Security researchers published details yesterday on a new ransomware for Mac, which calls itself “Patcher.” The file-encrypting ransomware program finds its way onto macOS systems through BitTorrent websites, masquerading as an Adobe Premiere CC or Office 2016 patcher. Intego’s malware research team has updated its VirusBarrier anti-virus definitions to detect all components of the ransomware, identified as OSX/Filecoderand OSX/Filecoder.fs.
What is the Infection Vector?
A torrent claiming to contain a patcher for Adobe Premiere CC 2017 or Office 2016 is the only delivery mechanism known so far. Macs running OS X 10.11.x El Capitan and macOS 10.12.x are at risk.
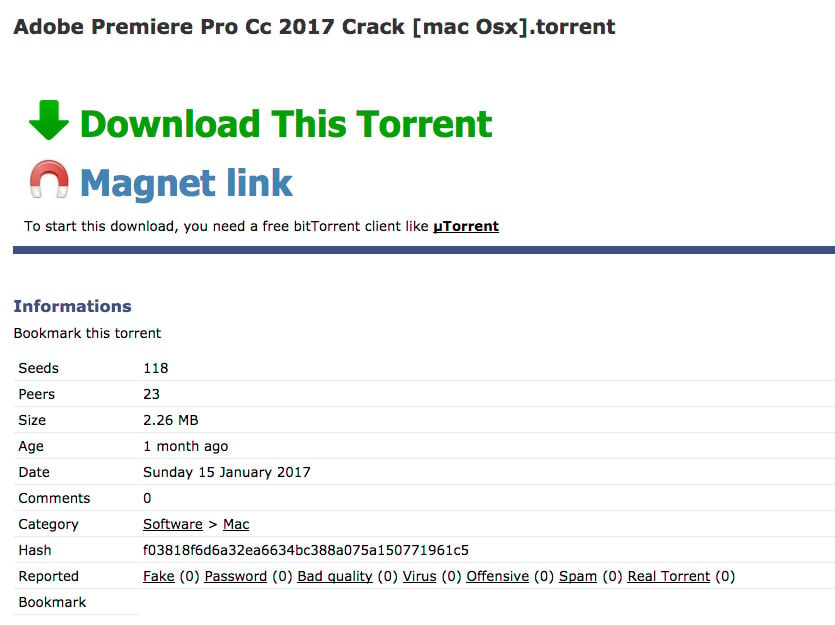
Patcher was found on the bittorrent site seedpeer[.]eu
Patcher does not appear to be concerned about where it runs or if any security software is present. The application is signed with a key that is not signed by Apple.
codesign -dv /Users/intego/Desktop/Office\ 2016\ Patcher.app
Executable=/Users/intego/Desktop/Office 2016 Patcher.app/Contents/MacOS/Office 2016 Patcher
Identifier=NULL.prova
Format=app bundle with Mach-O thin (x86_64)
CodeDirectory v=20100 size=507 flags=0x2(adhoc) hashes=11+3 location=embedded
Signature=adhoc
Info.plist entries=22
TeamIdentifier=not set
Sealed Resources version=2 rules=12 files=14
Internal requirements count=0 size=12
The bundle identifier “NULL.prova” was found in another application, named “prova,” which is similar in appearance.
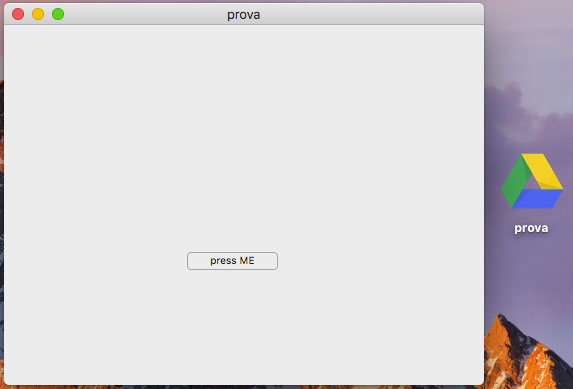
prova application
codesign -dv /Users/intego/Desktop/prova.app
Executable=/Users/intego/Desktop/prova.app/Contents/MacOS/prova
Identifier=NULL.prova
Format=app bundle with Mach-O thin (x86_64)
CodeDirectory v=20100 size=411 flags=0x2(adhoc) hashes=8+3 location=embedded
Signature=adhoc
Info.plist entries=22
TeamIdentifier=not set
Sealed Resources version=2 rules=12 files=14
Internal requirements count=0 size=12
The prova application, designed to have the same or similar ransomware functionality, does not appear to be functional and may just have been a test run leading up to the currently discussed Patcher app.
