opposed to ransomware that infects your PC), it’s still scaring people.”
How to tell if it’s HTML ransomware
Web browsers lock up for all sorts of reasons, so I asked Jerome how we would know for sure, if HTML ransomware caused the lockup:
“The browser being locked may not be ransomware in all cases. I can think of many sites that use annoying JavaScripts to keep the user on the page (pop-ups that ask ‘are you sure you want to leave this page?’). HTML ransomware is characterized by the following:
- Warning from the police
- Fee to be paid using a voucher
- Computer or browser locked
“If those three elements are in place, it’s HTML ransomware.”
How to get rid of HTML ransomware
Jerome did a thorough job of explaining how to remove HTML ransomware from Safari in his blog post, but missed explaining what those using other operating systems should do. Here’s what others should do:
“I recommend ending the web-browser process(es) after first having disabled JavaScript. Simply killing the web-browser process will recover the ransomware page and put you right back where you started.”
There is a possibility you may not have to worry about HTML ransomware if your antimalware provider is on top of the situation like Malwarebytes.
“Malwarebytes has a large database of malicious sites that is constantly updated. The PRO users are protected against malicious websites as they pop up. This is due to it’s ability to blacklist entire IP ranges since they know they are only used for criminal purposes; any new website registered on those will be automatically blocked.”
Final thoughts
At first, I felt that HTML ransomware was not a big deal. But, it did not take long for me to realize darn near everything we do computer-wise involves the web browser. And, if the web browser appears to be locked up, it will seem like a huge deal.
Since this attack is easy to fix, it would be a shame to have those who do not understand what’s going on even for a second consider paying the ransom. So, please, let’s get the word out on HTML ransomware.
Via: techrepublic




Leave a Reply