A security researcher has released a tool that allows victims of the BadBlock ransomware to decrypt their encrypted files for free.
On Thursday, Lawrence Abrams of Bleeping Computer published an article about the crypto-ransomware variant.
In it, he does not withhold his disgust for the malware. He describes BadBlock as “poorly coded and horribly designed” because it not only encrypts a user’s files but also adversely affects a user’s machine:
“Unlike almost all other ransomware infections, BadBlock will not only encrypt your data files, but it will also encrypt the executables on your computer, including important Windows system files…. This means that if you reboot your computer after BadBlock encrypts your machine, you will find that the computer… no longer starts. This is because required executables have been encrypted….”
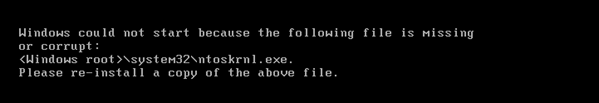
That’s not the only difference separating BadBlock from other crypto-malware variants.
As soon as ransomware begins encrypting a user’s files, it will display a message notifying them that their computer has been infected. Users can leverage that information to access the Task Manager and terminate “badransom.exe,” which shuts down the encryption process before it has time to finish. Doing so does not restore access to any files encrypted by the ransomware, however.
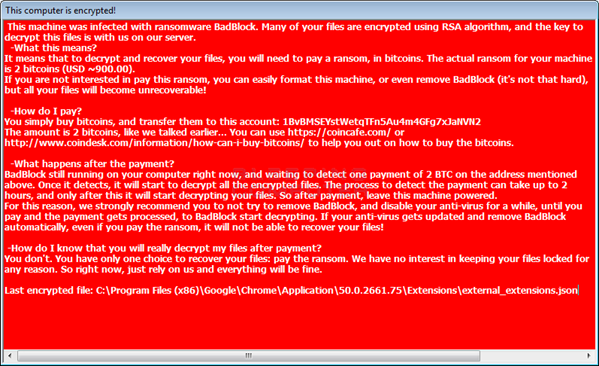
Fortunately, for those users with encrypted files, there is now hope.
Security researcher Fabian Wosar of Emisoft has released a tool that allows victims affected by BadBlock to decrypt their files for free.
After downloading the decryptor (available here), a user needs to drag an encrypted file and an unencrypted version of that same file (or of a file with the exact same format) onto the utility.
The decryptor will use those files to create a decryption key, which the victim can then use to decrypt all of their remaining files.
To avoid a ransomware infection at the hands of BadBlock and other variants, users should avoid clicking on suspicious links and email attachments, install an anti-virus solution on their computers, and implement software patches as soon as they become available.
For more ransomware prevention tips, please click here.
You can also learn more about ransomware in general here.
Via: tripwire




Leave a Reply