According to the researchers, the application appears to be poorly coded as the window is transparent. A quick overview in the code confirms that it was written using Swift:
0000000100008098 dq 0x0000000000000040 ; DATA XREF=-[_TtC34Adobe_Premiere_Pro_CC_2017_Patcher11AppDelegate count]+4, -[_TtC34Adobe_Premiere_Pro_CC_2017_Patcher11AppDelegate setCount:]+4, sub_100001940+105, -[_TtC34Adobe_Premiere_Pro_CC_2017_Patcher11AppDelegate init]+105, sub_100001ee0+31, 0x100007460
00000001000080a0 dq __swift_FORCE_LOAD_$_swiftFoundation
00000001000080a8 dq __swift_FORCE_LOAD_$_swiftObjectiveC
00000001000080b0 dq __swift_FORCE_LOAD_$_swiftDarwin
00000001000080b8 dq __swift_FORCE_LOAD_$_swiftIOKit
00000001000080c0 dq __swift_FORCE_LOAD_$_swiftDispatch
00000001000080c8 dq __swift_FORCE_LOAD_$_swiftCoreGraphics
00000001000080d0 dq __swift_FORCE_LOAD_$_swiftAppKit
00000001000080d8 dq __swift_FORCE_LOAD_$_swiftCoreImage
00000001000080e0 dq __swift_FORCE_LOAD_$_swiftXPC
00000001000080e8 dq __swift_FORCE_LOAD_$_swiftQuartzCore
00000001000080f0 dq __swift_FORCE_LOAD_$_swiftCoreData
Code between the Adobe Premiere CC and Office 2016 applications are the same.
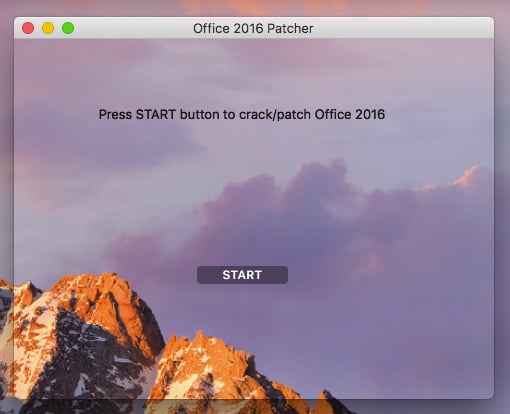
Patcher’s application window
Clicking the START button immediately starts the encryption process, and the window shows progress in 3 steps.
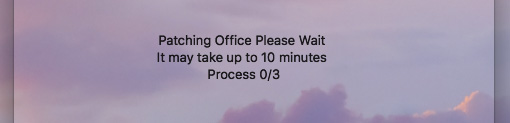
Progress window, step 0 of 3
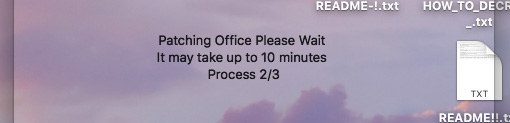
Progress window, step 2 of 3
By the time the window shows step 2/3, an infected Mac will see its desktop loaded with text files. Of course, the progress window is just there to delay the user while all the files are encrypted in the background. Even if the application is quit at this point it will be too late, because when the text files appear on the desktop all of the contents in the Users folder is already encrypted. When the window shows step 2/3, it’s already done; step 3/3 never comes and the application just sits there indefinitely.
Any new data created while Patcher is running will not be encrypted by the ransomware. Patcher appears to focus only on data that was present when the application was first started.
The original data that was encrypted is deleted using rm, Patcher then attempts to wipe the free space on the drive with diskutil to make sure the original data is really gone. Luckily, the author made a mistake in the ransomware:
It tries to execute /usr/bin/diskutil, however the path to diskutil in macOS is /usr/sbin/diskutil.
This mistake may give a user the chance to recover some of the deleted data by using tools such as Data Rescue. If the ransomware is discovered promptly, which shouldn’t be a problem as the numerous text files on the desktop are a solid indicator that something is wrong, and the Mac is shut down, data recovery may have a chance. The longer the Mac is powered on, the greater the chances are the deleted files are overwritten.
It is also possible to interrupt Patcher simply by quitting the application. Patcher is very slow, taking a good 30 seconds to encrypt a 250MB video file, so it will need a decent amount of time to encrypt a typical user folder, which can be hundreds of gigabytes. If the user suspects the application is not working or is not what it claims to be, it can be closed and the encrypting of data will stop.
Where Does Filecoder Install?
Filecoder is a stand-alone application that does not install files on the system to keep itself alive after a restart. It simply takes your user home folder and encrypts everything in it. The application appears to disable itself, so it cannot be launched again. When it’s done disabling itself, it goes after any mounted network volumes and connected external drives. It leaves the system folder, library and applications folders alone, going only after files in the Users folder.
As soon as Patcher runs, the user will see text files popping up on the desktop and in other user home folders, with names like “README.txt” and “DECRYPT!.txt.” Opening these text files will present the following information:
NOT YOUR LANGUAGE? USE https://translate.google.com
What happened to your files ?
All of your files were protected by a strong encryption method.What do I do ?
So , there are two ways you can choose: wait for a miracle or start obtaining BITCOIN NOW! , and restore YOUR DATA the easy way
If You have really valuable DATA, you better NOT WASTE YOUR TIME, because there is NO other way to get your files, except make a PAYMENTFOLLOW THESE STEPS:
1) learn how to buy bitcoin https://en.bitcoin.it/wiki/Buying_Bitcoins_(the_newbie_version)
2)send 0.25 BTC to 1EZrvz1kL7SqfemkH3P1VMtomYZbfhznkb
3)send your btc address and your ip (you can get your ip here https://www.whatismyip.com) via mail to rihofoj@mailinator.com
4)leave your computer on and connected to the internet for the next 24 hours after payment, your files will be unlocked. (If you can not wait 24 hours make a payment of 0.45 BTC your files will be unlocked in max 10 minutes)KEEP IN MIND THAT YOUR DECRYPTION KEY WILL NOT BE STORED ON MY SERVER FOR MORE THAN 1 WEEK SINCE YOUR FILE GET CRYPTED,THEN THERE WON’T BE ANY METHOD TO RECOVER YOUR FILES, DON’T WASTE YOUR TIME!
After your data is encrypted, you are instructed to pay 0.25 bitcoin ($280) to have your files unlocked within 24 hours. If you’re in a rush, however, you can pay 0.45 bitcoin ($500) and your files will be unlocked in 10 minutes or less.
Looking at the previously mentioned prova application, the readme.txt mentions the same bitcoin address but a different email address: “rihofoj@zainmax.net.” In Patcher, the name ‘rihofoj’ uses the mailinator service instead of the zainmax.net domain.
Even if one would be inclined to pay the ransom (which we do NOT recommend), there is a problem. Filecoder never actually sends a decryption key to a server or makes a network connection of any kind. This means the ransomware author does not have a way to unlock your files even if you pay.
When the patcher application is launched, everything currently in your home folder is encrypted. Any new files or folders, even those created while the patcher is running, are not touched. A reboot will have you greeted with a “Sign in to iCloud” window, just like the one you see when you first log in to your Mac. You’ll also find all your settings and preferences reverted to default as your Library folder, including the Preferences, Accounts, Saved Application state, and other, are now encrypted.
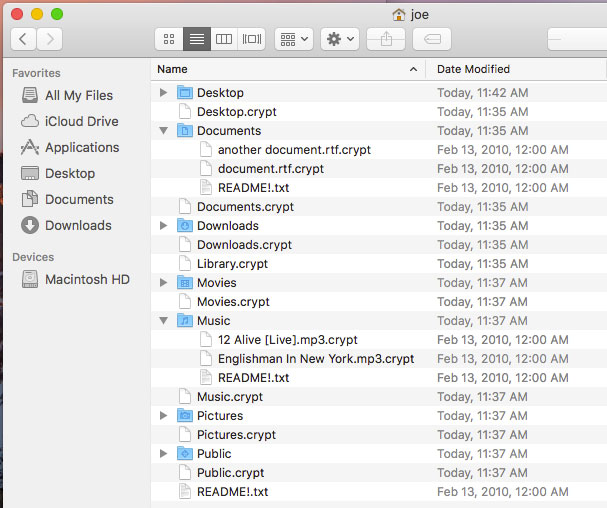
Encrypted contents of the User folder
Patcher changes the modification date of the encrypted files to February 13, 2010, for reasons unknown at this time.
Should Mac Users be Concerned?
While this ransomware was currently only found on a BitTorrent site, it could have posed as a fake Flash Player update or other delivery mechanism, thus able to reach a far greater audience. The ransomware is very basic and makes no attempts to hide itself or stay alive after reboots, but if it makes its way onto your Mac and gets a chance to run, it will thoroughly ruin your week. The torrent file carrying the ransomware was found on two BitTorrent sites and appears to have no active seeds, so it cannot be downloaded at the time of writing this article, slightly minimizing the risk. However, Patcher may be hiding in other places not yet discovered.
How to Tell if Your Mac is Infected
If you see files on your desktop or any other folder in your user directory with a .crypt extension, along with text files with names such as “README.txt,” “README_.txt,” “README-!.txt,” “README!!.txt,” “DECRYPT!.txt,” “HOW_TO_DECRYPT_!.txt” and “DECRYPT_!.txt,” your Mac probably fell victim to Filecoder.
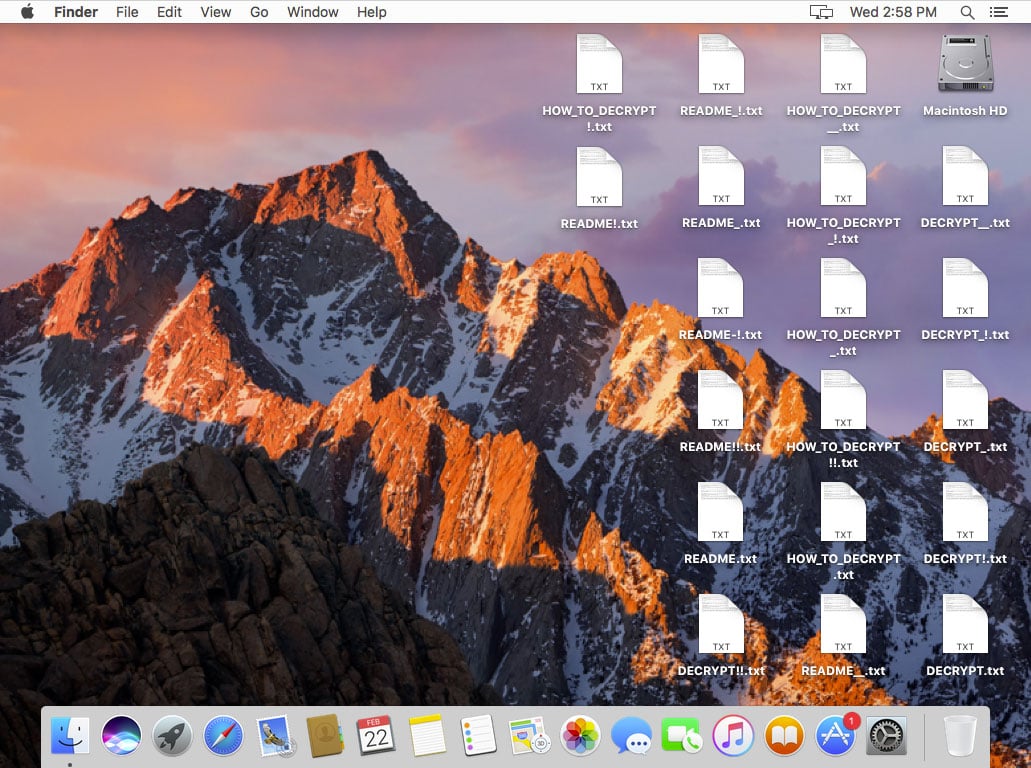
Clear signs your Mac was hit by Patcher
How to Protect Yourself from Patcher Ransomware
Unfortunately, malware is no surprise when downloading software from BitTorrent sources, so a surefire way to protect yourself from Patcher ransomware is to only get software directly from the source, such as the App Store or from the vendor’s official website. (Yup, this means you gotta pay for it if the software isn’t free.)
Furthermore, Apple has pushed an update to its XProtect anti-virus signatures to version 2089 on Mavericks, Yosemite, El Capitan, and Sierra, detecting some components of this threat as OSX.Findzip.A. However, Apple appears to miss the prova occurrence or any iteration that can modify the README.txt name. During our testing, running the Patcher application does not generate a GateKeeper warning nor does it ask for a password.
Users of Intego VirusBarrier with up-to-date malware definitions can detect all of the components of the ransomware, identified as OSX/Filecoder and OSX/Filecoder.fs, and block it if it makes its way onto your system.
Manually removing Patcher is as simple as deleting the Adobe Premiere CC 2017 or Office 2016 patcher applications. In this case, it is far more important to keep Patcher from ever getting on your system. There are no other files to delete, and a backup of your data will have to be restored as your user folder is now fully encrypted. This scenario can be seen as complete data loss and highlights the importance of having a solid and smart backup strategy.
The best way to protect yourself from ransomware is to plan ahead, before disaster strikes, and we therefore encourage you to have a look our guide to help you stay safe from ransomware: A Layman’s Guide to Ransomware Protection.
via: intego




Leave a Reply